Cybersecurity and Information Assurance PPT
... • Used for many personal electronic devices including phones, music players, etc. Threats • Bluejacking-sending unsolicited messages to Bluetooth devices • Bluesnarfing-unauthorized access of information from a wireless device through a Bluetooth connection • Bluebugging-unauthorized control of Blue ...
... • Used for many personal electronic devices including phones, music players, etc. Threats • Bluejacking-sending unsolicited messages to Bluetooth devices • Bluesnarfing-unauthorized access of information from a wireless device through a Bluetooth connection • Bluebugging-unauthorized control of Blue ...
HSARPA Cyber Security R&D
... We still lack large-scale deployment of security technology sufficient to protect our vital infrastructures ...
... We still lack large-scale deployment of security technology sufficient to protect our vital infrastructures ...
The Difference Between Compliance and Cyber Security
... president of commercial markets for Lockheed's Information Systems security services. ...
... president of commercial markets for Lockheed's Information Systems security services. ...
Forms of Network Attacks
... Introduce a virus program that uses your computers and software applications to copy viruses throughout your network. Introduce a Sniffer program to analyze your network and gain information that can eventually be used to crash or to corrupt your systems and network. Abnormally terminate your data a ...
... Introduce a virus program that uses your computers and software applications to copy viruses throughout your network. Introduce a Sniffer program to analyze your network and gain information that can eventually be used to crash or to corrupt your systems and network. Abnormally terminate your data a ...
Computer Science, MSCS - Northeastern University
... Computer Science, MSCS Northeastern University’s Master of Science in Computer Science is designed to prepare students for a variety of careers in computer science. The program combines both computing and important application domains—enabling you to increase your broad-based knowledge in the field ...
... Computer Science, MSCS Northeastern University’s Master of Science in Computer Science is designed to prepare students for a variety of careers in computer science. The program combines both computing and important application domains—enabling you to increase your broad-based knowledge in the field ...
Medical_Informatics_-_Computer_Networks
... masquerading as a trustworthy entity in an electronic communication). DoS (Denial of service attack; overloading a network by flooding it with useless traffic. Two types, this normal type and DDoS (Distributed DoS) where several computers flood a system with packets in a co-ordinated ...
... masquerading as a trustworthy entity in an electronic communication). DoS (Denial of service attack; overloading a network by flooding it with useless traffic. Two types, this normal type and DDoS (Distributed DoS) where several computers flood a system with packets in a co-ordinated ...
Systems Administrator needed for DoD Griffin Cyberspace Defense
... filter sensor traffic and alerts reporting activity based on Crew CC’s instruction that traffic does not need to be reviewed in a “real-time” operation by 33 NWS analysts. Monitor the effectiveness of the IDS/IPS sensor’s ability to collect and report suspicious network activity on Air Force network ...
... filter sensor traffic and alerts reporting activity based on Crew CC’s instruction that traffic does not need to be reviewed in a “real-time” operation by 33 NWS analysts. Monitor the effectiveness of the IDS/IPS sensor’s ability to collect and report suspicious network activity on Air Force network ...
University of Arizona
... • However, the ease with which these applications can be downloaded and run has provided a new vehicle for inflicting damage • Vandals can take on the form of a software application or applet that causes destruction of various degrees • A vandal can destroy a single file or a major portion of a comp ...
... • However, the ease with which these applications can be downloaded and run has provided a new vehicle for inflicting damage • Vandals can take on the form of a software application or applet that causes destruction of various degrees • A vandal can destroy a single file or a major portion of a comp ...
Factsheet - KFSensor
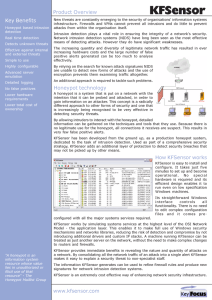
... files and it comes preconfigured with all the major systems services required. KFSensor works by simulating systems services at the highest level of the OSI Network Model - the application layer. This enables it to make full use of Windows security mechanisms and networks libraries, reducing the ris ...
... files and it comes preconfigured with all the major systems services required. KFSensor works by simulating systems services at the highest level of the OSI Network Model - the application layer. This enables it to make full use of Windows security mechanisms and networks libraries, reducing the ris ...
Incident Response: Six Steps for Managing Cyber Breaches
... Now that you have identified what the malware is, what it does, its characteristics and hash values, as well as which and how much sensitive data has been breached, it is time to remediate. Your incident response team can begin remediating systems by deleting all malicious or unauthorized code (if a ...
... Now that you have identified what the malware is, what it does, its characteristics and hash values, as well as which and how much sensitive data has been breached, it is time to remediate. Your incident response team can begin remediating systems by deleting all malicious or unauthorized code (if a ...
Guide to Security - Cal Poly Pomona Foundation, Inc.
... • However, the ease with which these applications can be downloaded and run has provided a new vehicle for inflicting damage • Vandals can take on the form of a software application or applet that causes destruction of various degrees • A vandal can destroy a single file or a major portion of a comp ...
... • However, the ease with which these applications can be downloaded and run has provided a new vehicle for inflicting damage • Vandals can take on the form of a software application or applet that causes destruction of various degrees • A vandal can destroy a single file or a major portion of a comp ...
Computer Security: Principles and Practice, 1/e
... • Threat - A potential for violation of security, which exists when there is a circumstance, capability, action, or event that could breach security and cause harm. • Vulnerability - Flaw or weakness in a system's design, implementation, or operation and management that could be exploited to violate ...
... • Threat - A potential for violation of security, which exists when there is a circumstance, capability, action, or event that could breach security and cause harm. • Vulnerability - Flaw or weakness in a system's design, implementation, or operation and management that could be exploited to violate ...
Virtual Cyber Security Lab - Celtic-Plus
... Celtic-Plus Proposers Day 22 September 2016, Istanbul ...
... Celtic-Plus Proposers Day 22 September 2016, Istanbul ...
Study Material for MCA (SEM-V) Subject: Cyber Security and
... The internet and the privately owned systems provide new and better opportunities for espionage. ...
... The internet and the privately owned systems provide new and better opportunities for espionage. ...
systemsprinciples2
... Insiders: employees or customers seeking revenge or gain Criminals seeking financial gain. Organized crime seeking gain or hiding criminal activities. Organized terrorist groups or nation states trying to ...
... Insiders: employees or customers seeking revenge or gain Criminals seeking financial gain. Organized crime seeking gain or hiding criminal activities. Organized terrorist groups or nation states trying to ...
Irfan Ahmed Assistant Professor Department of Computer Science
... ! proprietary firmware/OS ! Limited tools/techniques to access and modify ...
... ! proprietary firmware/OS ! Limited tools/techniques to access and modify ...
Taxonomy of Computer Security Incidents
... • Incident Category Type (e.g., CAT 1, CAT 2, etc.) • Incident Timestamp • Source IP, Destination IP, port, and protocol • Operating System, including version, patches, etc. • System Function (e.g., DNS/web server, workstation, etc.) • Antivirus software installed, including version, and latest upda ...
... • Incident Category Type (e.g., CAT 1, CAT 2, etc.) • Incident Timestamp • Source IP, Destination IP, port, and protocol • Operating System, including version, patches, etc. • System Function (e.g., DNS/web server, workstation, etc.) • Antivirus software installed, including version, and latest upda ...
SRI International
... TCP/IP attacks – Realtime event correlation system to support local operator identification and response – Specification-based policies enabling intrusion prevention without impacting availability – An anonymous and secure peer sharing framework that allows • Sector wide threat intelligence acquisit ...
... TCP/IP attacks – Realtime event correlation system to support local operator identification and response – Specification-based policies enabling intrusion prevention without impacting availability – An anonymous and secure peer sharing framework that allows • Sector wide threat intelligence acquisit ...
Computer Hacking
... accomplish a goal outside of the creator’s original purpose. • To be accused of hacking, it must be proven that someone gained access to the computer, intending to hack it without permission. ...
... accomplish a goal outside of the creator’s original purpose. • To be accused of hacking, it must be proven that someone gained access to the computer, intending to hack it without permission. ...
Skating on Stilts
... • 74% have implemented new measures as a result of regulation • 58% say regulation has “sharpened policy and improved security” • 28% say it has “diverted resources from improving security to recording/reporting incidents or other forms of compliance” ...
... • 74% have implemented new measures as a result of regulation • 58% say regulation has “sharpened policy and improved security” • 28% say it has “diverted resources from improving security to recording/reporting incidents or other forms of compliance” ...
Security Requirements
... those that have access to information that they are not suppose to gain access to. “In 1999, some students at the University of the South Pacific managed to get access to the system and retrieve a list of all students email passwords. This allowed them to send abusive messages to others using othe ...
... those that have access to information that they are not suppose to gain access to. “In 1999, some students at the University of the South Pacific managed to get access to the system and retrieve a list of all students email passwords. This allowed them to send abusive messages to others using othe ...
PROTECTING INFORMATION RESOURCES
... • Critical for most organizations – Especially in recent years, with hackers becoming more numerous and adept at stealing and altering private information ...
... • Critical for most organizations – Especially in recent years, with hackers becoming more numerous and adept at stealing and altering private information ...
module 2 network security unit 1
... • Malicious programs like viruses, worms (is a self-replicating virus that does not alter files but resides in active memory and duplicates itself. ) • Trojan horses (actually do damage once software installed or run on your computer) • spyware(spyware is programming that is put in someone's compute ...
... • Malicious programs like viruses, worms (is a self-replicating virus that does not alter files but resides in active memory and duplicates itself. ) • Trojan horses (actually do damage once software installed or run on your computer) • spyware(spyware is programming that is put in someone's compute ...
Click here to access the presentation.
... − Bandwidth compression; Quality of Service ICT Industry Revolution ...
... − Bandwidth compression; Quality of Service ICT Industry Revolution ...