* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Cutting Edge VoIP Security Issues Color
Post-quantum cryptography wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cyberwarfare wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Information security wikipedia , lookup
Unix security wikipedia , lookup
Airport security wikipedia , lookup
Wireless security wikipedia , lookup
Cyberattack wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Mobile security wikipedia , lookup
Distributed firewall wikipedia , lookup
Security-focused operating system wikipedia , lookup
Social engineering (security) wikipedia , lookup
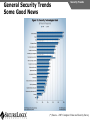
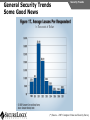
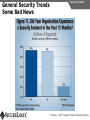
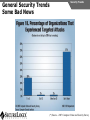
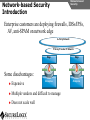
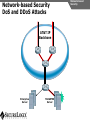
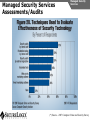
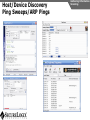
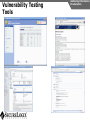
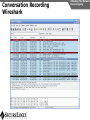
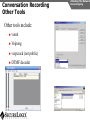
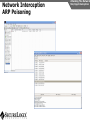
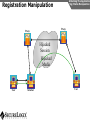
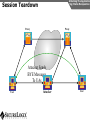
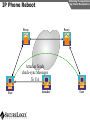
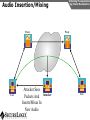
Network and VoIP Security – More Important Than Ever Mark D. Collier Chief Technology Officer SecureLogix Corporation [email protected] Outline General Security Trends Good news Bad news Going forward Network-Based Security Managed Security Services Internal Application/VoIP Security Outline General Security Trends Some Good News Security Trends Basic security measures, such as anti-virus, firewalls, and anti-spyware, are ubiquitously deployed Average losses due to security breaches are up, but down significantly from 2001 and 2002 (*) The number of incidents is down (*) Incidents are being reported at a greater rate (*) (*) Source – 2007 Computer Crime and Security Survey General Security Trends Some Good News Security Trends (*) Source – 2007 Computer Crime and Security Survey General Security Trends Some Good News Security Trends (*) Source – 2007 Computer Crime and Security Survey General Security Trends Some Good News Security Trends (*) Source – 2007 Computer Crime and Security Survey General Security Trends Some Good News Security Trends (*) Source – 2007 Computer Crime and Security Survey General Security Trends Some Bad News Security Trends (*) Source – 2007 Computer Crime and Security Survey General Security Trends Some Bad News Security Trends Signature based-detection systems are being pushed to the limit The platforms, network, and applications are getting more and more complex Attacks are becoming increasing complex Perimeter security has many issues Security funding is a small part of IT spending – no more than 10% and often less than 5% (*) Targeted attacks are increasing (*) (*) Source – 2007 Computer Crime and Security Survey General Security Trends Some Bad News Security Trends (*) Source – 2007 Computer Crime and Security Survey General Security Trends Some Bad News Security Trends (*) Source – 2007 Computer Crime and Security Survey General Security Trends Going Forward Security Trends Increased deployment of Intrusion Detection and Prevention Systems (IDSs and IPSs) Possible increase the in use of Network Admission Control (NAC) Network-Based Security solutions are available Managed Security Services solutions are available Increased focus on internal application security New applications such as Voice Over IP (VoIP) moving onto the data network Network-based Security Network-based Security Introduction Enterprise customers are deploying firewalls, IDSs/IPSs, AV, anti-SPAM on network edge 3rd Party Network Primary Provider IP Network Some disadvantages: Edge Edge Client Enterprise Client Enterprise Expensive Multiple vendors and difficult to manage Does not scale well Network-based Security Network-based Security Introduction Network-based security embeds security capability in the network 3rd Party Network AT&T IP Network VPN, Firewall, IDS, Anti-Virus, etc. Edge Edge Firewall, IDS, Anti-Virus, etc. Some advantages: Client Enterprise Leverages security capability in the network Centralized management Scales better Client Enterprise Network-based Security Advantages Network-based Security Leverages security expertise Greatly assists with threat reconnaissance Broad network visibility allows greater awareness and warning of attacks The impact of major Worm attacks are seen well in advance of when they are a threat to an enterprise The only real solution to DoS and DDoS attacks A great defense in depth approach Still may need network defense and internal security Network-based Security Network-based Security Early Detection of Attacks Web-Based Information Collection Social Engineering Reconnaissance Broad Network Mapping Service Vulnerability Exploitation Targeted Scan Scanning Password Guessing System Access Preventive Phase (Defense) AT&T Security Service Primary Emphasis DDOS Zombie Code Installation Use of Stolen Accounts for Attack System File Delete Damage Log File Changes Track Coverage Reactive Phase (Defense) Network-based Security DoS and DDoS Attacks AT&T IP Backbone Enterprise Server TARGETED Server Network-based Security Network-based Security AT&T Offerings AT&T AT&T AT&T AT&T AT&T AT&T AT&T Internet Protect® DDoS Defense My Internet Protect Private Intranet Protect Network-Based Firewalls Secure E-Mail Gateway Web Security Services Network-Based Security Platform Network-based Security Managed Security Services Introduction Managed Security Services Managed Security Services (MSS) are a viable alternative to in-house security staffing Leverage experienced staff, who are familiar with security processes and products Often can be more cost effective Eliminates the need to retain and train staff Security assessments/audits are commonly outsourced Managed Security Services Enterprise Penetration Managed Security Services (*) Source – 2007 Computer Crime and Security Survey Managed Security Services Assessments/Audits Managed Security Services (*) Source – 2007 Computer Crime and Security Survey Managed Security Services AT&T Offerings Premises-Based Firewalls Managed Intrusion Detection Endpoint Security Service Token Authentication Network-based Security Application/VoIP Security VoIP Security Introduction Despite availability of network-based security, managed services, and customer-premise edge security, securing applications is still important Voice Over IP (VoIP) is one internal application that must be secured Public Website Research Introduction Gathering Information Footprinting An enterprise website often contains a lot of information that is useful to a hacker: Organizational structure and corporate locations Help and technical support Job listings Phone numbers and extensions Public Website Research Countermeasures Gathering Information Footprinting It is difficult to control what is on your enterprise website, but it is a good idea to be aware of what is on it Try to limit amount of detail in job postings Remove technical detail from help desk web pages Google Hacking Introduction Gathering Information Footprinting Google is incredibly good at finding details on the web: Vendor press releases and case studies Resumes of VoIP personnel Mailing lists and user group postings Web-based VoIP logins Google Hacking Countermeasures Gathering Information Footprinting Determine what your exposure is Be sure to remove any VoIP phones which are visible to the Internet Disable the web servers on your IP phones There are services that can help you monitor your exposure: www.cyveilance.com ww.baytsp.com Host/Device Discovery and Identification Gathering Information Scanning Consists of various techniques used to find hosts: Ping sweeps ARP pings TCP ping scans SNMP sweeps After hosts are found, the type of device can be determined Classifies host/device by operating system Once hosts are found, tools can be used to find available network services Host/Device Discovery Ping Sweeps/ARP Pings Gathering Information Scanning Host/Device Discovery Countermeasures Gathering Information Scanning Use firewalls and Intrusion Prevention Systems (IPSs) to block ping and TCP sweeps VLANs can help isolate ARP pings Ping sweeps can be blocked at the perimeter firewall Use secure (SNMPv3) version of SNMP Change SNMP public strings Enumeration Introduction Gathering Information Enumeration Involves testing open ports and services on hosts/devices to gather more information Includes running tools to determine if open services have known vulnerabilities Also involves scanning for VoIP-unique information such as phone numbers Includes gathering information from TFTP servers and SNMP Vulnerability Testing Tools Gathering Information Enumeration Vulnerability Testing Countermeasures Gathering Information Enumeration The best solution is to upgrade your applications and make sure you continually apply patches Some firewalls and IPSs can detect and mitigate vulnerability scans TFTP Enumeration Introduction Gathering Information Enumeration Almost all phones we tested use TFTP to download their configuration files The TFTP server is rarely well protected If you know or can guess the name of a configuration or firmware file, you can download it without even specifying a password The files are downloaded in the clear and can be easily sniffed Configuration files have usernames, passwords, IP addresses, etc. in them TFTP Enumeration Countermeasures Gathering Information Enumeration It is difficult not to use TFTP, since it is so commonly used by VoIP vendors Some vendors offer more secure alternatives Firewalls can be used to restrict access to TFTP servers to valid devices SNMP Enumeration Introduction Gathering Information Enumeration SNMP is enabled by default on most IP PBXs and IP phones Simple SNMP sweeps will garner lots of useful information If you know the device type, you can use snmpwalk with the appropriate OID You can find the OID using Solarwinds MIB Default “passwords”, called community strings, are common SNMP Enumeration Countermeasures Gathering Information Enumeration Disable SNMP on any devices where it is not needed Change default public and private community strings Try to use SNMPv3, which supports authentication Network Infrastructure DoS Attacking The Network Network DoS The VoIP network and supporting infrastructure are vulnerable to attacks VoIP media/audio is particularly susceptible to any DoS attack which introduces latency and jitter Attacks include: Flooding attacks Network availability attacks Supporting infrastructure attacks Flooding Attacks Introduction Attacking The Network Network DoS Flooding attacks generate so many packets at a target, that it is overwhelmed and can’t process legitimate requests Flooding Attacks Countermeasures Attacking The Network Network DoS Layer 2 and 3 QoS mechanisms are commonly used to give priority to VoIP media (and signaling) Use rate limiting in network switches Use anti-DoS/DDoS products Some vendors have DoS support in their products (in newer versions of software) Network Availability Attacks Attacking The Network Network DoS This type of attack involves an attacker trying to crash the underlying operating system: Fuzzing involves sending malformed packets, which exploit a weakness in software Packet fragmentation Buffer overflows Network Availability Attacks Countermeasures Attacking The Network Network DoS A network IPS is an inline device that detects and blocks attacks Some firewalls also offer this capability Host based IPS software also provides this capability Supporting Infrastructure Attacks Attacking The Network Network DoS VoIP systems rely heavily on supporting services such as DHCP, DNS, TFTP, etc. DHCP exhaustion is an example, where a hacker uses up all the IP addresses, denying service to VoIP phones DNS cache poisoning involves tricking a DNS server into using a fake DNS response Supporting Infrastructure Attacks Countermeasures Attacking The Network Network DoS Configure DHCP servers not to lease addresses to unknown MAC addresses DNS servers should be configured to analyze info from non-authoritative servers and dropping any response not related to queries Network Eavesdropping Introduction Attacking The Network Eavesdropping VoIP configuration files, signaling, and media are vulnerable to eavesdropping Attacks include: TFTP configuration file sniffing (already discussed) Number harvesting and call pattern tracking Conversation eavesdropping By sniffing signaling, it is possible to build a directory of numbers and track calling patterns voipong automates the process of logging all calls Wireshark is very good at sniffing VoIP signaling Conversation Recording Wireshark Attacking The Network Eavesdropping Conversation Recording Other Tools Other tools include: vomit Voipong voipcrack (not public) DTMF decoder Attacking The Network Eavesdropping Network Eavesdropping Countermeasures Attacking The Network Eavesdropping Use encryption: Many vendors offer encryption for signaling Use the Transport Layer Security (TLS) for signaling Many vendors offer encryption for media Use Secure Real-time Transport Protocol (SRTP) Use ZRTP Use proprietary encryption if you have to Network Interception Introduction Attacking The Network Net/App Interception The VoIP network is vulnerable to Man-In-The-Middle (MITM) attacks, allowing: Eavesdropping on the conversation Causing a DoS condition Altering the conversation by omitting, replaying, or inserting media Redirecting calls Network Interception ARP Poisoning Attacking The Network Net/App Interception The most common network-level MITM attack is ARP poisoning Involves tricking a host into thinking the MAC address of the attacker is the intended address There are a number of tools available to support ARP poisoning: Cain and Abel ettercap Dsniff hunt Network Interception ARP Poisoning Attacking The Network Net/App Interception Network Interception Countermeasures Some countermeasures for ARP poisoning are: Static OS mappings Switch port security Proper use of VLANs Signaling encryption/authentication ARP poisoning detection tools, such as arpwatch Attacking The Network Net/App Interception Attacking The Application Attacking The Application VoIP systems are vulnerable to application attacks against the various VoIP protocols Attacks include: Fuzzing attacks Flood-based DoS Signaling and media manipulation Attacking The Application Fuzzing Fuzzing Introduction Fuzzing describes attacks where malformed packets are sent to a VoIP system in an attempt to crash it Research has shown that VoIP systems, especially those employing SIP, are vulnerable to fuzzing attacks There are many public domain tools available for fuzzing: Protos suite SipBomber Asteroid SFTF Fuzzy Packet SIP Proxy NastySIP SIPp Scapy SIPsak Fuzzing Commercial Tools There are some commercial tools available: Beyond Security BeStorm Codenomicon MuSecurity Mu-4000 Security Analyzer Security Innovation Hydra Sipera Systems LAVA tools Attacking The Application Fuzzing Fuzzing Countermeasures Attacking The Application Fuzzing Make sure your vendor has tested their systems for fuzzing attacks Consider running your own tests An VoIP-aware IPS can monitor for and block fuzzing attacks Flood-Based DoS Attacking The Application Flood-Based DoS Several tools are available to generate floods at the application layer: rtpflood – generates a flood of RTP packets inviteflood – generates a flood of SIP INVITE packets SiVuS – a tool which a GUI that enables a variety of floodbased attacks Virtually every device we tested was susceptible to these attacks Flood-Based DoS Countermeasures Attacking The Application Flood-Based DoS There are several countermeasures you can use for floodbased DoS: Use VLANs to separate networks Use TCP and TLS for SIP connections Use rate limiting in switches Enable authentication for requests Use SIP firewalls/IPSs to monitor and block attacks Attacking The Application Sig/Media Manipulation Registration Manipulation Proxy Proxy Hijacked Session Hijacked Media User Attacker User Attacking The Application Sig/Media Manipulation Session Teardown Proxy Proxy Attacker Sends BYE Messages To UAs User Attacker User Attacking The Application Sig/Media Manipulation IP Phone Reboot Proxy Proxy Attacker Sends check-sync Messages To UA User Attacker User Audio Insertion/Mixing Proxy User Attacker Sees Packets And Inserts/Mixes In New Audio Attacking The Application Sig/Media Manipulation Proxy Attacker User Signaling/Media Manipulation Countermeasures Attacking The Application Sig/Media Manipulation Some countermeasures for signaling and media manipulation include: Use digest authentication where possible Use TCP and TLS where possible Use SIP-aware firewalls/IPSs to monitor for and block attacks Use audio encryption to prevent RTP injection/mixing Voice SPAM Introduction Social Attacks Voice SPAM Voice SPAM refers to bulk, automatically generated, unsolicited phone calls Similar to telemarketing, but occurring at the frequency of email SPAM Not an issue yet, but will become prevalent when: The network makes it very inexpensive or free to generate calls Attackers have access to VoIP networks that allow generation of a large number of calls It is easy to set up a voice SPAM operation, using Asterisk, tools like “spitter”, and free VoIP access Voice SPAM Countermeasures Social Attacks Voice SPAM Some potential countermeasures for voice SPAM are: Authenticated identity movements, which may help to identify callers Legal measures Network-based filtering Enterprise voice SPAM filters: Black lists/white lists Approval systems Audio content filtering Turing tests VoIP Phishing Introduction Social Attacks Phishing Similar to email phishing, but with a phone number delivered though email or voice When the victim dials the number, the recording requests entry of personal information VoIP Phishing Countermeasures Traditional email spam/phishing countermeasures come in to play here. Educating users is a key Social Attacks Phishing Final Thoughts Final Thoughts General network security is improving in some ways, but new threats are emerging Network-based security and managed security services can be used to improve enterprise security Don’t neglect internal security and key applications