* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Diapositive 1
Server Message Block wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Network tap wikipedia , lookup
Wireless security wikipedia , lookup
Extensible Authentication Protocol wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Deep packet inspection wikipedia , lookup
Computer network wikipedia , lookup
Airborne Networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Internet protocol suite wikipedia , lookup
Zero-configuration networking wikipedia , lookup
UniPro protocol stack wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
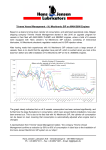
VoWLAN: The Voice over WLAN Maxime Staszewski Fall 2008 - CS 484: Network Concept Agenda • Brief overwiew of VoWLAN • WLAN: • Security issue (Virtual Private Network) • VoIP: • Voice Digitization/Compression • IPv6 • Session Initiation Protocol (SIP) • Conclusion Brief Overwiew of VoWLAN • • • • • • • • VoIP over WLAN Low-cost communication costs Add mobility of phone terminals No permanent connection between the two sides transmits information according to the status of network congestion Slight degradation of communication compared to a fixed line Convergence data/voice Require 802.11 set by the IEEE Virtual Private Network (VPN) • Virtual: connects two “physical” networks (WLANs) by an untrusted link (Internet) • Private: only computers on both sides of the VPN can "see" the data. • Tunneling Protocol: a protocol allowing data from one end of the VPN to another to be secured by encryption algorithms. Virtual Private Network (VPN) • VPN client: the component allowing to encrypt and decrypt data on the user side (client) • VPN server: the component encrypting and decrypting the data on the other side of the organization Virtual Private Network Point-to-point tunneling protocol (PPTP) • • • Protocol of PPP encapsulation over IP designed by Microsoft Allow to set the virtual private networks (VPNs) over a public network. The protocol opens two channels of communication between the client and server: • a channel control for the management of the bond (TCP connection) • a channel carrying data traffic of private network (Protocol Generic Routing Encapsulation) Internet Protocol Security (IPsec) • • • • Set of protocols (Layer 3 of OSI model) using algorithms allowing the transport of secured data over an IP network The purpose of this protocol: authenticate and encrypt the data The stream can only be understood by the final recipient (encryption) Modification of data through intermediaries may not be possible (integrity). Speech digitization methods • Waveform coders: utilize algorithms to produce an output that approximates the input waveform • Vocoding: digitize a compact description of the voice spectrum in several frequency bands. Waveform coders • Use an algorithm to produce an output that approximates the input waveform • Two processes are required to perform digitizing of an analog signal: • Sampling: this discretizes the signal in time • Quantizing: this discretizes the signal in amplitude Pulse Code Modulation (PCM) An uncompressed sampling technique of an analog signal IPv6 (Internet Protocol version 6) • Successor of IPv4 • Ensures QoS better than IPv4 • availability, reliability, timeliness • uses QoS with the help classification and marking of IP packets to make the VoIP infrastructure sure • provides a traffic-class field (8 bits) in the IPv6 header. • has a 20-bit flow label. IPv6 (Internet Protocol version 6) Session Initiation Protocol (SIP) • Open standard protocol of management sessions often used in telecommunications normalized by IETF • Most common for Internet telephony (VoIP) since 2007 • Takes the best aspects of the H.323 protocol. • Handles authentication and location of multiple participants • Responsible for negotiating on the types of media used by the different participants in encapsulating SDP messages (Session Description Protocol). Session Initiation Protocol (SIP) • The basic methods are: • INVITE allows a client to request a new session • ACK confirms the establishment of the session • CANCEL cancels INVITES in abeyance •BYE ends a session in progress • The answer codes are similar to HTTP: • 100 TRYING • 200 OK • 404 not found Session Initiation Protocol (SIP) • The development of SIP is based on three elements: • The User Agents designate the agents found in SIP phones • The Registrar is a server that handles REGISTER requests sent by the User Agent to report their current location • A SIP Proxy serves as an intermediary between User Agents who do not know their respective locations (IP address). Session Initiation Protocol (SIP) Proxy Server SIP Call Flow Conclusion • Potential market growth • Some problems: • Interferences • Quality of voice call •… • Many opportunities • Main competitor; DECT Thank You For Your Attention Questions?