DBA 102:NOW WHAT
... Biggest factor is hardware Must be properly configured Creates abstraction layer between Windows Server and hardware Virtualization layer controls access to physical hardware Host level memory pressure may require minimum memory setting Viable part of High Availability solution, but not the whole so ...
... Biggest factor is hardware Must be properly configured Creates abstraction layer between Windows Server and hardware Virtualization layer controls access to physical hardware Host level memory pressure may require minimum memory setting Viable part of High Availability solution, but not the whole so ...
What can “Economics of Information Security” offer for SMEs
... All the Windows versions and virtual machine platform are available to download using MSDN Guidance in CEHintro.pdf file ...
... All the Windows versions and virtual machine platform are available to download using MSDN Guidance in CEHintro.pdf file ...
PACS Link MIM Security White Paper
... The custom user interface limits the user to the specific functions defined for the product; hence, preventing user access to the operating system’s desktop. Medical Images and DICOM IOD’s are the only files that are transmitted and received over the TCP/IP network using the DICOM protocol. No EMAIL ...
... The custom user interface limits the user to the specific functions defined for the product; hence, preventing user access to the operating system’s desktop. Medical Images and DICOM IOD’s are the only files that are transmitted and received over the TCP/IP network using the DICOM protocol. No EMAIL ...
Document
... Connection of multiple servers across a network To utilise fully requires low cost, high speed bandwidth ...
... Connection of multiple servers across a network To utilise fully requires low cost, high speed bandwidth ...
LAN design issues
... Connection of multiple servers across a network To utilise fully requires low cost, high speed bandwidth ...
... Connection of multiple servers across a network To utilise fully requires low cost, high speed bandwidth ...
Powerpoint - Chapter 13
... Kerberos is an authentication protocol typically used by directory services, such as Active Directory, to provide users with a single network logon capability. Kerberos was developed at the Massachusetts Institute of Technology and is now standardized by the IETF. When a server running Kerberos (cal ...
... Kerberos is an authentication protocol typically used by directory services, such as Active Directory, to provide users with a single network logon capability. Kerberos was developed at the Massachusetts Institute of Technology and is now standardized by the IETF. When a server running Kerberos (cal ...
Week 4 - cda college
... decomposes the problem of building a network into more manageable components. Rather than implementing a monolithic piece of software that does everything you will ever want, you can implement several layers, each of which solves one part of the problem. it provides a more modular design. If you ...
... decomposes the problem of building a network into more manageable components. Rather than implementing a monolithic piece of software that does everything you will ever want, you can implement several layers, each of which solves one part of the problem. it provides a more modular design. If you ...
File
... company has Windows Server 2003 and Red Hat Enterprise Linux servers. The business and sales unit uses Windows XP Professional and Windows 7 Professional workstations. The plant users have a combination of Windows XP professional and Red Hat Linux computers on user’s desktops. The company plans to h ...
... company has Windows Server 2003 and Red Hat Enterprise Linux servers. The business and sales unit uses Windows XP Professional and Windows 7 Professional workstations. The plant users have a combination of Windows XP professional and Red Hat Linux computers on user’s desktops. The company plans to h ...
Chapter 21 PowerPoint Presentation
... Remote Authentication DialIn User Service (RADIUS) • RADIUS provides • Remote user authentication that is vendorindependent. • Scaleable authentication designs for performance. ...
... Remote Authentication DialIn User Service (RADIUS) • RADIUS provides • Remote user authentication that is vendorindependent. • Scaleable authentication designs for performance. ...
9_13_35_JanResume
... To learn the minutest aspect of the work given and to implement it in the best possible way so as to enhance my skills and give better performance to the Organization. And not only to be a part of a successful organization but also to be reason of its success. Professional Strenght ...
... To learn the minutest aspect of the work given and to implement it in the best possible way so as to enhance my skills and give better performance to the Organization. And not only to be a part of a successful organization but also to be reason of its success. Professional Strenght ...
Proposal Student Competition Enhancement
... • A native UNIX Network File-System to share data on the network. • Required package nfs-utils • /etc/init.d/nfs • /etc/exports /ort *(rw,no_root_squash) • Mount the shared nfs file-system: # mount 192.168.10.1:/ort /public ### Can permanently go into /etc/fstab ### ...
... • A native UNIX Network File-System to share data on the network. • Required package nfs-utils • /etc/init.d/nfs • /etc/exports /ort *(rw,no_root_squash) • Mount the shared nfs file-system: # mount 192.168.10.1:/ort /public ### Can permanently go into /etc/fstab ### ...
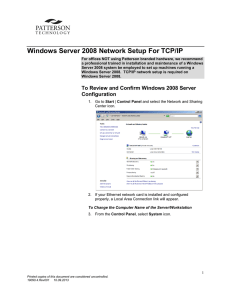
Windows Server 2008 Network Setup For TCP/IP
... Windows Server 2008 Network Setup For TCP/IP For offices NOT using Patterson branded hardware, we recommend a professional trained in installation and maintenance of a Windows Server 2008 system be employed to set up machines running a Windows Server 2008. TCP/IP network setup is required on Windows ...
... Windows Server 2008 Network Setup For TCP/IP For offices NOT using Patterson branded hardware, we recommend a professional trained in installation and maintenance of a Windows Server 2008 system be employed to set up machines running a Windows Server 2008. TCP/IP network setup is required on Windows ...
IBM Spectrum Scale File Protocols
... – in a CES cluster all nodes are homogenous wrt sercives, in 4.1.1 also wrt IPs Node groups are new in 4.2 – Use cases: ...
... – in a CES cluster all nodes are homogenous wrt sercives, in 4.1.1 also wrt IPs Node groups are new in 4.2 – Use cases: ...
Windows Server Installation
... • Set CD-ROM to be a bootable device • Select this option by pressing the key when the systems – Otherwise the computer will start from an already active partition containing an operating system ...
... • Set CD-ROM to be a bootable device • Select this option by pressing the key when the systems – Otherwise the computer will start from an already active partition containing an operating system ...
1992-1995: Bachelor degree in Information Technology with
... In 2011 Dockx-Group started merging and consolidating its subsidiary companies to our new 40000m² business site in Wilrijk. This site consists of new storage, technical and administrative buildings. I was and still am responsible for providing network infrastructure and merging all the different com ...
... In 2011 Dockx-Group started merging and consolidating its subsidiary companies to our new 40000m² business site in Wilrijk. This site consists of new storage, technical and administrative buildings. I was and still am responsible for providing network infrastructure and merging all the different com ...
CHAPTER 3 Classes of Attack
... source IP address to port 19 (chargen port) to the subnet broadcast adress – Affected Windows NT systems respond to each broadcast – Creating a flood of UDP datagrams on the network ...
... source IP address to port 19 (chargen port) to the subnet broadcast adress – Affected Windows NT systems respond to each broadcast – Creating a flood of UDP datagrams on the network ...
document
... Server Message Block Signing • Server Message Block (SMB) protocol – Used when accessing files over network share on Windows server – By default, not secure ...
... Server Message Block Signing • Server Message Block (SMB) protocol – Used when accessing files over network share on Windows server – By default, not secure ...
Curriculum Vitae
... Implementing a Microsoft Windows Server 2003 & Windows Server 2008 Network Infrastructure: Network Hosts… ...
... Implementing a Microsoft Windows Server 2003 & Windows Server 2008 Network Infrastructure: Network Hosts… ...
IST346: Services - Syracuse University
... Unify a set of workstations into a distributed computing environment, since they share common resources. Typical environments have several services, and services often depend on other services. Some services are simple, and have no interaction’s on the user’s part. (network time, or NTP for example) ...
... Unify a set of workstations into a distributed computing environment, since they share common resources. Typical environments have several services, and services often depend on other services. Some services are simple, and have no interaction’s on the user’s part. (network time, or NTP for example) ...
MS Word file
... Chapter 5 Key Points 1. When monitoring memory as it relates to server performance, remember _______________________ the better and consider the size and location of the ___________________________. 2. Match the tool with its purpose Server manager ...
... Chapter 5 Key Points 1. When monitoring memory as it relates to server performance, remember _______________________ the better and consider the size and location of the ___________________________. 2. Match the tool with its purpose Server manager ...
APP-G
... Assignment may be temporary: Address “leased” to a client for a limited time. SENS supports DHCP client, server and relay agent operation ...
... Assignment may be temporary: Address “leased” to a client for a limited time. SENS supports DHCP client, server and relay agent operation ...
Glossary for Ingrasys FISC Servers
... especially since implementation of ISO 9660 interchange levels was more problematic than first perceived. The proposed extensions, System Use Shared Protocol (SUSP), and the Rockridge Interchange Protocol (RRIP), allow for support of multi-platform formats, tables of contents with deeper levels of h ...
... especially since implementation of ISO 9660 interchange levels was more problematic than first perceived. The proposed extensions, System Use Shared Protocol (SUSP), and the Rockridge Interchange Protocol (RRIP), allow for support of multi-platform formats, tables of contents with deeper levels of h ...
Resume - Trelco Limited Company
... May 2001- Dec. 28th 2004-Technical Support Analyst – Sprint Corporation – Kansas City, M0. Responsible for troubleshooting over 2,500 applications within a global network consisting of 77,000 employees and 10,000 servers. The network was a combination of AD, NT, UNIX, Mainframe, Novell, and Windows ...
... May 2001- Dec. 28th 2004-Technical Support Analyst – Sprint Corporation – Kansas City, M0. Responsible for troubleshooting over 2,500 applications within a global network consisting of 77,000 employees and 10,000 servers. The network was a combination of AD, NT, UNIX, Mainframe, Novell, and Windows ...
Field Trip Briefing
... your server, that is, it allows you to create more than one virtual servers for one physical server. ...
... your server, that is, it allows you to create more than one virtual servers for one physical server. ...