Model Answers Mid-Semester Test 2010
... Which of the OSI Layers handles each of the following: a. Dividing the transmitted bit stream into frames. Data Link Layer b. Determining which route through the subnet to use? Network Layer ...
... Which of the OSI Layers handles each of the following: a. Dividing the transmitted bit stream into frames. Data Link Layer b. Determining which route through the subnet to use? Network Layer ...
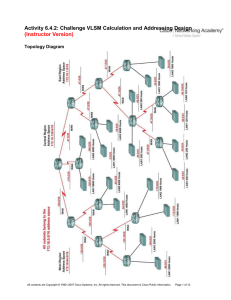
2e_06_6_4_2_vlsm_instr
... All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. ...
... All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. ...
PDF
... Monitoring the user experience end-to-end and gaining better control of endpoints, with MSI. Today’s networks have difficulty differentiating the traffic flows (voice, video, data, and signaling) sent by different devices, appliances, and applications. This lack of differentiation complicates bandwi ...
... Monitoring the user experience end-to-end and gaining better control of endpoints, with MSI. Today’s networks have difficulty differentiating the traffic flows (voice, video, data, and signaling) sent by different devices, appliances, and applications. This lack of differentiation complicates bandwi ...
Coding and Error Control
... – Devices working together for data analysis and automated control Bluetooth and IEEE 802.15 12-3 ...
... – Devices working together for data analysis and automated control Bluetooth and IEEE 802.15 12-3 ...
Cisco Unified Border Element 1.3
... Configurable SIP Profiles on the Cisco Unified Border Element help customers by allowing SIP messages from entities in their network to pass through the border element and have header fields and the embedded SDP manipulated. This configurability allows for more endpoints to interconnect by acting as ...
... Configurable SIP Profiles on the Cisco Unified Border Element help customers by allowing SIP messages from entities in their network to pass through the border element and have header fields and the embedded SDP manipulated. This configurability allows for more endpoints to interconnect by acting as ...
NION CobraNet Hardware Manual Version 1.7.1.0 July 23, 2014
... Important network considerations This product is designed to operate on a network backbone or infrastructure. The design, implementation and maintenance of this infrastructure is critical to correct operation and performance of the product. Peavey Electronics Corp does not support nor service networ ...
... Important network considerations This product is designed to operate on a network backbone or infrastructure. The design, implementation and maintenance of this infrastructure is critical to correct operation and performance of the product. Peavey Electronics Corp does not support nor service networ ...
Volume B Equity Market Trading and Information Network
... If join’s on the network devices are necessary they should be changed to “IP IGMP static-group” commands and not be “IP IGMP join-group” commands. (Multicast fast switching cannot happen on an interface with “join-group” commands on it. ...
... If join’s on the network devices are necessary they should be changed to “IP IGMP static-group” commands and not be “IP IGMP join-group” commands. (Multicast fast switching cannot happen on an interface with “join-group” commands on it. ...
re-feedback - Bob Briscoe
... • example #2: tiered QoS at flat rates, each with congestion quota throttle • subscription effectively buys congestion quotas for a set of tiers • higher tiers can use a higher weight policer (more permissive) • applications configured to use a relevant tier (QoS class) • the more of each quota is u ...
... • example #2: tiered QoS at flat rates, each with congestion quota throttle • subscription effectively buys congestion quotas for a set of tiers • higher tiers can use a higher weight policer (more permissive) • applications configured to use a relevant tier (QoS class) • the more of each quota is u ...
Lifesize UVC Platform™ Installation and Deployment Guide
... 1. Position a chassis rail guide (rack rail) in the appropriate location in the rack. Make certain the sliding rail guide faces the inside of the rack. 2. Use the following items to secure the assembly to the rack: ...
... 1. Position a chassis rail guide (rack rail) in the appropriate location in the rack. Make certain the sliding rail guide faces the inside of the rack. 2. Use the following items to secure the assembly to the rack: ...
Cisco Inter-network Operating System (IOS) A short guide for the
... The network-number identifies the network using OSPF. The mask tells which bits to use from the network-number, and the area-id is used for determining areas in an OSPF configuration. Example: Router(config-router)#network 192.168.10.0 255.255.255.0 area 0.0.0.0 Repeat this step for all the network ...
... The network-number identifies the network using OSPF. The mask tells which bits to use from the network-number, and the area-id is used for determining areas in an OSPF configuration. Example: Router(config-router)#network 192.168.10.0 255.255.255.0 area 0.0.0.0 Repeat this step for all the network ...
PDF
... businesses face complex implementation challenges when trying to split inbound and outbound traffic across multiple links while ensuring continuous network availability. This complexity increases further when these connections are from different service providers or have different characteristics su ...
... businesses face complex implementation challenges when trying to split inbound and outbound traffic across multiple links while ensuring continuous network availability. This complexity increases further when these connections are from different service providers or have different characteristics su ...
RoamAbout 802.11 Wireless Networking Guide
... email address: [email protected] Make sure to include the document Part Number in the email message. ...
... email address: [email protected] Make sure to include the document Part Number in the email message. ...
FortiOS™ Handbook - Advanced Routing for FortiOS 5.2
... To add or edit a static route, go to Router > Static > Static Routes and select Create New. ...
... To add or edit a static route, go to Router > Static > Static Routes and select Create New. ...
3rd Edition, Chapter 5
... 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully utilize channel ...
... 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully utilize channel ...
Fax over IP recommendations
... Since e-mail has become established, the fax has been declared obsolete time and again. Nevertheless, countless analogue fax machines are still in use worldwide today. In Switzerland alone, the figure is still 500,000. In principle, these can continue being used with IP telephony connections – howev ...
... Since e-mail has become established, the fax has been declared obsolete time and again. Nevertheless, countless analogue fax machines are still in use worldwide today. In Switzerland alone, the figure is still 500,000. In principle, these can continue being used with IP telephony connections – howev ...
ISSN: XXXX-XXXX, p ISSN
... Peer-to-peer (P2P) botnets have recently been adopted by botmasters for their resiliency against takedown efforts. Besides being harder to take down, modern botnets tend to be stealthier in the way they perform malicious activities, making current detection approaches ineffective. In addition, the r ...
... Peer-to-peer (P2P) botnets have recently been adopted by botmasters for their resiliency against takedown efforts. Besides being harder to take down, modern botnets tend to be stealthier in the way they perform malicious activities, making current detection approaches ineffective. In addition, the r ...
Description
... The purchased products, services and features are stipulated by the contract made between Huawei and the customer. All or part of the products, services and features described in this document may not be within the purchase scope or the usage scope. Unless otherwise specified in the contract, all st ...
... The purchased products, services and features are stipulated by the contract made between Huawei and the customer. All or part of the products, services and features described in this document may not be within the purchase scope or the usage scope. Unless otherwise specified in the contract, all st ...
Why Latency Lags Bandwidth, and What it Means to Computing
... multiple replicas of data at remote sites Caching (obviously) to reducing latency Replication: multiple requests to multiple copies and just use the quickest reply Prefetching to reduce latency Large block sizes for disk and memory Protocol: few very large messages – vs. chatty protocol with lots sm ...
... multiple replicas of data at remote sites Caching (obviously) to reducing latency Replication: multiple requests to multiple copies and just use the quickest reply Prefetching to reduce latency Large block sizes for disk and memory Protocol: few very large messages – vs. chatty protocol with lots sm ...
Presentation
... multiple replicas of data at remote sites Caching (obviously) to reducing latency Replication: multiple requests to multiple copies and just use the quickest reply Prefetching to reduce latency Large block sizes for disk and memory Protocol: few very large messages – vs. chatty protocol with lots sm ...
... multiple replicas of data at remote sites Caching (obviously) to reducing latency Replication: multiple requests to multiple copies and just use the quickest reply Prefetching to reduce latency Large block sizes for disk and memory Protocol: few very large messages – vs. chatty protocol with lots sm ...
Presentation Title Size 30PT
... Is the existing CCNA v3.1 curriculum very difficult for your students in terms of theoretical topics? CCNA Discovery Yes, the current CCNA curriculum is very difficult ...
... Is the existing CCNA v3.1 curriculum very difficult for your students in terms of theoretical topics? CCNA Discovery Yes, the current CCNA curriculum is very difficult ...
Active Mapping - University of California, Berkeley
... number of drawbacks. One is performance: the normalizer must be able to reconstruct every TCP stream in real-time. Another is robustness: since the normalizer is in the forwarding path of every packet, it must be extremely reliable even in the face of resource exhaustion; it also must be resistant t ...
... number of drawbacks. One is performance: the normalizer must be able to reconstruct every TCP stream in real-time. Another is robustness: since the normalizer is in the forwarding path of every packet, it must be extremely reliable even in the face of resource exhaustion; it also must be resistant t ...
M T ASTER’S HESIS
... Introduction to Multicasting Multicasting allows us to send a data packet to multiple sites at the same time. The key here is the ability to send one message to one or more nodes in a single operation. This provides a tremendous amount of savings in bandwidth when compared to traditional unicast tra ...
... Introduction to Multicasting Multicasting allows us to send a data packet to multiple sites at the same time. The key here is the ability to send one message to one or more nodes in a single operation. This provides a tremendous amount of savings in bandwidth when compared to traditional unicast tra ...
PRAISE FOR IP STORAGE NETWORKING: STRAIGHT
... Straight to the Core walks the reader through both the how and why of IP and Ethernet's flexibility.” —Larry Boucher, CEO, Alacritech “Orenstein communicates complex storage architecture concepts effortlessly. Unlike traditional storage networking analysis, IP Storage Networking: Straight to the Cor ...
... Straight to the Core walks the reader through both the how and why of IP and Ethernet's flexibility.” —Larry Boucher, CEO, Alacritech “Orenstein communicates complex storage architecture concepts effortlessly. Unlike traditional storage networking analysis, IP Storage Networking: Straight to the Cor ...
Cisco Nexus 1000V for Microsoft Hyper-V
... Gunnar Anderson, Product Marketing Manager, Cloud Networking & Services, Cisco Appaji Malla, Sr. Product Marketing Manager, Cloud Networking & Services, Cisco Sai Chaitanya, Technical Marketing Engineer, Cloud Networking & Services, Cisco ...
... Gunnar Anderson, Product Marketing Manager, Cloud Networking & Services, Cisco Appaji Malla, Sr. Product Marketing Manager, Cloud Networking & Services, Cisco Sai Chaitanya, Technical Marketing Engineer, Cloud Networking & Services, Cisco ...