* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download VPN tunneling protocols
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
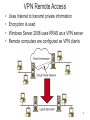
TV Everywhere wikipedia , lookup
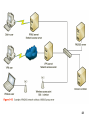
Internet protocol suite wikipedia , lookup
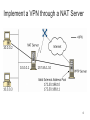
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Server Message Block wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Distributed firewall wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Extensible Authentication Protocol wikipedia , lookup
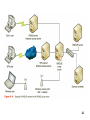
Wireless security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Objectives • Configure Network Access Services in Windows Server 2008 • RADIUS 1 Configuring Remote Access Services in Windows Server 2008 • Dial-up networking – Connects remote users using a phone line • Virtual Private Networks – Allow client connections to your network from remote locations – Works by creating a secure tunnel for transmitting data packets between two points – VPN tunneling protocols: • Point-to-Point Tunneling Protocol (Easiest) • Layer 2 Tunneling Protocol (Require Certificate) • Secure Socket Tunneling Protocol (Only support 2008 or newer client) 2 A VPN Tunnel • • • • Point-to-Point Tunneling Protocol (PPTP) Layer Two Tunneling Protocol (L2TP) IP Security (IPSec) tunnel mode IP-in-IP 3 VPN Remote Access • • • • Uses Internet to transmit private information Encryption is used Windows Server 2008 uses RRAS as a VPN server Remote computers are configured as VPN clients 4 Corporate Internetwork 5 Implement a VPN through a NAT Server 6 Enable and Configure a VPN Server Enabling packet filters should only be chosen if the server has multiple network cards with the filtered card connected to the Internet and the unfiltered cards connected to VPN traffic 7 VPN Protocols • PPTP is the most popular and can function through NAT • L2TP requires IPSec to function • By default, 128 PPTP ports and 128 L2TP ports available – Can increase the number of ports or – Disable a protocol by setting the number of ports to zero • SSTP: New in 2008. Only for Client-Site, not for Site-Site – PPP or L2TP over SSL 8 VPN Protocols (continued) 9 Authentication Protocols 10 Configuring Remote Access Servers • Control authentication and logging. Server and Client must support common protocol to authenticate and connect – – – – – – No Authentication Password Authenticated Protocol Shiva Password Authentication Protocol Challenge Handshake Authentication Protocol Microsoft Challenge Handshake Authentication Protocol Microsoft Challenge Handshake Authentication Protocol version 2 – Extensible Authentication Protocol • Specify whether or not the server is a router for IP, and if it allows IP-based remote access connections 11 • Enable broadcast name resolution Allowing Client Access • By default, none of the users are granted remote access permission • Remote access permission is controlled by their user object – If RRAS does not participate in Active Directory, the user object is stored in the local user account database – If RRAS belongs to an Active Directory domain, the user object is stored in the Active Directory database located on the domain controller 12 Network Access Policies • Control who is allowed to access remotely • Depends on the domain’s functional level (mixed, 2000 native or 2003 native or 2008) • Depend on the machine user is connecting to • Composed of Conditions, Constraints, and Settings – Conditions are criteria that must be met in order for remote access policy to apply to a connection – Allow if met constraints and Deny if not – After conditions and constrains are met, settings are applied to the connection 13 Network Access Policy Evaluation 14 Creating a VPN Client Connection • Configure VPN clients on client machines, e.g. Win XP • Windows Server 2008 can be configured as a VPN client • Create VPN connections using the “New Connection” Wizard in XP or earlier and “Set up a connection or network” wizard in Vista and 2008 – – – – – – Specify IP address (or FQDN) of VPN server Configure whether or not an initial connection is created Configure dialing and redialing options Specify if password and data encryption are required Configure the network configuration for VPN connection Configure an Internet connection firewall and Internet connection sharing 15 Routing and Remote Access and DHCP • Provide remote access clients with IP addresses during a dial-up connection. – Server Assigned IP Address option. • Routing and Remote Access uses DHCP to lease addresses. • DHCP leases are released when Routing and Remote Access is shut down. • Number of leased addresses can be configured. 16 Troubleshooting Remote Access • Software configuration errors by users or administrators – – – – – Incorrect phone numbers and IP addresses Incorrect authentication settings Incorrectly configured network access policies Name resolution is not configured Clients receive incorrect IP options • Best troubleshooting tools include: – – – – Log files (System log) Error messages Network Monitor Ipconfig and Ping command line tools • Hardware errors can also cause problems 17 Hardware Errors • Common hardware troubleshooting tips: – Ensure hardware is on the Microsoft hardware compatibility list – Use ping to determine if the address is reachable – See if you can dial in to a different remote access server – Ensure there is a link light on the network card 18 Resource Kit Utilities • RASLIST.EXE • RASSRVMON.EXE: Monitor Remote Access – Provides: Server, Port, Summary, and Individual Connection information – Alerting set up to run program of choice • RASUSERS.EXE • TRACEENABLE.EXE 19 Introduction to Network Policy Server • Network Policy Server (NPS) – Role service that provides a framework for creating and enforcing network access policies for client health – Can be used to perform: • Configure a RADIUS server • Configure a RADIUS proxy • Configure and implement Network Access Protection (NAP) 20 Introduction to RADIUS • RADIUS – Industry-standard protocol that provides centralized authentication, authorization, and accounting for network access devices • Components of RADIUS – – – – – RADIUS clients VPN server Network access servers RADIUS proxy RADIUS server Perform authentication & authorization User account database 21 22 23 24 Server 2008 NPS Console • NPS Console – Central utility for managing • • • • RADIUS clients and remote RADIUS servers Network health and access policies NAP settings for NAP scenarios Logging settings 25 Server 2008 NPS Console 26 Server 2008 NPS Console 27