* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download DDoS Attacks: What You Can`t See Can Hurt You Dave Larson
Mobile security wikipedia , lookup
Computer security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Cyberwarfare wikipedia , lookup
Cyberattack wikipedia , lookup
Cybercrime countermeasures wikipedia , lookup
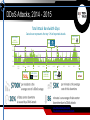
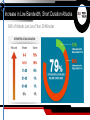
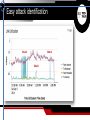
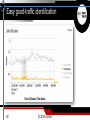
DDoS Attacks: What You Can’t See Can Hurt You Dave Larson DDoS Attacks, 2014 - 2015 Total Attack Bandwidth Gbps Data shown represents the top ~2% of reported attacks DEC 8 2014 DEC 31 2013 MAJOR HOSTING SITES XBOX JUL 23 2014 400 300 200 100 DEC 1 JAN 1 2014 FEB 1 MAR 1 FEB 5 2014 APR 1 APR 1 2014 BATTLE.NET MAY 1 JUN 1 JUL 1 JUN 23 2014 HONG KONG VOTING SITES AUG 1 SEP 1 OCT 1 NOV 1 DEC 1 AUG 24 2014 Source: Network Computing/Ponemon Institute Source: Digital Attack Map - DDoS attacks around the globe JAN 1 2015 JAN 4 2015 4chan The Attackers are Getting Smarter Researchers are finding an uptick in the number of new techniques Attackers defeating traditional protection (Firewall, ACL, Blackhole) Attackers are developing new methods of bypassing defenses DDoS Digital Attack Map http://www.digitalattackmap.com/ Fragmented Application Volumetric TCP Connect According to a recent survey conducted by the SANS Institute… “The most damaging DDoS attacks mix volumetric attacks with targeted, applicationspecific attacks.” The Problem is Real – and Pervasive • Our average customer sees almost 4 attacks per day! • Some customers see many more • Across all verticals and segments • No one is immune! Increase in Low Bandwidth, Short Duration Attacks 96% of Attacks Last Less Than 30 Minutes Real-time DDoS Data Interpretation Example – Hosting Data Center under constant attack Attack Traffic Raw Internet Good Traffic Raw Internet Good Traffic Protected Network Attack traffic is well above the normal levels and stays below the link capacity Attacks are mitigated in real-time Protected networks see normal traffic levels Flexible rule changes quickly allow mitigation of newly discovered attacks Easy attack identification Attack Attack Attack Easy good-traffic identification 40 © 2015 Corero Flow-based context Normal port profile 80, 443, etc Attack port profile 1900 (SSDP) Corero Analytics shows reflection hosts 40 © 2015 Corero DDoS Analytics & Data Interpretation - Highlights • Real-time and historical DDoS attack data interpretation Single screen operation with summary, top charts, drill-down searches • Attack identification Provides clear indication of current and historical attacks • Victim identification Lists top targeted IP addresses • Good-traffic identification Displays good traffic to the protected network • Threat vector identification Lists top blocked and detected events • Real-time defense DDoS detection and prevention Easy threat vector identification Real-time defense - Hosting Provider SmartWall Defeats Small Probes and Large Floods Easily Real-time defense - Hosting Provider Even Regular Large Bandwidth DDoS Attacks are no match for SmartWall. Multi-gigabit, high frequency attacks are defeated with ease. Attacks against online gaming company Blue Line = Traffic Inbound from Internet Yellow Line = Traffic Forwarded to Protected Network SmartWall Defeats Half Hour Duration, 400K Packet/Second Attack (Blue Spikes) SmartWall Forwards All Legitimate Traffic During Attack (Yellow Lines) Eliminate the DDoS problem Organizations must have the ability to visualize DDoS and mitigate in Real Time: Single-Pane-of-Glass analytics • • • • • Rich DDoS security dashboards Granular drill-down detailed analysis Real-time alerts and DDoS posture assessment Detailed report generation Event-based and optional line-rate PCAP generation Full integration with Splunk and/or syslog extensibility for integration with other SIEM tools Corero SmartWall® Network Threat Defense SmartWall® Threat Defense System (TDS) Online Enterprises & Service/Hosting Providers On-Premises or Cloud deployments Protection in modular increments of 10 Gbps In-line or on-demand scrubbing topologies