all the web without the risk
... Over 90 percent of undetected malware infects the enterprise via the Web browser.* Historically solutions have been built around the idea of 100 percent prevention either by removing vulnerabilities or detecting attacks before they are executed. Neither of these approaches has been completely effect ...
... Over 90 percent of undetected malware infects the enterprise via the Web browser.* Historically solutions have been built around the idea of 100 percent prevention either by removing vulnerabilities or detecting attacks before they are executed. Neither of these approaches has been completely effect ...
Relational Databases
... Structural dependence refers to the fact that if a file structure is changed (such as deletion or addition of a field), the related file management programs have to be modified accordingly Data dependence refers to the fact that the changes in data characteristics, such as changing a field from ...
... Structural dependence refers to the fact that if a file structure is changed (such as deletion or addition of a field), the related file management programs have to be modified accordingly Data dependence refers to the fact that the changes in data characteristics, such as changing a field from ...
Information Security in the New Millennium
... protected against accidental or deliberate modification Information must be available in a timely fashion. We must also establish and maintain the authenticity (correct attribution) of documents we create, send and receive If poor security practices allow damage to our systems, we may be subject to ...
... protected against accidental or deliberate modification Information must be available in a timely fashion. We must also establish and maintain the authenticity (correct attribution) of documents we create, send and receive If poor security practices allow damage to our systems, we may be subject to ...
Network Protocols
... capable of allowing data to be routed so suitable for both LANs and WANs (can send data for same destination through different routes so very useful. Works with different LAN technologies and is not OS dependant and because of this was chosen as the protocol used on the internet in 1983. TCP deals w ...
... capable of allowing data to be routed so suitable for both LANs and WANs (can send data for same destination through different routes so very useful. Works with different LAN technologies and is not OS dependant and because of this was chosen as the protocol used on the internet in 1983. TCP deals w ...
Torguard Ip Checker
... Torguard Ip Checker - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
... Torguard Ip Checker - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
The Great Firewall of China
... • URL Filtering • Content Filtering and Censorship • Network Traffic Analysis • Interfere Secure Connections • Record user activities • Network Security ...
... • URL Filtering • Content Filtering and Censorship • Network Traffic Analysis • Interfere Secure Connections • Record user activities • Network Security ...
45.3% of employees are aware that their workplace can be
... ■ Device used to communicate business emails: Desktop PC provided by company (46.1%); Laptop PC provided by company (37.9%); Personal smartphone (13.6%). ■ In terms of security policies in the workplace, 60.7% said “yes, we have security policies”, 31.3% said “no, we do not have policies”, and 8.0% ...
... ■ Device used to communicate business emails: Desktop PC provided by company (46.1%); Laptop PC provided by company (37.9%); Personal smartphone (13.6%). ■ In terms of security policies in the workplace, 60.7% said “yes, we have security policies”, 31.3% said “no, we do not have policies”, and 8.0% ...
Responding to Intrusions
... services. The first step once an intrusion is detected, is to immediately notify your CERT team. It is the responsibility of the CERT team to respond to the problem quickly and efficiently. The CERT team needs to neutralize the attack in order to prevent any further damages from occurring. The team ...
... services. The first step once an intrusion is detected, is to immediately notify your CERT team. It is the responsibility of the CERT team to respond to the problem quickly and efficiently. The CERT team needs to neutralize the attack in order to prevent any further damages from occurring. The team ...
Optimize Web and Application Load Balancing with Server Load
... infrastructure. Server load balancing tackles a number of requirements that are becoming progressively more important in networks. Most companies that have websites usually receive a high volume of traffic, and these are the companies that will find the best advantages with server load balancing. Se ...
... infrastructure. Server load balancing tackles a number of requirements that are becoming progressively more important in networks. Most companies that have websites usually receive a high volume of traffic, and these are the companies that will find the best advantages with server load balancing. Se ...
5th Chapter - information systems and it audit
... • Job rotation (wherever possible) • Restricted operation of operators over operator activity logs etc. • Audit trail of all operator activities and its periodical review by operations management. • Availability of documented Network operations standards and protocols to operators and periodical rev ...
... • Job rotation (wherever possible) • Restricted operation of operators over operator activity logs etc. • Audit trail of all operator activities and its periodical review by operations management. • Availability of documented Network operations standards and protocols to operators and periodical rev ...
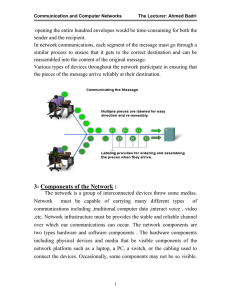
1-Introduction :
... intermediary devices. These devices use the destination host address, in conjunction with information about the network interconnections, to determine the path that messages should take through the network. Processes running on the intermediary network devices perform these functions: 1. Regenerate ...
... intermediary devices. These devices use the destination host address, in conjunction with information about the network interconnections, to determine the path that messages should take through the network. Processes running on the intermediary network devices perform these functions: 1. Regenerate ...
Attivo Networks Deception Platform Integrates with the Check Point
... and the resources needed to identify, block, and remediate threats inside the network. ...
... and the resources needed to identify, block, and remediate threats inside the network. ...
Manage security settings with Action Center
... A firewall is software or hardware that checks information coming from the Internet or a network and then either turns it away or allows it to pass through to your computer. In this way, a firewall helps prevent hackers and malicious software from gaining access to your computer. Even if you think t ...
... A firewall is software or hardware that checks information coming from the Internet or a network and then either turns it away or allows it to pass through to your computer. In this way, a firewall helps prevent hackers and malicious software from gaining access to your computer. Even if you think t ...
TMDE Web Site
... • Stable – Infrequent minor problems have been dealt with quickly • Reliable – Site off-line briefly (< 10 minutes each occurrence) 2 times in last 6 months • Secure – Strictly follows current Navy security requirements regarding access ...
... • Stable – Infrequent minor problems have been dealt with quickly • Reliable – Site off-line briefly (< 10 minutes each occurrence) 2 times in last 6 months • Secure – Strictly follows current Navy security requirements regarding access ...
Application Service Provider Security Requirements
... 1. The ASP must provide documentation of the controls for the physical and logical security of the hosted application’s infrastructure including network equipment, operating systems, applications, etc. and the maintenance and currency of those controls. 2. The ASP must provide documentation of those ...
... 1. The ASP must provide documentation of the controls for the physical and logical security of the hosted application’s infrastructure including network equipment, operating systems, applications, etc. and the maintenance and currency of those controls. 2. The ASP must provide documentation of those ...
Skating on Stilts
... – Fewer than 60% patched and updated software on a regular schedule – User name and password the most common form of login/authentication – more than three-quarters of SCADA/ICS systems are connected to an IP network or the Internet • nearly half of those admitted that these connections create unres ...
... – Fewer than 60% patched and updated software on a regular schedule – User name and password the most common form of login/authentication – more than three-quarters of SCADA/ICS systems are connected to an IP network or the Internet • nearly half of those admitted that these connections create unres ...
VirtuWind–Security in a Virtual and Programmable Industrial
... guarantee that secure communication for all interfaces (north-/south-/east/west-/bound) is possible. The communication channel between each SDN layer will be well protected (e.g., OpenFlow protocol is protected by Transport Layer Security (TLS)). Security measure techniques such as secure coding, de ...
... guarantee that secure communication for all interfaces (north-/south-/east/west-/bound) is possible. The communication channel between each SDN layer will be well protected (e.g., OpenFlow protocol is protected by Transport Layer Security (TLS)). Security measure techniques such as secure coding, de ...
Management Information Systems OUTLINE OBJECTIVES
... massive data centers that contain thousands of networked computer servers. ...
... massive data centers that contain thousands of networked computer servers. ...
Chapter 24 - William Stallings, Data and Computer
... • modifications to the logic of macro or executable files • modifications of critical system settings ...
... • modifications to the logic of macro or executable files • modifications of critical system settings ...
CNCERT/CC Annual Report 2008
... The workshop was held on 23rd March 2008 at APEC-TEL37 in Tokyo. 12 experts gave the presentations to share their experiences and skills regarding to Botnet. The workshop provided an atmosphere that encourages the sharing of knowledge and experiences of effective solutions for preventing, detecting ...
... The workshop was held on 23rd March 2008 at APEC-TEL37 in Tokyo. 12 experts gave the presentations to share their experiences and skills regarding to Botnet. The workshop provided an atmosphere that encourages the sharing of knowledge and experiences of effective solutions for preventing, detecting ...
Glenbriar TakeStock! - Glenbriar Technologies Inc.
... Complete exclusive, commercial, nontransferable, renewable three-year license from Deep-Secure Ltd. ...
... Complete exclusive, commercial, nontransferable, renewable three-year license from Deep-Secure Ltd. ...
Federal Bio
... Previously Mr. Crane was a Senior Information Security Consultant with Foundstone, a wholly owned subsidiary of McAfee, Inc. There he created and led the Information Security Management program. Service line specialties included performing risk assessments and creating risk mitigation strategies for ...
... Previously Mr. Crane was a Senior Information Security Consultant with Foundstone, a wholly owned subsidiary of McAfee, Inc. There he created and led the Information Security Management program. Service line specialties included performing risk assessments and creating risk mitigation strategies for ...