Computers: Tools for an Information Age
... recovery plans, and security legislation Describe in general terms how viruses work, the damage they can cause, and procedures used to prevent this damage Explain the threats to personal privacy posed by computers and the Internet. Describe actions you can take to maximize your privacy Copyright © 2 ...
... recovery plans, and security legislation Describe in general terms how viruses work, the damage they can cause, and procedures used to prevent this damage Explain the threats to personal privacy posed by computers and the Internet. Describe actions you can take to maximize your privacy Copyright © 2 ...
AxxonSoft and Quantum Create a Powerful Solution
... have created a joint storage solution that effectively manages the ever-increasing data management requirements of today’s surveillance landscape, using Quantum’s multi-tier storage platform and AxxonSoft’s physical security information management (PSIM) software platform. This joint offering delive ...
... have created a joint storage solution that effectively manages the ever-increasing data management requirements of today’s surveillance landscape, using Quantum’s multi-tier storage platform and AxxonSoft’s physical security information management (PSIM) software platform. This joint offering delive ...
Case Study - SELECOM - Optirep
... To insure underground tourism protection, but also to guarantying personal security during interventions, Ariege country council entrusted Selecom for the supply, the installation and the commissioning of a new system of communication, relaying the indoor telephone network of Niaux Cave, and especia ...
... To insure underground tourism protection, but also to guarantying personal security during interventions, Ariege country council entrusted Selecom for the supply, the installation and the commissioning of a new system of communication, relaying the indoor telephone network of Niaux Cave, and especia ...
TrendMicro Titanium - A New Concept in Security by Ira Wilsker
... This lack of frequent signature file updating may have been an acute disadvantage with earlier security products, where failure to update frequently would leave the computer ...
... This lack of frequent signature file updating may have been an acute disadvantage with earlier security products, where failure to update frequently would leave the computer ...
User Behavior based Anomaly Detection for Cyber
... Fusion of data from multiple sources is generating new information from existing data. Now users can access any information from inside or outside of the organization very easily. It helps to increase the user productivity and knowledge shared within the organization. But this leads to a new area of ...
... Fusion of data from multiple sources is generating new information from existing data. Now users can access any information from inside or outside of the organization very easily. It helps to increase the user productivity and knowledge shared within the organization. But this leads to a new area of ...
TNS03%20Introduction%20to%20Network%20Security
... Appears to be benign (良好) software but secretly downloading a virus or other malware. For a Trojan horse to spread, you must invite these programs onto your computers. For example, by opening an email attachment or downloading and running a file from the Internet. ...
... Appears to be benign (良好) software but secretly downloading a virus or other malware. For a Trojan horse to spread, you must invite these programs onto your computers. For example, by opening an email attachment or downloading and running a file from the Internet. ...
System Administration
... Access Controls - specific access controls can include restrictions on: • Locations from which a user can log on to the system or access its resources. • Days/times when access is granted or denied. • The ability to read, write, create and delete directories and files. • The ability to execute progr ...
... Access Controls - specific access controls can include restrictions on: • Locations from which a user can log on to the system or access its resources. • Days/times when access is granted or denied. • The ability to read, write, create and delete directories and files. • The ability to execute progr ...
How UTM Solutions Provide the Most Complete
... track a user's personal information and pass it on to third parties without the user's authorization or knowledge. ...
... track a user's personal information and pass it on to third parties without the user's authorization or knowledge. ...
Chapter 2: Introduction to Microprocessor
... It is composed of collection of files that are linked in such a way that information from one of the files may be combined with information from other files so that a user may receive the exact required information. ...
... It is composed of collection of files that are linked in such a way that information from one of the files may be combined with information from other files so that a user may receive the exact required information. ...
Network Security
... Proxy server: implemented to improve performance by filtering requests Authentication: passwords should be updated biweekly Physical security: ...
... Proxy server: implemented to improve performance by filtering requests Authentication: passwords should be updated biweekly Physical security: ...
The wild world of malware: Keeping your
... described above can identify a huge majority of the malware attempting to enter a company’s network. This includes attacks that involve spam email, phishing (fake) websites, and “drive-by downloads” that inject malware during a visit to a seemingly safe website. Each of these methods of infection us ...
... described above can identify a huge majority of the malware attempting to enter a company’s network. This includes attacks that involve spam email, phishing (fake) websites, and “drive-by downloads” that inject malware during a visit to a seemingly safe website. Each of these methods of infection us ...
Click here to access the presentation.
... − Modular application framework can be utilized to develop entire new applications. − 3rd party developers have added/extended applications ...
... − Modular application framework can be utilized to develop entire new applications. − 3rd party developers have added/extended applications ...
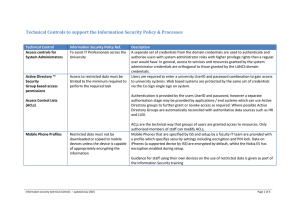
Technical Controls to support the Information
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
Principal Security Engineer– PAE4IT A. PRIMARY ROLE Working
... required. Practical experience with one or more relational database packages is required. A demonstrated ability to apply security tools in small- and large-scale vulnerability assessments (vulnerability scanners, password cracking tools, etc.) is required. A demonstrated ability to clearly and effe ...
... required. Practical experience with one or more relational database packages is required. A demonstrated ability to apply security tools in small- and large-scale vulnerability assessments (vulnerability scanners, password cracking tools, etc.) is required. A demonstrated ability to clearly and effe ...
EHLANZENI DISTRICT MUNICIPALITY INTRUSION DETECTION
... protect resources and data on the organizational network. It provides guidelines about intrusion detection implementation of the organizational networks and hosts along with associated roles and responsibilities. This policy is designed both to protect the confidentiality of any data that may be sto ...
... protect resources and data on the organizational network. It provides guidelines about intrusion detection implementation of the organizational networks and hosts along with associated roles and responsibilities. This policy is designed both to protect the confidentiality of any data that may be sto ...
FootPrinting - PSU
... of tools and techniques. The profile usually includes detailed information about IP addresses and blocks, range of domain names, remote access, intranet structure, systems connected to the Internet …etc. ...
... of tools and techniques. The profile usually includes detailed information about IP addresses and blocks, range of domain names, remote access, intranet structure, systems connected to the Internet …etc. ...
Discovering Computers 2006
... and use of information about them Difficult to maintain today because data is stored online Employee monitoring is using computers to observe employee computer use Legal for employers to use monitoring software programs ...
... and use of information about them Difficult to maintain today because data is stored online Employee monitoring is using computers to observe employee computer use Legal for employers to use monitoring software programs ...
Access Security Requirements
... vigilantly checking or configuring auto updated and installing new virus definition files. 2.4 Implement and follow current best security practices for computer anti-Spyware scanning services and procedures: Use, implement and maintain a current, commercially available computer anti-Spyware scanni ...
... vigilantly checking or configuring auto updated and installing new virus definition files. 2.4 Implement and follow current best security practices for computer anti-Spyware scanning services and procedures: Use, implement and maintain a current, commercially available computer anti-Spyware scanni ...
Computer Science or Software Engineering?
... Computer Science or Software Engineering? Nearly three out of four new science or engineering jobs in the United States will be in computing, according to the Bureau of Labor Statistics. But what kind of computing job is right for you? If you are interested in majoring in either computer science or ...
... Computer Science or Software Engineering? Nearly three out of four new science or engineering jobs in the United States will be in computing, according to the Bureau of Labor Statistics. But what kind of computing job is right for you? If you are interested in majoring in either computer science or ...
Cyber-Terrorism
... • The internet is a powerful tool to influence people. • Terrorist groups are increasingly using the internet to spread propaganda, radicalising and recruiting individuals by indoctrinating them with extremist ideologies. ...
... • The internet is a powerful tool to influence people. • Terrorist groups are increasingly using the internet to spread propaganda, radicalising and recruiting individuals by indoctrinating them with extremist ideologies. ...
Workstar iGuard
... 3. Contactless SmartCard: With this feature, your workforce can gain access to the iGuard faster and smarter, by using the Philips Mifare Contactless Smart Card. Each user would have his / her own smart card, which stores the user information including the name, company & branch code, and the finger ...
... 3. Contactless SmartCard: With this feature, your workforce can gain access to the iGuard faster and smarter, by using the Philips Mifare Contactless Smart Card. Each user would have his / her own smart card, which stores the user information including the name, company & branch code, and the finger ...
The Top Ten of Security
... – The “reading room” for SANS, a large computer security training organization. ...
... – The “reading room” for SANS, a large computer security training organization. ...
Fundamentals of Computer Security
... Distributed Systems[2] Intelligent Security System for Computers users’ activity monitoring Online and off-line monitoring allowing to detect anomalies and irregularities in user behavior. On-line monitoring is carried in real time, and is used to predict user actions (use neural networks) Off ...
... Distributed Systems[2] Intelligent Security System for Computers users’ activity monitoring Online and off-line monitoring allowing to detect anomalies and irregularities in user behavior. On-line monitoring is carried in real time, and is used to predict user actions (use neural networks) Off ...