* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Your computer
Survey
Document related concepts
Transcript
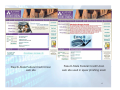
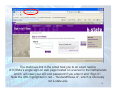
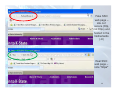
Protecting your Digital Self Basic Email and Web Security IT Security Training Mark Raker 20 February 2015 Primary Online Risks and Threats To Computers • Viruses Worms Trojans • Spyware • • To Families • • • • • Cyberbullies File-sharing abuses Invasion of privacy Disturbing content Predators To Personal Information • Online fraud and phishing Hoaxes Identity theft • Spam • • Primary Threats to Computer Security Viruses/Worms Software programs designed to invade your computer, and copy, damage, or delete your data. Trojans Viruses that pretend to be helpful programs while destroying your data, damaging your computer, and stealing your personal information. Spyware Software that tracks your online activities or displays endless ads. Primary Online Risks for Children Disturbing Content File-share Abuse Cyberbullies Both children and adults may use the Internet to harass or intimidate other people. Unauthorized sharing of music, video, and other files may be illegal, and download malicious software. If kids explore unsupervised, they could stumble upon images or information you may not want them exposed to. Predators Invasion of Privacy These people use the Internet to trick children into meeting with them in person. If kids fill out online forms, they may share information you don’t want strangers to have about them or your family. Primary Threats to Personal Online Safety Phishing E-mail sent by online criminals to trick you into going to fake Web sites and revealing personal information Identity Theft A crime where con artists get your personal information and access your cash and/or credit Hoaxes E-mail sent by online criminals to trick you into giving them money Spam Unwanted e-mail, instant messages, and other online communication Steps You Can Take Your computer Your family Yourself 1. Turn on Windows Internet firewall. 2. Use Microsoft Update to keep Windows upto-date automatically. 3. Install and maintain antivirus software. 4. Install and maintain anit-spam and antispyware software 5. Backup! 1. Talk with your kids about what they do online. 2. Set clear rules for Internet use. 3. Keep personal information private. 4. Use family safety settings in Microsoft software. 1. Practice Internet behavior that lowers your risk. 2. Manage your personal information carefully. 3. Use anti-phishing and anti-spam technology built into Windows Vista, Windows XP SP2, Windows Live, and Microsoft Outlook. Steps to Secure Your Computer 1. 2. 3. 4. 5. 6. 7. 8. Keep Your Operating System Up To Date Install and Update Anti-Virus Use Strong Passwords Enable Firewall Protection Install and Use Spyware Removal Tools Back Up Important Files Enable Screen Saver Passwords Be a little paranoid Set Strong Passwords The easiest way to break into your computer is a weak or blank password. If your computer is compromised it can be used to attack other computers on campus or around the world. • Set Your Computer Password - Do not leave it blank • Password Tips • Never share your password. • Never write your password down. • Change your password periodically. • Creating a Strong Password • • • • • • Passwords should be 7 characters or longer. The longer the better. Passwords should contain at least one alpha character (a-z). Passwords should contain at least one non-alpha character. Do not choose passwords that contain personal information, like pet’s or children’s names. Do not choose a word that is in the dictionary. These are the easiest to crack. Try using a pass phrase. For example, Hpatp0a = “Harry Potter and the Prisoner of Azkaban”. Other Ways to Help Protect Your Computer Back up your files regularly Read Web site privacy statements Close pop-ups using red “X” Think before you click Use Caution When Installing ‘Free’ Applications - Read Privacy Statements Understand what you are getting before you agree to download or share your personal information Many applications install piggy-back programs and toolbars Use the Red “X” to Close Pop-ups Always use the red “X” in the corner of a pop-up screen. • Never click “yes,” “accept,” or even “cancel,” because it could be a trick that installs software on your computer. • Clean up the Desktop Take Steps to Help Protect Your Family Talk with your kids about what they do online Online criminals Inappropriate content Invasion of privacy • • • Set clear rules for Internet use Teach your children to report suspicious activity • Keep personal information private • Teach children to check with you before sharing any personal information online • Help children choose appropriate screen names and e-mail addresses Use family safety software • Its ok to monitor your children’s online activities Evaluating attachments • Don’t open email attachments you were not expecting • From someone you do not know • From someone you know, but weren’t expecting them to send you a file (infected computers can send malicious emails from the owner of the computer to everyone in their email addressbook) • This is especially true if the content of the email message is brief, vague, and/or unusual • Saving it to your desktop without opening it or executing it is usually safe • Many anti-virus applications will scan and block malicious attachments at this point, or • When saved to the desktop, you can manually scan • If not detected, is either OK or a new variant of malware • If you need to send an attachment, contact the recipient and let him know you are sending it 14 Spyware and How to Avoid It. Spyware is software that is downloaded and installed onto your computer, often without your knowledge. Spyware monitors and shares your information while you browse the Internet. • Spyware is often installed by you without your knowledge by piggybacking on other software or by tricking you into installing it. • Some anti-virus software also has anti-spyware capability. • Anti-spyware Recommendations for Windows • Adaware (http://www.lavasoftusa.com/default.shtml.en) • Spybot Search and Destroy (http://www.safer-networking.org/en/home/index.html) • Spyware is not a major problem for the Mac OS yet. There are a few software companies that are starting to address the issue. • MacScan (http://macscan.securemac.com/) • NetBarrier X4 Firewall includes Spyware protection (http://www.intego.com/netbarrier/) Spoof Email (Phishing) Phishing emails are an attempt by thieves to lure you into divulging personal and financial information, for their profit. They pretend to be from well-known legitimate businesses, and increasingly look as if they actually are. They use clever techniques to induce a sense of urgency on your part so that you don't stop to think about whether they are legitimate or not. You can learn to know what to look for and where to report these scams when you find them. 6 Ways to Recognize Phishing 1. Generic Greeting For example, “Dear Customer”. 2. Sense of urgency. May include an urgent warning requiring immediate action. 3. Account status threat. May include a warning that your account will be terminated unless you reply. 4. Forged email address. The sender’s email address may be forged, even if it looks legitimate. 5. Forged links to Web sites. There is often a link to a Website to “fix” the problem. These are usually forged. 6. Requests for personal information. Asking for login and password info, either in email or via the link. Real K-State Federal Credit Union web site Fake K-State Federal Credit Union web site used in spear phishing scam 17 Spear phishing scam received by K-Staters in January 2010 “Phishing” scams try to trick you into providing private Information, like a password or bank acct info. “Spear phishing” Targets a specific population – in this case, K-State email users. 18 The malicious link in the email took you to an exact replica of K-State’s single sign-on web page hosted on a server in the Netherlands which will steal your eID and password if you enter it and “Sign in”. Note the URL highlighted in red – “flushandfloose.nl”, which is obviously not k-state.edu 19 Fake SSO web page – site not secure (http, not https) and hosted in the Netherlands (.nl) Real SSO web page – note “https” 20 Most Effective Spear Phishing Scam 21 Most Effective Spear Phishing Scam 22 Most Effective Spear Phishing Scam 23 Another Sample Spam Email 24 Recognizing Fake Antivirus Alerts Actual pop-up alert from Trend Micro OfficeScan: 25 Recognizing Fake Antivirus Alerts Example of a Fake AV “scareware” alert that tries trick you into buying worthless software to fix a non-existent infections: 26 Conclusion • There’s no way to be 100% secure surfing the web these days • Use multi-faceted approach to reduce your risk (browser security features, browser add-ons, Trend Micro security software, educate yourself) • These tools and techniques make your browsing experience less convenient and may frustrate you at times, but they are necessary in today’s hostile online climate • Think before you click! 27