security threats: a guide for small and medium
... enterprises (SMEs) are particularly hit hard when either one or both of these business requirements suffer. Data leakage, down-time and reputation loss can easily turn away new and existing customers if such situations are not handled appropriately and quickly. This may, in turn, impact on the compa ...
... enterprises (SMEs) are particularly hit hard when either one or both of these business requirements suffer. Data leakage, down-time and reputation loss can easily turn away new and existing customers if such situations are not handled appropriately and quickly. This may, in turn, impact on the compa ...
New Law Requires Businesses in California to Report Electronic Break-Ins
... In the wake of a security breach at one of its own data centers, the State of California has enacted legislation that requires businesses to disclose computer security breaches. The stimulus for the legislation occurred in April 2002, when California’s Steven P. Teale data center in Rancho Cordova s ...
... In the wake of a security breach at one of its own data centers, the State of California has enacted legislation that requires businesses to disclose computer security breaches. The stimulus for the legislation occurred in April 2002, when California’s Steven P. Teale data center in Rancho Cordova s ...
Chapter1 Introduction to Computers Computer : is an electronic
... With the handheld game console, the controls, screen and speakers are built into the device. Servers : A server controls access to the hardware, software, and other resources on a network -Provides a centralized storage area for programs, data, and information. -In many cases, one server accesses da ...
... With the handheld game console, the controls, screen and speakers are built into the device. Servers : A server controls access to the hardware, software, and other resources on a network -Provides a centralized storage area for programs, data, and information. -In many cases, one server accesses da ...
Network Security For Distributed Simulation Systems
... 3: MS encrypts data with its private key and returns data to network ...
... 3: MS encrypts data with its private key and returns data to network ...
Presentation Prepared By: Raghda Zahran
... on flawed assumptions or unverifiable data Harden the target; place multiple barriers between the adversary and enterprise information systems ...
... on flawed assumptions or unverifiable data Harden the target; place multiple barriers between the adversary and enterprise information systems ...
computer security - GH Raisoni Polytechnic, Nagpur
... A message is to be transferred from one party to another via Internet. Sender & receiver are principals of transaction and must cooperate for exchange to take place. An information channel is established by defining a route through Internet from source to destination with the help of communication p ...
... A message is to be transferred from one party to another via Internet. Sender & receiver are principals of transaction and must cooperate for exchange to take place. An information channel is established by defining a route through Internet from source to destination with the help of communication p ...
Phoenix SIEM (Security Information and Event
... more than 10 years experience in cyber security software engineering. Some of the notable organizations I have worked for include BAE Systems, Rapid 7 and 3M. At BAE Systems I worked with NetReveal and Vuma, at Rapid 7 I worked with Nexpose and Metasploit, ...
... more than 10 years experience in cyber security software engineering. Some of the notable organizations I have worked for include BAE Systems, Rapid 7 and 3M. At BAE Systems I worked with NetReveal and Vuma, at Rapid 7 I worked with Nexpose and Metasploit, ...
Chp. 8 - Cisco Networking Academy
... request to many computer systems on the Internet, with the source address modified to be the targeted computer system. The computer systems that receive the request respond and all the requests ...
... request to many computer systems on the Internet, with the source address modified to be the targeted computer system. The computer systems that receive the request respond and all the requests ...
Network Security Chapter 14
... ____ 15. A ____ policy is designed to produce a standardized framework for classifying information assets. a. classification of information c. service level agreement b. change management d. disposal and destruction ____ 16. ____ refers to a methodology for making changes and keeping track of those ...
... ____ 15. A ____ policy is designed to produce a standardized framework for classifying information assets. a. classification of information c. service level agreement b. change management d. disposal and destruction ____ 16. ____ refers to a methodology for making changes and keeping track of those ...
William Stallings, Cryptography and Network Security 3/e
... The outside router advertises only the existence of the screened subnet to the Internet; therefore, the internal network is invisible to the Internet. Similarly, the inside router advertises only the existence of the screened subnet to the internal network; therefore, the systems on the inside netwo ...
... The outside router advertises only the existence of the screened subnet to the Internet; therefore, the internal network is invisible to the Internet. Similarly, the inside router advertises only the existence of the screened subnet to the internal network; therefore, the systems on the inside netwo ...
Faculty of Correspondence, Evening and Distance
... technologies in economics - Software for information technologies - Information technologies and control in engineering ...
... technologies in economics - Software for information technologies - Information technologies and control in engineering ...
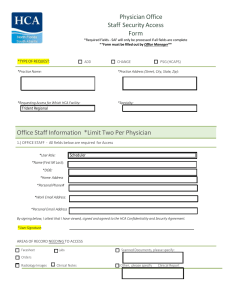
Physician Office Staff Security Access Form Office Staff Information
... I will act in accordance with the Company’s Code of Conduct at all times during my relationship with the Company. I understand that I should have no expectation of privacy when using Company information systems. The Company may log, access, review, and otherwise utilize information stored on or pass ...
... I will act in accordance with the Company’s Code of Conduct at all times during my relationship with the Company. I understand that I should have no expectation of privacy when using Company information systems. The Company may log, access, review, and otherwise utilize information stored on or pass ...
Distributed Data Dissemination Server
... Attribute based data discovery Multi-Server capability Client-side libraries available in C, C++, and Java ...
... Attribute based data discovery Multi-Server capability Client-side libraries available in C, C++, and Java ...
Distributed System Concepts and Architectures
... assigned a sensitivity label. The labels are used as the basis for mandatory access control decisions. ...
... assigned a sensitivity label. The labels are used as the basis for mandatory access control decisions. ...
Next Generation Security Operation Center for NCHC
... – Simulating vulnerable systems for network threats – Collecting malware samples and suspicious exploit traffic for further research – Analyzing Malware behavior for potential threats ...
... – Simulating vulnerable systems for network threats – Collecting malware samples and suspicious exploit traffic for further research – Analyzing Malware behavior for potential threats ...
William Stallings, Cryptography and Network Security 3/e
... The function of a strong position is to make the forces holding it practically unassailable —On War, Carl Von Clausewitz ...
... The function of a strong position is to make the forces holding it practically unassailable —On War, Carl Von Clausewitz ...
Your computer
... Spoof Email (Phishing) Phishing emails are an attempt by thieves to lure you into divulging personal and financial information, for their profit. They pretend to be from well-known legitimate businesses, and increasingly look as if they actually are. They use clever techniques to induce a sense of ...
... Spoof Email (Phishing) Phishing emails are an attempt by thieves to lure you into divulging personal and financial information, for their profit. They pretend to be from well-known legitimate businesses, and increasingly look as if they actually are. They use clever techniques to induce a sense of ...
Security – A Big Question for Big Data
... Billions in opportunity costs – need web efficiencies Insecurity has doomed numerous “solutions” ...
... Billions in opportunity costs – need web efficiencies Insecurity has doomed numerous “solutions” ...
systemsprinciples2
... The power of the attacker (characterizes possible attacks) • E.g., attacker can act as an ordinary user, read any data on disk, and monitor all network traffic. ...
... The power of the attacker (characterizes possible attacks) • E.g., attacker can act as an ordinary user, read any data on disk, and monitor all network traffic. ...
Slide 1
... Experts from the US National Security Agency and government labs said America had to change the way it thought about protecting Department of Defense (DoD) computer networks. "We've got the wrong mental model here," said Dr James Peery, head of the Information Systems Analysis Centre at the Sandia N ...
... Experts from the US National Security Agency and government labs said America had to change the way it thought about protecting Department of Defense (DoD) computer networks. "We've got the wrong mental model here," said Dr James Peery, head of the Information Systems Analysis Centre at the Sandia N ...
ITC_2013_13-02
... physical world. This reality prompted the director of national intelligence, James Clapper, to tell a congressional committee “We all recognize [cyber attacks] as a profound threat to this country, to its future, to its economy, to its very being.” [7] Recent events illustrate the need to ...
... physical world. This reality prompted the director of national intelligence, James Clapper, to tell a congressional committee “We all recognize [cyber attacks] as a profound threat to this country, to its future, to its economy, to its very being.” [7] Recent events illustrate the need to ...
Database Security - University of Scranton: Computing Sciences Dept.
... Databases often store data which is sensitive in nature Incorrect data or loss of data could negatively affect business operations Databases can be used as bases to attack other systems from ...
... Databases often store data which is sensitive in nature Incorrect data or loss of data could negatively affect business operations Databases can be used as bases to attack other systems from ...
10 March 2009 - Computer Science
... these problems. We approach this problem statement from the prospective of having legitimate access to encrypted traffic for doing analysis, debugging or data collection. There are a number of systems that implement parts of the problem statement. We are looking at building a system that is easy to ...
... these problems. We approach this problem statement from the prospective of having legitimate access to encrypted traffic for doing analysis, debugging or data collection. There are a number of systems that implement parts of the problem statement. We are looking at building a system that is easy to ...