Data Sheet UMUX NEBRA/NEBRO
... Hence UMUX network elements can be smoothly upgraded to support new broadband Ethernet services. ...
... Hence UMUX network elements can be smoothly upgraded to support new broadband Ethernet services. ...
Introduction to IPv6
... IPv6 can offer new opportunities as it eliminates NAT: Example: AJAX applications, Multimedia. You would need to give IPv6 Support to Software that runs on top of IP or that handle IP addresses. Example: ODBC, JDBC drivers upgrade, Database tables, log. ...
... IPv6 can offer new opportunities as it eliminates NAT: Example: AJAX applications, Multimedia. You would need to give IPv6 Support to Software that runs on top of IP or that handle IP addresses. Example: ODBC, JDBC drivers upgrade, Database tables, log. ...
ORiNOCO 802.11a/b/g/n USB Adapter
... 802.11n wireless products as well as legacy products. The ORiNOCO® 11n USB Adapter can be used with other 802.11n devices to form a stand-alone wireless Peer-to-Peer Group or used in conjunction with an Access Point infrastructure to provide mobile clients with wireless access. ...
... 802.11n wireless products as well as legacy products. The ORiNOCO® 11n USB Adapter can be used with other 802.11n devices to form a stand-alone wireless Peer-to-Peer Group or used in conjunction with an Access Point infrastructure to provide mobile clients with wireless access. ...
Offset Time-Emulated Architecture for Optical Burst Switching - Modelling and Performance Evaluation
... demand due to the introduction of broadband Internet access and new end-user business applications as well as the continuing paradigm shift from voice to data services. These trends have emerged at the same time as the advance in optical technologies which has enabled the development of high-capacit ...
... demand due to the introduction of broadband Internet access and new end-user business applications as well as the continuing paradigm shift from voice to data services. These trends have emerged at the same time as the advance in optical technologies which has enabled the development of high-capacit ...
Network Working Group G. Bernstein Request for
... There are currently two different multiplexing technologies in use in optical networks: wavelength-division multiplexing (WDM) and time division multiplexing (TDM). This work focuses on TDM technology. SDH and SONET are two TDM standards widely used by operators to transport and multiplex different ...
... There are currently two different multiplexing technologies in use in optical networks: wavelength-division multiplexing (WDM) and time division multiplexing (TDM). This work focuses on TDM technology. SDH and SONET are two TDM standards widely used by operators to transport and multiplex different ...
Session MI.1 - PW/MPLS
... Multi-segment PWs require extensions to single segment PW OAM to allow: Segmented OAM (between 1 or more T/S-PEs) Propagation of defect notifications between PW segments & ingress/egress tunnels ...
... Multi-segment PWs require extensions to single segment PW OAM to allow: Segmented OAM (between 1 or more T/S-PEs) Propagation of defect notifications between PW segments & ingress/egress tunnels ...
Cisco ANA VNE Drivers Data Sheet
... SNMP traps, and syslogs. SNMP traps can be imported through MIB files. These extensions can be done by customers or by the system integrator local to the ANA installation and do not affect the delivered ANA software. ...
... SNMP traps, and syslogs. SNMP traps can be imported through MIB files. These extensions can be done by customers or by the system integrator local to the ANA installation and do not affect the delivered ANA software. ...
ZigBee: Home Wireless Control Made Simple
... • ZigBee is designed to be a low power, low cost, low data rate, wireless solution. • ZigBee relies upon the robust IEEE 802.15.4 PHY/MAC to provide reliable data transfer in noisy, interference-rich environments • ZigBee layers on top of 15.4 with Mesh Networking, Security, and Applications control ...
... • ZigBee is designed to be a low power, low cost, low data rate, wireless solution. • ZigBee relies upon the robust IEEE 802.15.4 PHY/MAC to provide reliable data transfer in noisy, interference-rich environments • ZigBee layers on top of 15.4 with Mesh Networking, Security, and Applications control ...
Network Security Appliance Series
... chosen to compromise their security by turning off features to maintain network performance. Now your organization can be both secure and productive without compromising network performance. The Dell™ SonicWALL™ Network Security Appliance (NSA) Series next-generation firewalls (NGFWs) delivers a dee ...
... chosen to compromise their security by turning off features to maintain network performance. Now your organization can be both secure and productive without compromising network performance. The Dell™ SonicWALL™ Network Security Appliance (NSA) Series next-generation firewalls (NGFWs) delivers a dee ...
Ayodele Damola
... Thanks to my industrial supervisor at Ericsson Mr. Hans Mickelsson first for selecting me for this thesis project and for his continuous help and support along the whole way. Thank you Hans. Thanks to Mr. Jan Söderström for the opportunity to do my project at Ericsson Research. Thanks to Mr. Torbjör ...
... Thanks to my industrial supervisor at Ericsson Mr. Hans Mickelsson first for selecting me for this thesis project and for his continuous help and support along the whole way. Thank you Hans. Thanks to Mr. Jan Söderström for the opportunity to do my project at Ericsson Research. Thanks to Mr. Torbjör ...
view pdf - Christoph Sommer and Falko Dressler: Vehicular
... ▪ These slides are designed to accompany a lecture based on the textbook “Vehicular Networking” by Christoph Sommer and Falko Dressler, published in December 2014 by Cambridge University Press. ▪ Except where otherwise noted (e.g., logos and cited works) this slide deck is Copyright © 2009‐2015 C ...
... ▪ These slides are designed to accompany a lecture based on the textbook “Vehicular Networking” by Christoph Sommer and Falko Dressler, published in December 2014 by Cambridge University Press. ▪ Except where otherwise noted (e.g., logos and cited works) this slide deck is Copyright © 2009‐2015 C ...
SNMP Tutorial
... sysUpTime OBJECT-TYPE SYNTAX INTEGER ACCESS read-only STATUS mandatory DESCRIPTION “The time (in hundredths of a second) since the network management portion of the system was last re-initialized.” ...
... sysUpTime OBJECT-TYPE SYNTAX INTEGER ACCESS read-only STATUS mandatory DESCRIPTION “The time (in hundredths of a second) since the network management portion of the system was last re-initialized.” ...
MPLS QoS - Lyle School of Engineering
... – With pure datagram routing, overhead of carrying complete explicit route is prohibitive – MPLS allows explicit route to be carried only at the time the LSP is setup, and not with each packet – MPLS makes explicit routing practical ...
... – With pure datagram routing, overhead of carrying complete explicit route is prohibitive – MPLS allows explicit route to be carried only at the time the LSP is setup, and not with each packet – MPLS makes explicit routing practical ...
Chapter 9
... one end of the network to listen for the signal from another device at the other end of the network. Without being able to detect the signal from the first device soon enough, the second device will transmit and cause collision. ...
... one end of the network to listen for the signal from another device at the other end of the network. Without being able to detect the signal from the first device soon enough, the second device will transmit and cause collision. ...
IAS Router Common Criteria Operator Guidance
... NIAP Common Criteria validation: HTTPS/TLS. Whereas these protocols may provide authentication, integrity, and confidentiality there is no assurance assigned to their use within this evaluation. Instructions within this guidance document will guide the administrator how to use those protocols which ...
... NIAP Common Criteria validation: HTTPS/TLS. Whereas these protocols may provide authentication, integrity, and confidentiality there is no assurance assigned to their use within this evaluation. Instructions within this guidance document will guide the administrator how to use those protocols which ...
Release Notes for RingMaster Version 7.7.3.1
... Juniper sends two kinds of tokens electronically, in e-mail, in response to ordered licenses: Software Serial Numbers, and Authorization Codes. Software Serial numbers are sent when you order a base system (e.g., WLM-RTMS). Authorization Codes ( "AuthCodes") are sent when an additional capacity or f ...
... Juniper sends two kinds of tokens electronically, in e-mail, in response to ordered licenses: Software Serial Numbers, and Authorization Codes. Software Serial numbers are sent when you order a base system (e.g., WLM-RTMS). Authorization Codes ( "AuthCodes") are sent when an additional capacity or f ...
Product Description
... Multiservice bearing capability ........................................................................... 15 TDM service....................................................................................................... 16 ATM service ........................................................... ...
... Multiservice bearing capability ........................................................................... 15 TDM service....................................................................................................... 16 ATM service ........................................................... ...
Universal WiFi Range Extender WN3000RP
... 2. The Extender acts as an access point for computers. The Extender has its own wireless network called NETGEAR_EXT that wireless computers can join. In its role as an access point, the Extender performs tasks that wireless routers do, such as broadcasting its network name (SSID). The Extender must ...
... 2. The Extender acts as an access point for computers. The Extender has its own wireless network called NETGEAR_EXT that wireless computers can join. In its role as an access point, the Extender performs tasks that wireless routers do, such as broadcasting its network name (SSID). The Extender must ...
Advanced Networking: Network Address Translation (NAT)
... device to avoid inconsistent assignments to pieces of the same packet • End-to-end connectivity: – NAT destroys universal end-to-end reachability of hosts on the Internet – A host in the public Internet often cannot initiate communication to a host in a private network – The problem is worse, when t ...
... device to avoid inconsistent assignments to pieces of the same packet • End-to-end connectivity: – NAT destroys universal end-to-end reachability of hosts on the Internet – A host in the public Internet often cannot initiate communication to a host in a private network – The problem is worse, when t ...
Cloud Management Software/Platforms
... (such as setting up bridging interfaces or changing iptables rules). This functionality is being migrated to Neutron, a separate OpenStack project. In the Folsom release, much of the functionality will be duplicated between nova-network and Neutron. The nova-schedule process is conceptually the simp ...
... (such as setting up bridging interfaces or changing iptables rules). This functionality is being migrated to Neutron, a separate OpenStack project. In the Folsom release, much of the functionality will be duplicated between nova-network and Neutron. The nova-schedule process is conceptually the simp ...
Cisco ASA 5500 Series SSL/IPsec VPN Edition
... AnyConnect VPN Client, an automatically downloadable network-tunneling client that provides access to virtually any application or resource. Optimized Network Performance: The Cisco AnyConnect VPN Client provides an optimized VPN connection for latencysensitive traffic, such as voice over IP (VoIP) ...
... AnyConnect VPN Client, an automatically downloadable network-tunneling client that provides access to virtually any application or resource. Optimized Network Performance: The Cisco AnyConnect VPN Client provides an optimized VPN connection for latencysensitive traffic, such as voice over IP (VoIP) ...
p2p
... ZIGZAG distribute media content to many clients by organizing them into an appropriate tree. This tree routed at the server and including all and only the receivers. The subset of receivers get content directly from source and others get it from the receivers in the upstream. ...
... ZIGZAG distribute media content to many clients by organizing them into an appropriate tree. This tree routed at the server and including all and only the receivers. The subset of receivers get content directly from source and others get it from the receivers in the upstream. ...
Multicast Basic Concept
... • Unicast: point to point communication • Broadcast: packets are sent to all – IP supports broadcasting, but the use of broadcasts is strictly limited. – Protocols require broadcasts only when there is no alternative – Routers limit broadcasts to the local network or subnet, preventing broadcasts fo ...
... • Unicast: point to point communication • Broadcast: packets are sent to all – IP supports broadcasting, but the use of broadcasts is strictly limited. – Protocols require broadcasts only when there is no alternative – Routers limit broadcasts to the local network or subnet, preventing broadcasts fo ...
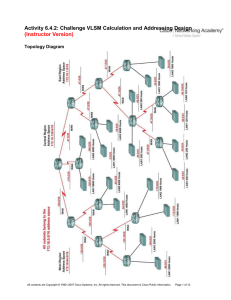
2e_06_6_4_2_vlsm_instr
... All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. ...
... All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. ...