Threats, Vulnerabilities, and Attacks
... TCP/IP is arguably the single most important computer networking technology. The Internet and most home networks support TCP/IP as the "language" computers use to find and connect with each other. Back ...
... TCP/IP is arguably the single most important computer networking technology. The Internet and most home networks support TCP/IP as the "language" computers use to find and connect with each other. Back ...
Appendix *J* - Credit Plus
... configuring auto updates and installing new anti-Spyware definition files weekly, at a minimum. If your company’s computers have unfiltered or unblocked access to the Internet (which prevents access to some known problematic sites), then it is recommended that anti-Spyware scans be completed more fr ...
... configuring auto updates and installing new anti-Spyware definition files weekly, at a minimum. If your company’s computers have unfiltered or unblocked access to the Internet (which prevents access to some known problematic sites), then it is recommended that anti-Spyware scans be completed more fr ...
Chapter 14 Network Security - Northern Arizona University
... the same expectation of privacy when sending e-mail as they do when sending a letter through the postal service. • A more accurate expectation would be to assume that the email is like a postcard that can be read by anyone who handles it during its journey from sender to recipient. • They often trav ...
... the same expectation of privacy when sending e-mail as they do when sending a letter through the postal service. • A more accurate expectation would be to assume that the email is like a postcard that can be read by anyone who handles it during its journey from sender to recipient. • They often trav ...
Chapter 14 Network Security
... the same expectation of privacy when sending e-mail as they do when sending a letter through the postal service. • A more accurate expectation would be to assume that the email is like a postcard that can be read by anyone who handles it during its journey from sender to recipient. • They often trav ...
... the same expectation of privacy when sending e-mail as they do when sending a letter through the postal service. • A more accurate expectation would be to assume that the email is like a postcard that can be read by anyone who handles it during its journey from sender to recipient. • They often trav ...
file - ScholarSphere
... effective their protection strategies are? In this study we are attempting to gather data from chief security officers and network administrators on what technical security measures they have implemented to protect their digital assets, what security policies they have initiated to support those pra ...
... effective their protection strategies are? In this study we are attempting to gather data from chief security officers and network administrators on what technical security measures they have implemented to protect their digital assets, what security policies they have initiated to support those pra ...
POST MASTER DEGREE IN SECURITY IN COMPUTER SYSTEMS
... Explore low level bits in Intel Edison board The goal of this project is to better understand intel Edison board. Edison is a module that contains a dual core atom processor (running linux) and a quark x86 micorcontroller (running a proprietary kernel). This platform is designed for IoT applications ...
... Explore low level bits in Intel Edison board The goal of this project is to better understand intel Edison board. Edison is a module that contains a dual core atom processor (running linux) and a quark x86 micorcontroller (running a proprietary kernel). This platform is designed for IoT applications ...
Essential Computer Concepts - MCST-CS
... • Identify the hardware and software that are used for data communications and to establish a network connection • Explain how Internet access, email, and the World Wide Web affect the use of computers • Describe potential security threats to computers and protection methods • Discuss the types of s ...
... • Identify the hardware and software that are used for data communications and to establish a network connection • Explain how Internet access, email, and the World Wide Web affect the use of computers • Describe potential security threats to computers and protection methods • Discuss the types of s ...
Campus Network Usage Policy
... and antivirus software installed. (7) All computer servers located within the University must receive permission from the Computer Center before they can be set up, and upon approval the servers will be assigned physical IP addresses and publicly accessible host names by the Computer Center. (8) Oth ...
... and antivirus software installed. (7) All computer servers located within the University must receive permission from the Computer Center before they can be set up, and upon approval the servers will be assigned physical IP addresses and publicly accessible host names by the Computer Center. (8) Oth ...
Report: Intrusion Detection Systems
... Users Behave in a Consistent Manner Behaviour can be Summarised in a Profile. Profile can be generated by Advanced ...
... Users Behave in a Consistent Manner Behaviour can be Summarised in a Profile. Profile can be generated by Advanced ...
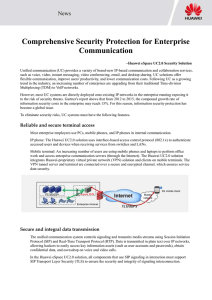
Comprehensive Security Protection for
... Multiplexing (TDM) to VoIP networks. However, most UC systems are directly deployed onto existing IP networks in the enterprise running exposing it to the risk of security threats. Gartner's report shows that from 2012 to 2015, the compound growth rate of information security costs in the enterprise ...
... Multiplexing (TDM) to VoIP networks. However, most UC systems are directly deployed onto existing IP networks in the enterprise running exposing it to the risk of security threats. Gartner's report shows that from 2012 to 2015, the compound growth rate of information security costs in the enterprise ...
NT Security Overview
... organization will have access to the network. In most businesses or organizations there are employees, staff, management and officers. Some can be trusted to access all of the network and others do not have the trust level to access any of the network. The administrator must decide who has access an ...
... organization will have access to the network. In most businesses or organizations there are employees, staff, management and officers. Some can be trusted to access all of the network and others do not have the trust level to access any of the network. The administrator must decide who has access an ...
Day 2
... • All cables run from the computers to a central location where a hub is located • The hub either resends the message to all the computers (broadcast star network) or only to the destination computer (switched star network) • We use a star topology here at Mercer in ...
... • All cables run from the computers to a central location where a hub is located • The hub either resends the message to all the computers (broadcast star network) or only to the destination computer (switched star network) • We use a star topology here at Mercer in ...
Overview on the Current Policy Trends in Robotics and AI in JAPAN
... Issue-driven Approach instead of Discipline-oriented Approach ...
... Issue-driven Approach instead of Discipline-oriented Approach ...
Call for Papers: HotPlanet 2015 6th International Workshop on Hot
... September 7, 2015, Paris In Conjunction with ACM MobiCom 2015 th ...
... September 7, 2015, Paris In Conjunction with ACM MobiCom 2015 th ...
Data Confidentiality
... make it something others can’t guess – not personal make sure no one is looking when you type it in ...
... make it something others can’t guess – not personal make sure no one is looking when you type it in ...
DRAFT DRAFT DRAFT Terremark Worldwide (NASDAQ:TMRK) is a
... Based on other factors, the IP address appears to be legitimate traffic from authorized business processes and was provided to QNA for confirmation. Several advanced analysis techniques were used to reduce the massive amount of traffic data in a process known as ‘data reduction'. The ‘data reduction ...
... Based on other factors, the IP address appears to be legitimate traffic from authorized business processes and was provided to QNA for confirmation. Several advanced analysis techniques were used to reduce the massive amount of traffic data in a process known as ‘data reduction'. The ‘data reduction ...
Operating Systems 4
... protect the computer’s resources from any unauthorized access. ◦ Establishing accounts for each user by the administrator (username, password and privileges) ◦ The OS use this information during each login procedure. ◦ The administrator(highly privileged) is able to monitor activity within the compu ...
... protect the computer’s resources from any unauthorized access. ◦ Establishing accounts for each user by the administrator (username, password and privileges) ◦ The OS use this information during each login procedure. ◦ The administrator(highly privileged) is able to monitor activity within the compu ...
Cybersecurity and Information Assurance PPT
... To guard against sniffing, make sure attacker cannot access a legitimate communication stream ...
... To guard against sniffing, make sure attacker cannot access a legitimate communication stream ...
Tobias Herber (530) 723-6691
... - Created customized Windows 7 images and scripts for workstation deployment - Administered Windows 2003-2012, CentOS, and vSphere ESXi servers - Created custom solution for legacy apps using Windows XP Mode - Set up IT infrastructure in new building, including a dual server rack, 12 physical server ...
... - Created customized Windows 7 images and scripts for workstation deployment - Administered Windows 2003-2012, CentOS, and vSphere ESXi servers - Created custom solution for legacy apps using Windows XP Mode - Set up IT infrastructure in new building, including a dual server rack, 12 physical server ...
UTG CPS (Computer Science) Major and Minor Brief Description
... possess a strong background in both Computer Science theory and practical applications. To help fill this urgent need, in the 2006-2007 school year The University of The Gambia (UTG) will begin offering a Bachelor's in Science (BSc) with a major or minor in Computer Science (CPS). The UTG CPS major ...
... possess a strong background in both Computer Science theory and practical applications. To help fill this urgent need, in the 2006-2007 school year The University of The Gambia (UTG) will begin offering a Bachelor's in Science (BSc) with a major or minor in Computer Science (CPS). The UTG CPS major ...
procedure name - Siskiyou Central Credit Union
... o They may not be used to send communications or material that defames or disparages an individual, Credit Union, or business. o They may not be used to conduct personal business. Solicitations, offers to buy and sell goods or services, and other personal messages to groups are not an appropriate us ...
... o They may not be used to send communications or material that defames or disparages an individual, Credit Union, or business. o They may not be used to conduct personal business. Solicitations, offers to buy and sell goods or services, and other personal messages to groups are not an appropriate us ...