Multicasting
... multicastr groups can have an arbitary number of members, traditional reliable protocols require the sender to handle an arbitary number of acknowledgements. This problem is refered to as the ACK Implosion, since no computer has enough processing power to handle this problem. •How to overcome ACk im ...
... multicastr groups can have an arbitary number of members, traditional reliable protocols require the sender to handle an arbitary number of acknowledgements. This problem is refered to as the ACK Implosion, since no computer has enough processing power to handle this problem. •How to overcome ACk im ...
PDF - This Chapter (262.0 KB)
... (NMS). ONS SNMP implementation uses standard Internet Engineering Task Force (IETF) management information bases (MIBs) to convey node-level inventory, fault, and performance management information for generic read-only management of DS-1, DS-3, SONET, and Ethernet technologies. SNMP allows a generi ...
... (NMS). ONS SNMP implementation uses standard Internet Engineering Task Force (IETF) management information bases (MIBs) to convey node-level inventory, fault, and performance management information for generic read-only management of DS-1, DS-3, SONET, and Ethernet technologies. SNMP allows a generi ...
Efficient Way of iSCSI based Remote Storage Service for
... command over IP network[5]. Since the iSCSI protocol can make client access the SCSI I/O devices of server host over an IP Network, client can use the storage of another host transparently without the need to pass server host's file system[6]. In iSCSI layer which is on top of TCP layer, common SCSI ...
... command over IP network[5]. Since the iSCSI protocol can make client access the SCSI I/O devices of server host over an IP Network, client can use the storage of another host transparently without the need to pass server host's file system[6]. In iSCSI layer which is on top of TCP layer, common SCSI ...
IP Multicast
... • The end-router R broadcasts its group membership to the whole network in the form (G, R). • Every router in the network maintains a group membership table with each entry being a tuple [S, G,].
• A sender simply sends data packets as they are available.
• Each router uses the network t ...
... • The end-router R broadcasts its group membership to the whole network in the form (G, R). • Every router in the network maintains a group membership table with each entry being a tuple [S, G,
Quality of Service
... passively watching line traffic – SNMP communication protocol to read out data and set parameters • Polling protocol, manager asks questions & agent responds ...
... passively watching line traffic – SNMP communication protocol to read out data and set parameters • Polling protocol, manager asks questions & agent responds ...
The Design and Implementation of a Next Generation Venugopalan Ramasubramanian
... This decoupling of namespace management from the physical location and ownership of nameservers enables CoDoNS to delegate the same portion of the namespace, say .com, to multiple competing namespace operators. These operators, which are each provided with signing authority over the same space, assi ...
... This decoupling of namespace management from the physical location and ownership of nameservers enables CoDoNS to delegate the same portion of the namespace, say .com, to multiple competing namespace operators. These operators, which are each provided with signing authority over the same space, assi ...
Wing TV-WP2-D11 Netw.. - Celtic-Plus
... applications due to the use of high bandwidth channels. This enables them to deliver a great number of high quality TV programs to all users provided of mobile terminals without limit on the number of users that can enjoy of this services within the coverage area. Thus broadcast technologies represe ...
... applications due to the use of high bandwidth channels. This enables them to deliver a great number of high quality TV programs to all users provided of mobile terminals without limit on the number of users that can enjoy of this services within the coverage area. Thus broadcast technologies represe ...
Seahorse XFp Analyzer User Guide
... Safe operation of the XFp Analyzer requires that all covers be securely attached and plate tray door is closed. This also prevents heat loss and system cooling, which can affect data quality. The door opens automatically when the tray is extended, allowing the operator to insert or remove the assay ...
... Safe operation of the XFp Analyzer requires that all covers be securely attached and plate tray door is closed. This also prevents heat loss and system cooling, which can affect data quality. The door opens automatically when the tray is extended, allowing the operator to insert or remove the assay ...
What Is ASF? Services
... Security is not generally thought of as part of the communication between components within an application. ASF (may) include a security infrastructure designed to transparently intercept and A/A intra-ASF communications. Security into ASF from external clients should be provided at the edge by stan ...
... Security is not generally thought of as part of the communication between components within an application. ASF (may) include a security infrastructure designed to transparently intercept and A/A intra-ASF communications. Security into ASF from external clients should be provided at the edge by stan ...
Multicast Virtual Private Networks
... (SDTV) was upgraded to High Definition Television (HDTV). HDTV bandwidth is increasing even further with 4K and 8K HDTV, the nomenclature coming from the number of vertical pixels. All of this extra bandwidth is challenging those finite communication channels and they must be constantly updated to k ...
... (SDTV) was upgraded to High Definition Television (HDTV). HDTV bandwidth is increasing even further with 4K and 8K HDTV, the nomenclature coming from the number of vertical pixels. All of this extra bandwidth is challenging those finite communication channels and they must be constantly updated to k ...
Address Resolution Protocol
... ARP Caching Because the mapping of IP addresses to media access control (MAC) addresses occurs at each hop (Layer 3 device) on the network for every datagram sent over an internetwork, performance of the network could be compromised. To minimize broadcasts and limit wasteful use of network resources ...
... ARP Caching Because the mapping of IP addresses to media access control (MAC) addresses occurs at each hop (Layer 3 device) on the network for every datagram sent over an internetwork, performance of the network could be compromised. To minimize broadcasts and limit wasteful use of network resources ...
Intermediate System-to-Intermediate System (IS-IS)
... • All routers in the same area must have the same area address. • The system ID must be the same number of octets throughout the domain. • Cisco has implemented a fixed length of 6 octets for the system ID of a NET. • It is customary to use the MAC address of the router, or an IP address of a loopba ...
... • All routers in the same area must have the same area address. • The system ID must be the same number of octets throughout the domain. • Cisco has implemented a fixed length of 6 octets for the system ID of a NET. • It is customary to use the MAC address of the router, or an IP address of a loopba ...
Chapter8 (Internet Protocol)
... The checksum uses one's complement arithmetic to add equal-size sections of the IP header. The complemented result is stored in the checksum field. The receiver also uses one's complement arithmetic to check the header. An IP package can consist of the following: a header-adding module, a proces ...
... The checksum uses one's complement arithmetic to add equal-size sections of the IP header. The complemented result is stored in the checksum field. The receiver also uses one's complement arithmetic to check the header. An IP package can consist of the following: a header-adding module, a proces ...
The History of nordunet
... in 1972) was also building other networks alongside arpanet. These networks used different technologies and were therefore incompatible with each other. To make the interconnection of separate networks possible, darpa established the “Internetting Project” in 1973. The goal of the project was to dev ...
... in 1972) was also building other networks alongside arpanet. These networks used different technologies and were therefore incompatible with each other. To make the interconnection of separate networks possible, darpa established the “Internetting Project” in 1973. The goal of the project was to dev ...
Towards Automated Dynamic Analysis for Linux
... system calls that map memory to determine program behavior. Then, the emulator would need to identify the semantic definition of various memory addresses, and replace the values as appropriate (e.g., a valid ProductID and VendorID). Additionally, due to limited write cycles on the primary storage de ...
... system calls that map memory to determine program behavior. Then, the emulator would need to identify the semantic definition of various memory addresses, and replace the values as appropriate (e.g., a valid ProductID and VendorID). Additionally, due to limited write cycles on the primary storage de ...
Data types
... For each computer with another address, a member of the own network (computer or router) must be found that can send the data into the right direction • This is sometimes wrong • Understanding of network addresses becomes important ...
... For each computer with another address, a member of the own network (computer or router) must be found that can send the data into the right direction • This is sometimes wrong • Understanding of network addresses becomes important ...
Implementation of IPv6 ToS over ATM Network
... called “IPv6 ToS Mapping” is also added to the source. This new attribute allows the user to select the ATM service category to map IPv6’s ToS. At simulation time, depending on the user’s selection, SVC’s of the specified ATM service category will be set up before packets are generated. For example, ...
... called “IPv6 ToS Mapping” is also added to the source. This new attribute allows the user to select the ATM service category to map IPv6’s ToS. At simulation time, depending on the user’s selection, SVC’s of the specified ATM service category will be set up before packets are generated. For example, ...
Institutionen f r systemteknik ö
... A Tactical Data Link (TDL) system has been deployed in many military missions as a winning strategy. The performance of a TDL system is governed by the MAC protocol. The MAC protocol that is able to provide more flexibility and high quality of services is more desirable. However, most MAC protocols ...
... A Tactical Data Link (TDL) system has been deployed in many military missions as a winning strategy. The performance of a TDL system is governed by the MAC protocol. The MAC protocol that is able to provide more flexibility and high quality of services is more desirable. However, most MAC protocols ...
OfficeConnect ADSL Wireless 11g Firewall Router User Guide
... adaptation) without written permission from 3Com Corporation. 3Com Corporation reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of 3Com Corporation to provide notification of such revision or change. 3Com Corporation prov ...
... adaptation) without written permission from 3Com Corporation. 3Com Corporation reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of 3Com Corporation to provide notification of such revision or change. 3Com Corporation prov ...
ST Micro Connect 2 host-target interface
... The ST Micro Connect 2 is a host-target interface for single and multi-core SoCs, providing fast access to host services. It can be used with STMicroelectronics’ development boards as well as customer’s boards. It enables Windows XP, Windows 7 and Red Hat Linux hosts to connect to a target developme ...
... The ST Micro Connect 2 is a host-target interface for single and multi-core SoCs, providing fast access to host services. It can be used with STMicroelectronics’ development boards as well as customer’s boards. It enables Windows XP, Windows 7 and Red Hat Linux hosts to connect to a target developme ...
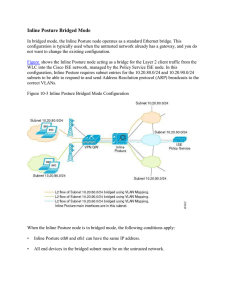
15360608-Inline Posture Bridged Mode
... they provide the rules for the profiles to follow. Access control lists (ACLs) prevent unwanted traffic from entering the network by filtering source and destination IP addresses, transport protocols, and other variables, using the RADIUS protocol. After you create DACLs as named permission objects, ...
... they provide the rules for the profiles to follow. Access control lists (ACLs) prevent unwanted traffic from entering the network by filtering source and destination IP addresses, transport protocols, and other variables, using the RADIUS protocol. After you create DACLs as named permission objects, ...
3rd Edition, Chapter 5
... multiple access protocol: distributed algorithm that determines how stations share channel, i.e., determine when station can transmit communication about channel sharing uses channel itself! what to look for in multiple access protocols: • synchronous or asynchronous • information needed abo ...
... multiple access protocol: distributed algorithm that determines how stations share channel, i.e., determine when station can transmit communication about channel sharing uses channel itself! what to look for in multiple access protocols: • synchronous or asynchronous • information needed abo ...
Z2400 Series User`s Guide
... for signs of misuse. Remove the power cord from the electrical outlet before inspecting it. Refer service or repairs, other than those described in the user documentation, to a professional service person. This product is designed, tested, and approved to meet strict global safety standards with the ...
... for signs of misuse. Remove the power cord from the electrical outlet before inspecting it. Refer service or repairs, other than those described in the user documentation, to a professional service person. This product is designed, tested, and approved to meet strict global safety standards with the ...
Cisco AS5300/Voice Gateway
... Gateway ports, additional Primary Rate Interface (PRI), T1, or E1 interfaces to the PSTN, and a gatekeeper to serve multiple gateways. The Cisco 2600 and 3600 can be utilized as a gatekeeper. The Cisco AS5300/Voice Gateway voice gateway is also interoperable with other vendors’ H.323 gatekeepers. Th ...
... Gateway ports, additional Primary Rate Interface (PRI), T1, or E1 interfaces to the PSTN, and a gatekeeper to serve multiple gateways. The Cisco 2600 and 3600 can be utilized as a gatekeeper. The Cisco AS5300/Voice Gateway voice gateway is also interoperable with other vendors’ H.323 gatekeepers. Th ...