ppt
... • Fig. 2.14a shows that if only one request is served at a time, the resources at the server machine may be underutilized, the server throughput (number of requests served per time unit) may be low, and response time to clients will increase as the load on the server increases • Fig. 2.14b shows tha ...
... • Fig. 2.14a shows that if only one request is served at a time, the resources at the server machine may be underutilized, the server throughput (number of requests served per time unit) may be low, and response time to clients will increase as the load on the server increases • Fig. 2.14b shows tha ...
Evaluation of the Proximity betw Web Clients and their
... A client with LDNS in cluster, responding to our request, and has at least one cache server in its cluster ...
... A client with LDNS in cluster, responding to our request, and has at least one cache server in its cluster ...
No Slide Title
... Provides a store-and-forward mail capability between host computer mail systems on the network ...
... Provides a store-and-forward mail capability between host computer mail systems on the network ...
CH7
... • FTP implementations include the functions of a protocol interpreter (PI) and a data transfer process (DTP). PI and DTP define two separate processes that work together to transfer files. As a result, FTP requires two connections to exist between the client and server, one to send control informati ...
... • FTP implementations include the functions of a protocol interpreter (PI) and a data transfer process (DTP). PI and DTP define two separate processes that work together to transfer files. As a result, FTP requires two connections to exist between the client and server, one to send control informati ...
IIS 7.0: a robust Web & Application Server
... Deploy federation servers in multiple organizations to facilitate business-tobusiness (B2B) transactions AD FS provides a Webbased, SSO solution ...
... Deploy federation servers in multiple organizations to facilitate business-tobusiness (B2B) transactions AD FS provides a Webbased, SSO solution ...
Detecting Malicious SMB Activity Using Bro
... “Server Message Block (SMB) can be defined as a protocol used for network file sharing that allows applications on a computer to read and write to file shares and request services from server programs on a computer network.” (Microsoft, 2013). Applications can utilize the SMB protocol to retrieve fi ...
... “Server Message Block (SMB) can be defined as a protocol used for network file sharing that allows applications on a computer to read and write to file shares and request services from server programs on a computer network.” (Microsoft, 2013). Applications can utilize the SMB protocol to retrieve fi ...
View the full User Guide
... Mohawk College VPN (Virtual Private Network) service provides a web-based, secure, authenticated remote access to the campus network, which enables faculty, staff, partners, and consultants to work from anywhere, at anytime, using any device including unmanaged PCs, mobile phones and PDAs. You can a ...
... Mohawk College VPN (Virtual Private Network) service provides a web-based, secure, authenticated remote access to the campus network, which enables faculty, staff, partners, and consultants to work from anywhere, at anytime, using any device including unmanaged PCs, mobile phones and PDAs. You can a ...
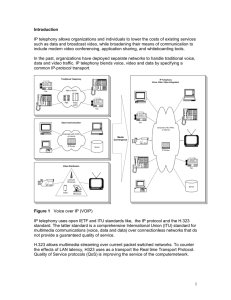
Introduction
... 1. John wishes to initiate an H.323 conference with Alice, another user on the LAN. Once Alice’s video conferencing application creates an Address object and puts it in listen mode. Alice’s IP address is added to the Internet Locator Service (ILS) ...
... 1. John wishes to initiate an H.323 conference with Alice, another user on the LAN. Once Alice’s video conferencing application creates an Address object and puts it in listen mode. Alice’s IP address is added to the Internet Locator Service (ILS) ...
Technical Experience Summary - Novellus Consulting :: HOME
... Work on high availability production servers for Hardware & Windows Server issues. Provide Remote support to Branches. Migrated from previous versions of Active Directory to Windows 2008 to 2012 Auditing access provided to users, Account creation logs and Event Logs. Involved in Datacenter Migration ...
... Work on high availability production servers for Hardware & Windows Server issues. Provide Remote support to Branches. Migrated from previous versions of Active Directory to Windows 2008 to 2012 Auditing access provided to users, Account creation logs and Event Logs. Involved in Datacenter Migration ...
LogiKal Installation Manual - Building Envelope Software
... updates will automatically install after download. If multiple updates are downloaded they will be installed one after the other. In general: All updates are downloaded from the server www.orgadata.com (IP: 80.154.33.61) over the FTP port 21 and saved to the LogiKal directory (e.g. X:\LOGIKAL\Update ...
... updates will automatically install after download. If multiple updates are downloaded they will be installed one after the other. In general: All updates are downloaded from the server www.orgadata.com (IP: 80.154.33.61) over the FTP port 21 and saved to the LogiKal directory (e.g. X:\LOGIKAL\Update ...
Lecture3
... • A Security Association (SA) is a logical simplex connection between two network-layer entities • Two SA’s required for bidirectional secure communication • SA is specified by ...
... • A Security Association (SA) is a logical simplex connection between two network-layer entities • Two SA’s required for bidirectional secure communication • SA is specified by ...
SPARK Research-Based PE Programs, Physical Education
... exams using the Microsoft 70-282 Practice Exam from ipass4sure.com. Once you start using our 70-282 exam questions you simply can't stop! You are guaranteed to pass your Microsoft 70-282 test with ease and in your first attempt. Here's what you can expect from the ipass4sure Microsoft 70-282 course: ...
... exams using the Microsoft 70-282 Practice Exam from ipass4sure.com. Once you start using our 70-282 exam questions you simply can't stop! You are guaranteed to pass your Microsoft 70-282 test with ease and in your first attempt. Here's what you can expect from the ipass4sure Microsoft 70-282 course: ...
Architecting Shared Server Hosting With
... Windows 2000 Advance Server Windows 2000 Data center ...
... Windows 2000 Advance Server Windows 2000 Data center ...
5. Product Warranty
... Efficient Raid management, equipped with Hardware Raid, it supports Raid 0, Raid 1. Configured at HW raid, system & data rebuild and recync performs as high efficiency. Humanistic HDD installation, rigid and elegant aluminum case with retractable tray, it is convenient for HDD installation and repla ...
... Efficient Raid management, equipped with Hardware Raid, it supports Raid 0, Raid 1. Configured at HW raid, system & data rebuild and recync performs as high efficiency. Humanistic HDD installation, rigid and elegant aluminum case with retractable tray, it is convenient for HDD installation and repla ...
ch9
... the building blocks that the network can provide and how those blocks can interact with each other. • Applications might need their own protocols, too. ...
... the building blocks that the network can provide and how those blocks can interact with each other. • Applications might need their own protocols, too. ...
Microsoft Word Format
... was installed onto Windows 2003 and using IIS 6.0 Excellent Knowledge of DNS and Name Servers which are required for the registration of any Domain Name on the Internet and other requirements which are necessary for hosting a Website Installation, Configuration & Implementation of Microsoft (Sybari) ...
... was installed onto Windows 2003 and using IIS 6.0 Excellent Knowledge of DNS and Name Servers which are required for the registration of any Domain Name on the Internet and other requirements which are necessary for hosting a Website Installation, Configuration & Implementation of Microsoft (Sybari) ...
Network
... – Every night every host fetches file from central repository. – OK for a few hundred hosts. – Scalability? • File size. • Centrally managed. ...
... – Every night every host fetches file from central repository. – OK for a few hundred hosts. – Scalability? • File size. • Centrally managed. ...
VPN Scenarios
... http://IIS1.example.com/winxp.gif. You should see a Windows XP graphic. • 28.Click Start, click Run, type \\IIS1\ROOT, and then click OK. You should see the contents of the Local Drive (C:) on IIS1. • 29.Right-click the PPTPtoCorpnet connection, and ...
... http://IIS1.example.com/winxp.gif. You should see a Windows XP graphic. • 28.Click Start, click Run, type \\IIS1\ROOT, and then click OK. You should see the contents of the Local Drive (C:) on IIS1. • 29.Right-click the PPTPtoCorpnet connection, and ...
ABCD - Cisco
... Request For Comments. Document series used as the primary means for communicating information about the Internet. Some RFCs are designated by the IAB as Internet standards. Most RFCs document protocol specifications such as Telnet and FTP, but some are humorous or historical. RFCs are available onli ...
... Request For Comments. Document series used as the primary means for communicating information about the Internet. Some RFCs are designated by the IAB as Internet standards. Most RFCs document protocol specifications such as Telnet and FTP, but some are humorous or historical. RFCs are available onli ...
SIP
... Authentication- RFC 3261 Any time that a proxy server or UA receives a request, it MAY challenge the initiator of the request to provide assurance of its identity. No authorization systems are recommended or discussed in this document. The "Digest" authentication mechanism described in this sect ...
... Authentication- RFC 3261 Any time that a proxy server or UA receives a request, it MAY challenge the initiator of the request to provide assurance of its identity. No authorization systems are recommended or discussed in this document. The "Digest" authentication mechanism described in this sect ...
Lecture04: Network Layer Security
... Common Internet File System (or SMB) Common Internet File System (CIFS), aka Server Message Block (SMB), is a network protocol for file sharing on a LAN, running at app/presentation layer A client-server protocol Rely on other protocols for transport Most commonly used is NetBIOS over TCP ( ...
... Common Internet File System (or SMB) Common Internet File System (CIFS), aka Server Message Block (SMB), is a network protocol for file sharing on a LAN, running at app/presentation layer A client-server protocol Rely on other protocols for transport Most commonly used is NetBIOS over TCP ( ...
Computer Networking viva IT-3
... regardless of whether it is connected to another network or not. Q5 What are the characteristics of the bus topology? A5 In a bus topology, all the communicating equipment is connected through the same cable, or set of cables. Q6 What is star topology A6 Star Topology is the most common type of netw ...
... regardless of whether it is connected to another network or not. Q5 What are the characteristics of the bus topology? A5 In a bus topology, all the communicating equipment is connected through the same cable, or set of cables. Q6 What is star topology A6 Star Topology is the most common type of netw ...
Some Network Commands - Texas Tech University
... Developed by IBM for its LAN Manager product and has been adopted by Microsoft for its Windows NT, LAN Manager, and Windows for Workgroups products. A new, extended version of NetBIOS, the program that lets computers communicate within a local area network. Formalizes the frame format (or arrangemen ...
... Developed by IBM for its LAN Manager product and has been adopted by Microsoft for its Windows NT, LAN Manager, and Windows for Workgroups products. A new, extended version of NetBIOS, the program that lets computers communicate within a local area network. Formalizes the frame format (or arrangemen ...