... Dr. Khalid Al-Biyari said that by concentrating on system design projects, more emphasis on system integration using available components is needed Mr. Ahmad Ashadawi stated that there is no data research, and there is an urgent need to develop top most quality and capability access to massive d ...
Computer and System Logging Policy
... 3. Scope This policy applies to all [LEP] staff that create, deploy, or support application and system software. ...
... 3. Scope This policy applies to all [LEP] staff that create, deploy, or support application and system software. ...
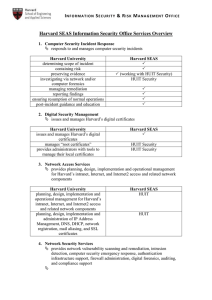
Harvard SEAS Information Security Office Services Overview
... may indicate computer attack, compromised machine, data breach, etc Harvard University monitors network traffic in real-time aggregates and correlates security data from network and system infrastructure ...
... may indicate computer attack, compromised machine, data breach, etc Harvard University monitors network traffic in real-time aggregates and correlates security data from network and system infrastructure ...
6.01 RCNET Module
... and it is now a commonly available means of connecting industrial electronic devices. Modbus enables communication among many devices connected to the same network, for example a system that measures temperature and humidity and communicates the results to a computer. Remote Terminal Unit or sometim ...
... and it is now a commonly available means of connecting industrial electronic devices. Modbus enables communication among many devices connected to the same network, for example a system that measures temperature and humidity and communicates the results to a computer. Remote Terminal Unit or sometim ...
Database Administrator
... Experience and knowledge in supporting application system development life cycle. Responsible for data dictionary backup and recovery. Responsible for definition of standards of data dictionaries. May program dictionary analysis and maintenance software. Perform performance tuning. Monit ...
... Experience and knowledge in supporting application system development life cycle. Responsible for data dictionary backup and recovery. Responsible for definition of standards of data dictionaries. May program dictionary analysis and maintenance software. Perform performance tuning. Monit ...
BSc Computer Science Frequently Asked QuestionsWhere
... Where are the jobs? There is a strong demand for Computer Science graduates nationally and internationally from both SMEs and multinationals. A degree in Computer Science is recognised all over the globe. Many of our graduates work in the UK, Europe, the US as well as in Ireland. Is the degree a ful ...
... Where are the jobs? There is a strong demand for Computer Science graduates nationally and internationally from both SMEs and multinationals. A degree in Computer Science is recognised all over the globe. Many of our graduates work in the UK, Europe, the US as well as in Ireland. Is the degree a ful ...
Information Security and its Implications on Everyday
... Wireless technology No Physical network boundaries ...
... Wireless technology No Physical network boundaries ...
Acceptable User Policy
... in this document and to investigate or prevent illegal activities being committed over our network. Cybersmart reserves the right to monitor user and network traffic for site security purposes and prevent any unauthorised attempts to tamper with our site or cause damage to our property. Cybersmart r ...
... in this document and to investigate or prevent illegal activities being committed over our network. Cybersmart reserves the right to monitor user and network traffic for site security purposes and prevent any unauthorised attempts to tamper with our site or cause damage to our property. Cybersmart r ...
Network Security - University of Hull
... The component steps that enable an activity Can be software components or human procedures ...
... The component steps that enable an activity Can be software components or human procedures ...
presentation
... units in a manner that requires the user to have little or no knowledge of the unique characteristics of those units". ...
... units in a manner that requires the user to have little or no knowledge of the unique characteristics of those units". ...
Data and Applications Security - The University of Texas at Dallas
... The University of Texas at Dallas ...
... The University of Texas at Dallas ...
Network Security
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
BIO-ELECTRO-INFO TECHNOLOGIES TO COMBAT TERRORISM
... Protection Center (NIPC) confirmed that Chinese hackers had been active in launching Web defacing and distributed-denial-of-service attacks on the Department of the Interior's National Business Center, the U.S. Geological Survey's site and Pacific Bell ...
... Protection Center (NIPC) confirmed that Chinese hackers had been active in launching Web defacing and distributed-denial-of-service attacks on the Department of the Interior's National Business Center, the U.S. Geological Survey's site and Pacific Bell ...
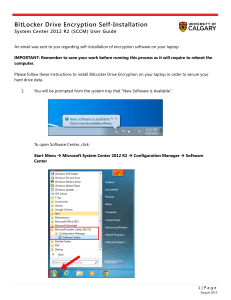
BitLocker Drive Encryption Self
... System Center 2012 R2 (SCCM) User Guide An email was sent to you regarding self-installation of encryption software on your laptop. IMPORTANT: Remember to save your work before running this process as it will require to reboot the computer. Please follow these instructions to install BitLocker Drive ...
... System Center 2012 R2 (SCCM) User Guide An email was sent to you regarding self-installation of encryption software on your laptop. IMPORTANT: Remember to save your work before running this process as it will require to reboot the computer. Please follow these instructions to install BitLocker Drive ...
Network Security
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
Certifications authenticate Blancco´s high standards
... and Windows Mobile). TÜV-SÜD also endorses Blancco for storage media, noting that it is “appropriate to safely and irrecoverably erase the data on all popular types of hard drives.” The Norwegian National Security Authority The Norwegian National Security Authority (NSM) approved Blancco HMG Softwar ...
... and Windows Mobile). TÜV-SÜD also endorses Blancco for storage media, noting that it is “appropriate to safely and irrecoverably erase the data on all popular types of hard drives.” The Norwegian National Security Authority The Norwegian National Security Authority (NSM) approved Blancco HMG Softwar ...
19-DS-05-2016_OZGUR
... management of the international goods supply chain trade movements • SEC-19-BES-2016: Data fusion for maritime security applications • DS-05-2016: EU Cooperation and International Dialogues in Cybersecurity and Privacy Research and Innovation • DS-06-2017: Cryptography • DS-08-2017: Privacy, Data Pr ...
... management of the international goods supply chain trade movements • SEC-19-BES-2016: Data fusion for maritime security applications • DS-05-2016: EU Cooperation and International Dialogues in Cybersecurity and Privacy Research and Innovation • DS-06-2017: Cryptography • DS-08-2017: Privacy, Data Pr ...
A Brief Overview of VoIP Security By John McCarron Voice of
... of the conversations. It is relatively easy and simple. There are many free network analyzer, sniffers and packet capture tools that can convert VoIP traffic to wave files (Roberts 2005). This allows you to save the files and play them back on a computer. Vomit, Voice over Misconfigured Internet Tel ...
... of the conversations. It is relatively easy and simple. There are many free network analyzer, sniffers and packet capture tools that can convert VoIP traffic to wave files (Roberts 2005). This allows you to save the files and play them back on a computer. Vomit, Voice over Misconfigured Internet Tel ...
Securing the Network - Austin Community College
... Sophisticated attack tools and open networks continue to generate an increased need for network security policies and infrastructure to protect organizations from internally and externally based attacks. Organizations must balance network security needs against ebusiness processes, legal issues, and ...
... Sophisticated attack tools and open networks continue to generate an increased need for network security policies and infrastructure to protect organizations from internally and externally based attacks. Organizations must balance network security needs against ebusiness processes, legal issues, and ...
Slide 1
... Multithreading – parts of the same application can run as separate tasks (video and image processing) Multiprocessing – when a computer has multiple CPUs / Cores, a single running application can thread across cores. ...
... Multithreading – parts of the same application can run as separate tasks (video and image processing) Multiprocessing – when a computer has multiple CPUs / Cores, a single running application can thread across cores. ...
Hands-On Ethical Hacking and Network Security
... company’s internal network and the Internet is dangerous – It leaves the company open to attack if a hacker compromises the firewall ...
... company’s internal network and the Internet is dangerous – It leaves the company open to attack if a hacker compromises the firewall ...
Support: Ticket, Process, and Expectations
... the hard disk will show up just like another hard disk when connected and unlocked via the password). Tutorial available at http://www.trucrypt.org/docs/?s=tutorial Great approach for home computers as it provides a location for all work files to be placed in an encrypted "drive" and when the comp ...
... the hard disk will show up just like another hard disk when connected and unlocked via the password). Tutorial available at http://www.trucrypt.org/docs/?s=tutorial Great approach for home computers as it provides a location for all work files to be placed in an encrypted "drive" and when the comp ...
Network and Systems - University of Glasgow
... The Universal Access and Information Security working groups have produced a set of draft Policies and Guidelines for consultation These are not meant to place unnecessary barriers in the way of users doing their legitimate work They are not tablets of stone but rather starting points that will evol ...
... The Universal Access and Information Security working groups have produced a set of draft Policies and Guidelines for consultation These are not meant to place unnecessary barriers in the way of users doing their legitimate work They are not tablets of stone but rather starting points that will evol ...