Hardware Requirements shelby v.5
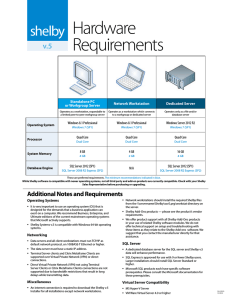
... Data servers and all client workstations must run TCP/IP as default network protocol, on 100BASE-T Ethernet or higher. The data server must have a static IP address. Terminal Server clients and Citrix Metaframe Clients are supported over Virtual Private Network (VPN) or direct connections. ...
... Data servers and all client workstations must run TCP/IP as default network protocol, on 100BASE-T Ethernet or higher. The data server must have a static IP address. Terminal Server clients and Citrix Metaframe Clients are supported over Virtual Private Network (VPN) or direct connections. ...
PPT
... New on Fork-Linearizability Fork Linearizable Byzantine emulation (simplified) - every execution is fork-linearizable - if the server is correct ...
... New on Fork-Linearizability Fork Linearizable Byzantine emulation (simplified) - every execution is fork-linearizable - if the server is correct ...
What is a VPN
... frames, which in turn encapsulate IP, IPX, or NetBEUI protocols With L2TP, the computer performs all security checks and validations, and enables data encryption, which makes it much safer to send information over nonsecure networks by using the new Internet Protocol security (IPSec) In this case da ...
... frames, which in turn encapsulate IP, IPX, or NetBEUI protocols With L2TP, the computer performs all security checks and validations, and enables data encryption, which makes it much safer to send information over nonsecure networks by using the new Internet Protocol security (IPSec) In this case da ...
What is a VPN
... frames, which in turn encapsulate IP, IPX, or NetBEUI protocols With L2TP, the computer performs all security checks and validations, and enables data encryption, which makes it much safer to send information over nonsecure networks by using the new Internet Protocol security (IPSec) In this case da ...
... frames, which in turn encapsulate IP, IPX, or NetBEUI protocols With L2TP, the computer performs all security checks and validations, and enables data encryption, which makes it much safer to send information over nonsecure networks by using the new Internet Protocol security (IPSec) In this case da ...
Hacking Part 1
... “Security Not My Problem”: SNMP read-only mode password is “public” C:\> snmputil walk public
C:\> snmputil walk 10.10.0.2 public .1.3.6.1.4.1.77.1.2.25
Can provide usernames, OS version, share names/paths, running services,
etc.
Countermeasures:
Block TCP/UDP 161 at netwo ...
... “Security Not My Problem”: SNMP read-only mode password is “public” C:\> snmputil walk
עבודה מס` 3 – מבוא לרשתות תקשורת תאריך הגשה : 09.07.08 הגשה בזוגות
... window ARQ protocol with sender window size (SWS) = 2 frames. Assume that receiver window size (RWS) = 1 frame. Note that RWS is the maximum number of out-of-order frames that the receiver is willing to accept. Backup your example with a diagram depicting the messages passing between the sender and ...
... window ARQ protocol with sender window size (SWS) = 2 frames. Assume that receiver window size (RWS) = 1 frame. Note that RWS is the maximum number of out-of-order frames that the receiver is willing to accept. Backup your example with a diagram depicting the messages passing between the sender and ...
Chapter 23 - William Stallings, Data and Computer
... Internet Directory Service and the World Wide Web Life in the modern world is coming to depend more and more upon technical means of communication. Without such technical aids the modern city-state could not exist, for it is only by means of them that trade and business can proceed; that goods and s ...
... Internet Directory Service and the World Wide Web Life in the modern world is coming to depend more and more upon technical means of communication. Without such technical aids the modern city-state could not exist, for it is only by means of them that trade and business can proceed; that goods and s ...
FIT100: Fluency with Information Technology
... • Computers see groups of four number IP addresses -- physical network • Both are ideal for the “users” needs ...
... • Computers see groups of four number IP addresses -- physical network • Both are ideal for the “users” needs ...
Part I: Introduction
... reduction of storage costs, increase in high speed net access from homes, enhancements to caching and introduction of QoS in IP networks ...
... reduction of storage costs, increase in high speed net access from homes, enhancements to caching and introduction of QoS in IP networks ...
Diapositive 1
... Protocol of PPP encapsulation over IP designed by Microsoft Allow to set the virtual private networks (VPNs) over a public network. The protocol opens two channels of communication between the client and server: • a channel control for the management of the ...
... Protocol of PPP encapsulation over IP designed by Microsoft Allow to set the virtual private networks (VPNs) over a public network. The protocol opens two channels of communication between the client and server: • a channel control for the management of the ...
Real-Time Authentication Using Digital Signature Schema
... online shopping, etc. Constant improvements in security is required as internet traffic increases ...
... online shopping, etc. Constant improvements in security is required as internet traffic increases ...
Remote Access Service
... encryption and authentication keys that are used by IPsec. – Authentication header (AH): This provides connectionless integrity and the authentication of data. It also provides protection versus replay attacks. – Encapsulating security payload (ESP): This provides the same services as AH but also pr ...
... encryption and authentication keys that are used by IPsec. – Authentication header (AH): This provides connectionless integrity and the authentication of data. It also provides protection versus replay attacks. – Encapsulating security payload (ESP): This provides the same services as AH but also pr ...
The Internet and Its Uses - Genesee Community College
... __________________________________ is functioning as a server. A server is usually a computer that _________ ___________________ with many client systems. Some servers ____________________________ _________________________ to verify if the user has permission to access the requested data A server so ...
... __________________________________ is functioning as a server. A server is usually a computer that _________ ___________________ with many client systems. Some servers ____________________________ _________________________ to verify if the user has permission to access the requested data A server so ...
Wired communication standards solutions
... 11 What’s reported by the ipconfig command for each connection? On LAN 2 – PCI Card, DHCP is not enabled. A manual IPv4 address, along with a subnet mask, default gateway, and DNS server address are reported. There is no IPv6 information, as you disabled IPv6 on this NIC. On Local Area Connection, D ...
... 11 What’s reported by the ipconfig command for each connection? On LAN 2 – PCI Card, DHCP is not enabled. A manual IPv4 address, along with a subnet mask, default gateway, and DNS server address are reported. There is no IPv6 information, as you disabled IPv6 on this NIC. On Local Area Connection, D ...
VPN tunneling protocols
... Password Authenticated Protocol Shiva Password Authentication Protocol Challenge Handshake Authentication Protocol Microsoft Challenge Handshake Authentication Protocol Microsoft Challenge Handshake Authentication Protocol version 2 – Extensible Authentication Protocol ...
... Password Authenticated Protocol Shiva Password Authentication Protocol Challenge Handshake Authentication Protocol Microsoft Challenge Handshake Authentication Protocol Microsoft Challenge Handshake Authentication Protocol version 2 – Extensible Authentication Protocol ...
A network operating system (NOS) is a computer
... The client–server model of computing is a distributed application structure that partitions tasks or workloads between the providers of a resource or service, called servers, and service requesters, called clients.[1] Often clients and servers communicate over a computer network on separate hardwar ...
... The client–server model of computing is a distributed application structure that partitions tasks or workloads between the providers of a resource or service, called servers, and service requesters, called clients.[1] Often clients and servers communicate over a computer network on separate hardwar ...
Real Time Block Transfer Related Survey
... Corporation-Wide Networking And Distributed Security Windows NT stores account names and passwords in a database called the Security Accounts Manager (SAM) database Network Domains ...
... Corporation-Wide Networking And Distributed Security Windows NT stores account names and passwords in a database called the Security Accounts Manager (SAM) database Network Domains ...
What is WinConnect Server XP?
... over a dial-up or wireless connection, to access the data and Windows applications whenever and wherever it is required. • Remote System Administration WinConnect Server XP is an alternative solution to complement IT staff operations and provide end users with better administration services. The adm ...
... over a dial-up or wireless connection, to access the data and Windows applications whenever and wherever it is required. • Remote System Administration WinConnect Server XP is an alternative solution to complement IT staff operations and provide end users with better administration services. The adm ...
com223-chapter 5
... Commonly used LAN protocols and the network operating systems with which they are used Advantages and disadvantages of LAN protocols Improving LAN performance by using only the protocols necessary in a particular ...
... Commonly used LAN protocols and the network operating systems with which they are used Advantages and disadvantages of LAN protocols Improving LAN performance by using only the protocols necessary in a particular ...
MJ-CV-1 - Snap Tech IT
... Intl Informatics System Avaran (BASA-FAVA Project) – IRAN FAVA is a big network project which support more than 60 company and 120 system administrator with a big central data center and related to main city hall of Isfahan/Iran. ...
... Intl Informatics System Avaran (BASA-FAVA Project) – IRAN FAVA is a big network project which support more than 60 company and 120 system administrator with a big central data center and related to main city hall of Isfahan/Iran. ...
2233 Booth Avenue • Marysville, CA 95901 • (530) 713
... Exchange (PBX) Work with Executone on switchboard issues o Continually monitor network system for changes made (use of software such as, but not limited to, SolarWinds) Attempt to document any changes not communicated o Requested documentation for any simple interim support for items I have prim ...
... Exchange (PBX) Work with Executone on switchboard issues o Continually monitor network system for changes made (use of software such as, but not limited to, SolarWinds) Attempt to document any changes not communicated o Requested documentation for any simple interim support for items I have prim ...
Objectives - cloudfront.net
... Directory integration, Symantec Ghost Solutions 3.1, Microsoft Office 2010-2016/365, IBM DOORS, Microsoft Exchange, Apple Mac Leopard 10.5/Mountain Lion 10.8/10.10.5/Yosemite/El Capitan (10.11.5)/Sierra 10.12.3; Cloud computing, Enterprise Vault, Microsoft SQL server 2000, 2005, 2008 R2, 2012, Inter ...
... Directory integration, Symantec Ghost Solutions 3.1, Microsoft Office 2010-2016/365, IBM DOORS, Microsoft Exchange, Apple Mac Leopard 10.5/Mountain Lion 10.8/10.10.5/Yosemite/El Capitan (10.11.5)/Sierra 10.12.3; Cloud computing, Enterprise Vault, Microsoft SQL server 2000, 2005, 2008 R2, 2012, Inter ...
Visio-Xpert DNC configurations.vsd
... require a Network, and the Comtrol Hub is installed in a central location on the shop floor to minimize the RS-232 cabling distance to each CNC Machine. The Multi-DNC computer is normally connected to CAD/CAM over a LAN so that each CNC controller can get its' files directly from the CAD/CAM worksta ...
... require a Network, and the Comtrol Hub is installed in a central location on the shop floor to minimize the RS-232 cabling distance to each CNC Machine. The Multi-DNC computer is normally connected to CAD/CAM over a LAN so that each CNC controller can get its' files directly from the CAD/CAM worksta ...
Windows Server 2012 Network Setup For TCP/IP
... Printed copies of this document are considered uncontrolled> 19090.2.Rev001 10.09.2013 ...
... Printed copies of this document are considered uncontrolled> 19090.2.Rev001 10.09.2013 ...























