* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Web Site Development Tools
Information security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Cyberattack wikipedia , lookup
Unix security wikipedia , lookup
Network tap wikipedia , lookup
Distributed firewall wikipedia , lookup
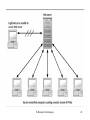
Security-focused operating system wikipedia , lookup
Wireless security wikipedia , lookup
Computer security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Chapter 7 E-Business Network and Web Site Security E-Business Technologies 1 Objectives In this chapter, you will learn to: • Describe general e-business and Web site security issues • Identify ways to protect the physical security of a network • List internal network security risks and explain how to protect against them • Discuss external network and Web site security risks and explain how to protect against them E-Business Technologies 2 Objectives In this chapter, you will learn to: • Identify the risks associated with an e-business’s online transactions • Illustrate a virtual private network • Describe wireless security issues • Discuss the importance of security audits E-Business Technologies 3 General Network and Web Site Security Issues • E-business security: protecting data and physical networks • E-business security risks include: – Physical risks: Damage to network and data – Internal risks: Threats originating within organization – External risks: Threats from outside the organization – Transactional risks: Data loss and interception E-Business Technologies 4 Valued Gateway Client: Physical Risks • Include accidental or deliberate damage to equipment or data resulting from natural disaster or sabotage • Specific issues include: – Network equipment and physical location – Electrical power backup – Internet connectivity redundancy – Outsourcing physical risks E-Business Technologies 5 Network Equipment and Physical Location Equipment and locations security include: • Network facilities location: network equipment and server rooms always locked, locations anonymous • Fire protection: install fire-suppression systems that do not damage servers, routers, electrical equipment - but these systems might be fatal to humans • Network facilities construction: construction and design of facilities more substantial than conventional office space and with particular attention to electrical and communication considerations E-Business Technologies 6 Electrical Power Backup • E-businesses should consider two levels of backup power: – Batteries that assume power within milliseconds of a failure – Power generators that automatically start when the batteries die • Critical servers should never be out more than five minutes per year to achieve “five nines reliability” (99.999% uptime) E-Business Technologies 7 Internet Connectivity Redundancy • E-businesses should have more than one connection to the Internet • ISPs and Web hosting companies often have connections to more than one network service provider (NSP) • Complete data-center redundancy allows e-businesses to continue operations from a different location in the event of a major disaster • What is the price of redundancy and when is the price too high? E-Business Technologies 8 Outsourcing Physical Risks • Using Web hosting services provides physically secure environment for e-business servers • Fee for service arrangement provides power, connectivity, and secure environment • Eliminates internal risks to physical security • What are the benefits for small firms to outsource? E-Business Technologies 9 Physical Risks to Network and Web Site Assets • Include accidental or deliberate damage to equipment or data is accidental or deliberate more likely? • Caused by natural disaster or sabotage • Threat to network infrastructure includes: – Damage to network equipment – Damage to power supplies – Damage from fire E-Business Technologies 10 Network Equipment and Physical Location • Physical security begins with equipment safety • Threat reduction includes proper management of network facilities location and fire protection • Security countermeasures for network facilities locations include: – Locked network equipment room doors with restricted personnel access – Locations of servers and switching equipment kept anonymous E-Business Technologies 11 Network Equipment and Physical Location • Fire protection and countermeasures to prevent fire damage include: – Use fire suppression system approved for electrical fires in server, switch, and power rooms – Use only fire extinguishers approved for electrical fires in server, switch, and power rooms – Pre-select and train employees responsible for fire control E-Business Technologies 12 Internal Security Risks • Come from inside the company: unhappy employees, poor security awareness, poor planning • Establishing and enforcing security policy is first countermeasure • Additional countermeasures include: – Password protecting the network – Using biometric identification – Using smart card authorization E-Business Technologies 13 Passwords • Passwords are used to identify a specific computer user and grant user access • Effective when created properly and changed regularly DO DON’T Use a combination of at least six characters and numbers Use familiar names, dates, or numbers significant to user Use easy to remember combinations Use common words from the dictionary, street names, etc. Change password periodically Pick new password similar to the old password E-Business Technologies 14 Biometric Identification • Measurement of biological data • Biometric security devices and software measure and record a computer user’s unique human characteristics (such as eye retina or iris) for user identification • Still under development E-Business Technologies 15 Smart Card • Smart cards contain an embedded memory chip with user identification information • Can be used to authenticate a remote user logging into a network • Disadvantage: Risk of loss or theft E-Business Technologies 16 Backup and Restore Policies and Procedures • Describes the plan for securing vital data files and software in case of disaster • Specifies when and how critical files and software are backed up • Backups should be built in to daily, weekly, monthly network maintenance schedule • Test restore procedure, and archive, by performing periodic restores E-Business Technologies 17 Backup and Restore Policies and Procedures • Backup media should also be stored offsite or at least a second copy of the backup media) • Some e-businesses assign backup responsibilities to employees outside of IT department • Offsite storage also available via Internet connection from data management companies E-Business Technologies 18 Disaster Recovery Planning • Disaster Recovery Plan part of e-business’ Business Continuity Plan • DRP for network operations should include procedures for handling electrical outages, data loss, and security breaches • Plan can include the use or redundant servers and equipment to handle system failover • DRP should be tested periodically E-Business Technologies 19 External Security Risks • Originate outside the company’s network • Must bypass network defenses • Connecting to the Internet exposes private LANs to risk of attack • Stringent security necessary to protect against external risk E-Business Technologies 20 Hackers • Outside intruders that deliberately gain unauthorized access to individual computers or computer networks • White hat hackers find and make known weaknesses in computer systems without regard for personal gain • Black hat hackers (crackers) gain access to steal valuable information, disrupt service, or cause damage E-Business Technologies 21 Hacker Attack Tactics • Objective: interrupt operations or use hacked computer as base of attack on other computers • The most common method is to send confusing data to a server or other computer • Crashing a program can allow a hacker to take control of computers • Buffer overflows tie up operating memory, degrading performance, causing crashes E-Business Technologies 22 Distributed Denial of Service Attacks • Denial of Service (DoS) attacks designed to disable network using flood of useless traffic • Distributed DoS uses multiple computers to attack networks • DDoS attacks include: – Unending string of Pings – Sending hundred of huge e-mail messages E-Business Technologies 23 E-Business Technologies 24 Web Site Defacement • Hacker deliberately changes the content of Web pages • Caused by breaking into network, accessing Web site files and modifying files • Better known victims include FBI, Goodyear, NY Times, and NASA E-Business Technologies 25 Hacker Countermeasures • Firewalls designed to resist buffer overflows and other common types of hacker attacks • Firewall types include: – Packet-filtering firewalls – Circuit-level firewalls - verified by TCP, the weakness is that once it is verified subsequent packets are not verified – Application-level firewalls (e-mail, FTP, or some other application) E-Business Technologies 26 E-Business Technologies 27 hacking back is illegal Hacker Countermeasures • Network Address Translation uses external IP addresses to hide internal IP addresses • Proxy server uses external IP address to send HTTP request over Internet and forwards responses from HTTP servers to requesting client using internal IP address E-Business Technologies 28 How Filters Work • A filter is a process or device that screens incoming information • Allows only information that meets specified criteria through • Disabling service ports denies access to HTTP, email from Internet • Restricting access to internal IP addresses hides computers E-Business Technologies 29 Viruses Standard computer viruses: • Are small, usually destructive, programs that are inserted into other files that then become “infected” • Infect executable programs or operating system files, spreading when infected program executes • Can also spread via e-mail headers or attachments • Can prevent a computer system from booting, erase files or entire hard drives, prevent the saving or printing of files, and send repetitive email messages E-Business Technologies 30 Worms • Viruses that reside in a computer’s memory replicating itself • Uncontrolled replications consume a computer’s resources, slowing or crashing the system NAME DATE IDENTIFIED WHAT IT DOES W32.Nimda. A@mm 9/18/2001 Sent as e-mail or MS Outlook/Outlook Express folders. Attacks IIS Web servers. E-Business Technologies 31 Macro Viruses • A macro virus is a virus that infects macros • Distributed in files such as Word documents or Excel workbooks e-mailed or transferred via floppy disk NAME DATE IDENTIFIED WHAT IT DOES W97M.Debil Byte.A 02/05/2002 Infects MS Word Normal.dot template, and subsequent documents E-Business Technologies 32 Trojan Horses • Pretends to be something useful or fun, does something malicious instead • Used to steal passwords, record a user’s keystrokes, locate IP addresses, and plant other destructive programs NAME DATE IDENTIFIED WHAT IT DOES Backdoor. Surgeon 02/20/2002 Allows hacker to take control by opening a port (35000) and get control of computer E-Business Technologies 33 Wireless Viruses • “Liberty Crack” Palm Trojan, identified in August 2000 – Could delete all applications on a Palm device • “Phage” discovered in September 2000 – Infected Palm operating system applications and documents – Proliferated when users beamed or shared an infected document E-Business Technologies 34 Virus Hoaxes • Some so-called viruses trumpeted in the media or announced via warning e-mails are just hoaxes • False warnings about viruses proliferate as quickly as real viruses • Creates an atmosphere in which a real virus warning might not be taken seriously • Several antivirus software vendors maintain upto-date information on viruses, worms, Trojan horses, and hoaxes. This information is available online. E-Business Technologies 35 Virus Countermeasures • Countermeasures to block infections include: – Antivirus software – Employee education – Installing software updates and patches – User awareness – Use of application software tools – It's not just the job of IT, but of all users E-Business Technologies 36 Transactional Security • Transactional security includes: – – – – Authentication Integrity Nonrepudiation Confidentiality • Protective measures include: sending and receiving encrypted messages or data, using digital certificates to authenticate the parties involved in the transaction, and storing retained customer information properly E-Business Technologies 37 Encryption • Cryptography is the art of protecting information by encrypting it • Encryption is the translation of data into a secret code called ciphertext • Ciphertext that is transmitted to its destination and then decrypted (or returned to its unencrypted format) is called plaintext • Both parties in a transaction need access to encryption key • Network encryption uses two keys: a public key to encrypt information and a private key to decrypt it E-Business Technologies 38 Public Key Infrastructure • An e-business obtains public and private keys from a certificate authority (CA) • Public keys are posted to a public directory • Private keys are given only to the e-business requesting the keys • A digital certificate is the electronic security credential that certifies an entity’s identity E-Business Technologies 39 E-Business Technologies 40 How Public Key Encryption Works • Public-key encryption is asymmetric • Uses very large prime numbers to create public keys • Public and private keys are used for the initial session greeting; session keys encrypt and decrypt data • Session keys are shorter keys created and used only during the current session and discarded afterward • In the U.S., session keys usually consist of 16 digits equaling 128 bits, also called 128-bit keys E-Business Technologies 41 Security Protocols • Secure Sockets Layer (SSL) uses public key encryption and digital certificates; and is included in Web browsers/Web servers • Transport Layer Security (TLS) used to assure no third-party access to Internet communications Uses two protocols: – TLS Record Protocol – TLS Handshake Protocol • Secure Electronic Transactions (SET) protocol used for presenting credit card transaction on the Internet E-Business Technologies 42 Virtual Private Networks • Virtual Private Networks (VPNs) are private networks that use the Internet to transmit data VPNs use: • Firewalls • Public key encryption • Digital certificates E-Business Technologies 43 E-Business Technologies 44 Tunneling • Tunneling encapsulates one protocol within another protocol requires telecomm equipment that supports VPN • VPNs using the Internet encapsulate encrypted data, sending and receiving IP addresses, and a special tunneling protocol within a regular IP packet • Tunneling protocols include: Point-to-Point, GRE, L2TP, and IPSec • Method of data encryption and encapsulation depends on the protocol used E-Business Technologies 45 Wireless Security • Eavesdropping on early wireless transmissions was fairly simple: – FDMA technologies stayed on one frequency for call duration, required “listening device” that operated on same frequency – TDMA technologies switch can be intercepted using device that listens for one-third of a second and then decompresses signal into full second of speech • CDMA (other current standards) poses more of a challenge, but … not invincible E-Business Technologies 46 WAP and WTLS • Wireless Transport Layer Security (WTLS) uses encryption and digital certificates • Upon accessing WAP server, WAP client requests secure connection • WAP server responds by sending digital certificate, with public key • WAP client generates encrypted session key to WAP server, which decrypts the key • WAP client/server can send/receive encrypted data for balance of session E-Business Technologies 47 WLANs and Security • WLANs are most vulnerable at wireless access points • Hackers need only an 802.11b-enabled laptop, an inexpensive antennae, and WLAN access point detection software, such as NetStumbler • Using “meaningful” access point names and “default” settings on wireless access points simplifies hacker’s job • Using Wireless Equivalent Privacy (WEP) security protocol (IEEE 802.11b Wi-Fi) provides encryption and authentication of wireless transmissions E-Business Technologies 48 IrDA and Bluetooth Security • Short distances and line-of-sight requirements for IrDA devices make “sniffers” impractical • Using laptops with default IrDA port settings in public places (such as airports) automatically allows networking with other IrDA devices without authentication or passwords • Bluetooth uses 128-bit link key, private encryption keys, user PIN and device addresses for transmission security • Bluetooth vulnerability: device address sent with each transmission and user PINs can be compromised easily by theft or loss of device E-Business Technologies 49 Security Audits • Security audit is a comprehensive review and assessment of an e-business’s security vulnerabilities • A complete security audit should include: reviewing security policies, employee security training, and the physical security of the e-business’s offices and network facilities • Audits can include examining the technical security of a network via penetration testing or actual attempted hacking attacks by security audit personnel E-Business Technologies 50 Penetration Test Protection • When evaluating security firms request: – Proof of insurance: cover cost of fixing damage/losses caused by penetration testing – Nondisclosure agreements: prevent disclosure of test results, network and proprietary information – Scanning tools: determine what scanning tools will be used for testing – Scope of engagement: scope of audit and test plans – Documentation: final detailed accounting of audit, including individual test results, findings E-Business Technologies 51