Tema 1: Tecnologías LAN. - GRC
... IP Protocol Suite - the most predominant networking technology. Voice & Data convergence on a single network infrastructure. Continual increase in number of users. Demand for higher connection speeds. Increase in traffic volumes. Ever-increasing number of ISP networks. ...
... IP Protocol Suite - the most predominant networking technology. Voice & Data convergence on a single network infrastructure. Continual increase in number of users. Demand for higher connection speeds. Increase in traffic volumes. Ever-increasing number of ISP networks. ...
Solaris 10 - Center for Internet Security
... Background. The Center for Internet Security ("CIS") provides benchmarks, scoring tools, software, data, information, suggestions, ideas, and other services and materials from the CIS website or elsewhere (“Products”) as a public service to Internet users worldwide. Recommendations contained in the ...
... Background. The Center for Internet Security ("CIS") provides benchmarks, scoring tools, software, data, information, suggestions, ideas, and other services and materials from the CIS website or elsewhere (“Products”) as a public service to Internet users worldwide. Recommendations contained in the ...
Drafting Behind Akamai - Northwestern University
... • Publish the results through DNS over short time scales ...
... • Publish the results through DNS over short time scales ...
FTTx PON Guide Testing Passive Optical Networks
... that RBOCs can invest in last-mile fiber network—without having to share it with competitors−providing a major incentive toward the deployment of FTTx networks. Some predict a US$1 billion market for FTTx networks, for RBOCs alone. ...
... that RBOCs can invest in last-mile fiber network—without having to share it with competitors−providing a major incentive toward the deployment of FTTx networks. Some predict a US$1 billion market for FTTx networks, for RBOCs alone. ...
Towards Automated Dynamic Analysis for Linux
... system calls that map memory to determine program behavior. Then, the emulator would need to identify the semantic definition of various memory addresses, and replace the values as appropriate (e.g., a valid ProductID and VendorID). Additionally, due to limited write cycles on the primary storage de ...
... system calls that map memory to determine program behavior. Then, the emulator would need to identify the semantic definition of various memory addresses, and replace the values as appropriate (e.g., a valid ProductID and VendorID). Additionally, due to limited write cycles on the primary storage de ...
9.4.2 CSMA/CD – The Process
... of directly connected hubs make up what is known as a collision domain. A collision domain is also referred to as a network segment. Hubs and repeaters therefore have the effect of increasing the size of the collision domain. ...
... of directly connected hubs make up what is known as a collision domain. A collision domain is also referred to as a network segment. Hubs and repeaters therefore have the effect of increasing the size of the collision domain. ...
Campuswide VLAN
... Single or multiple ELANs Wire speed Layer 3 into the core Enterprise servers on Fast Ethernet ...
... Single or multiple ELANs Wire speed Layer 3 into the core Enterprise servers on Fast Ethernet ...
vipersat file streamer user guide
... protocol rather than using TCP, a common standard for computer communications. The advantages that TCP/IP provides for typical internet communications can become limitations when passing traffic over a satellite network, where inherent delays can be mistaken for congestion or low bandwidth, resultin ...
... protocol rather than using TCP, a common standard for computer communications. The advantages that TCP/IP provides for typical internet communications can become limitations when passing traffic over a satellite network, where inherent delays can be mistaken for congestion or low bandwidth, resultin ...
Archer_C2600_UG_V1 - TP-Link
... Featuring four fixed external antennas and high power amplifiers, Archer C2600 is able to boost Wi-Fi coverage throughout your home. Advanced Beamforming technology enables Archer C2600 to focus Wi-Fi signal to connected devices, delivering a more targeted and highly efficient wireless connection. ...
... Featuring four fixed external antennas and high power amplifiers, Archer C2600 is able to boost Wi-Fi coverage throughout your home. Advanced Beamforming technology enables Archer C2600 to focus Wi-Fi signal to connected devices, delivering a more targeted and highly efficient wireless connection. ...
S9700 Series Terabit Routing Switches
... conferencing, wireless access. In addition, the S9700 also provides a variety of reliability technologies including in-service software upgrade, non-stop forwarding, hardware OAM/BFD, and ring network protection. These technologies improve customers' network efficiency and maximize the normal operat ...
... conferencing, wireless access. In addition, the S9700 also provides a variety of reliability technologies including in-service software upgrade, non-stop forwarding, hardware OAM/BFD, and ring network protection. These technologies improve customers' network efficiency and maximize the normal operat ...
Networks and Network Security - Nicolas T. COURTOIS` research in
... hard to make it work with existing firewalls etc.. IPSEC has no defenses against network traffic analysis Gollman: IPSEC violates two design principles of the Internet: network should be: • stateless: in IPSEC network nodes to work synchronized • unreliable: however in IPSEC there are problems if pa ...
... hard to make it work with existing firewalls etc.. IPSEC has no defenses against network traffic analysis Gollman: IPSEC violates two design principles of the Internet: network should be: • stateless: in IPSEC network nodes to work synchronized • unreliable: however in IPSEC there are problems if pa ...
Industrial ETHERNET
... you to our product recommendation in four fast, simple steps. It makes no difference whether it’s a matter of connectors, Industrial ETHERNET components or FiberINTERFACES. You select area of application, product category, criteria and requirements – and immediately receive our individual ...
... you to our product recommendation in four fast, simple steps. It makes no difference whether it’s a matter of connectors, Industrial ETHERNET components or FiberINTERFACES. You select area of application, product category, criteria and requirements – and immediately receive our individual ...
Vipersat CDM-570/570L
... reproduced without prior written permission of Comtech EF Data, Inc. IMPORTANT NOTE: The information contained in this document supersedes all previously published information regarding this product. Product specifications are subject to change without prior notice. Comtech reserves the right to rev ...
... reproduced without prior written permission of Comtech EF Data, Inc. IMPORTANT NOTE: The information contained in this document supersedes all previously published information regarding this product. Product specifications are subject to change without prior notice. Comtech reserves the right to rev ...
Reference Manual for the 54 Mbps Wireless Router WGR614 v6 202-10099-01, April 2005
... NETGEAR is a trademark of Netgear, Inc. Microsoft, Windows, and Windows NT are registered trademarks of Microsoft Corporation. Other brand and product names are registered trademarks or trademarks of their respective holders. Statement of Conditions In the interest of improving internal design, oper ...
... NETGEAR is a trademark of Netgear, Inc. Microsoft, Windows, and Windows NT are registered trademarks of Microsoft Corporation. Other brand and product names are registered trademarks or trademarks of their respective holders. Statement of Conditions In the interest of improving internal design, oper ...
Architectures and Algorithms for IPv4/IPv6
... algorithm. It is suitable to use in simulation as its behaviour tends to be closer to the behaviour of real networks since it does not overload unnecessarily some links more than others. It may also be used in machines where the computation of paths is Dijkstra based and situations of equal-cost rou ...
... algorithm. It is suitable to use in simulation as its behaviour tends to be closer to the behaviour of real networks since it does not overload unnecessarily some links more than others. It may also be used in machines where the computation of paths is Dijkstra based and situations of equal-cost rou ...
IPv6 Deployment Status in KT/Korea
... strategy council driven by MIC • No Telco’s are now ready to deploy IPv6 as they see IPv6 as business, not as infrastructure upgrade • They’re still research-oriented even though they have IPv6 deployment plans – KT, SKT, etc KT Future Technology Laboratory ...
... strategy council driven by MIC • No Telco’s are now ready to deploy IPv6 as they see IPv6 as business, not as infrastructure upgrade • They’re still research-oriented even though they have IPv6 deployment plans – KT, SKT, etc KT Future Technology Laboratory ...
TESI DOCTORAL Àlex Vallejo Blanxart
... It is true, a thesis is a very long and lonely journey, but not all the way. It would have been impossible to carry out this thesis without the collaboration of many people. Some of them just helped a bit at some crucial points, some have been around transversally, some we have never met in real lif ...
... It is true, a thesis is a very long and lonely journey, but not all the way. It would have been impossible to carry out this thesis without the collaboration of many people. Some of them just helped a bit at some crucial points, some have been around transversally, some we have never met in real lif ...
TCP operations
... trusted, which is not the case in the current commercial Internet. The statement secure comes from the time, when TCP/IP was primarily used for Military purposes. TCP provides reliable services on top of a less reliable internet communication systems on following areas [4]: ...
... trusted, which is not the case in the current commercial Internet. The statement secure comes from the time, when TCP/IP was primarily used for Military purposes. TCP provides reliable services on top of a less reliable internet communication systems on following areas [4]: ...
FOCUS Technical Report
... primitives to the switches. This design offers limited flexibility but provides the best performance. Unfortunately, it requires modifications to hardware switches – a feat that is not easily achieved. Thus today, most datacenters explore a middle ground by turning on the legacy protocols on switch ...
... primitives to the switches. This design offers limited flexibility but provides the best performance. Unfortunately, it requires modifications to hardware switches – a feat that is not easily achieved. Thus today, most datacenters explore a middle ground by turning on the legacy protocols on switch ...
Cisco IP SLA`s
... IP SLA for Voice over IP • VoIP may be difficult to deploy when the network behavior is not well understood Cisco IOS IP SLAs will verify network readiness and QoS Measure critical performance for VoIP deployment Real time warning of network performance degradation IP SLA is universally available a ...
... IP SLA for Voice over IP • VoIP may be difficult to deploy when the network behavior is not well understood Cisco IOS IP SLAs will verify network readiness and QoS Measure critical performance for VoIP deployment Real time warning of network performance degradation IP SLA is universally available a ...
What Is a Virtual Private Network?
... Communications. Like L2F, PPTP allows the tunneling of remote access client PPP frames between a NAS and a VPN gateway/concentrator. PPTP also allows a tunnel to be set up directly from a remote access client to a VPN gateway/concentrator. PPP encapsulated packets carried over PPTP tunnels are often ...
... Communications. Like L2F, PPTP allows the tunneling of remote access client PPP frames between a NAS and a VPN gateway/concentrator. PPTP also allows a tunnel to be set up directly from a remote access client to a VPN gateway/concentrator. PPP encapsulated packets carried over PPTP tunnels are often ...
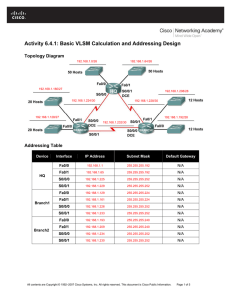
Activity 6.4.1: Basic VLSM Calculation and Addressing Design
... 4. What is the maximum number of host IP addresses that are needed for a single subnet? _______ 5. What is the least number of host IP addresses that are needed for a single subnet? _______ 6. How many IP addresses are needed for the East portion of the network? Be sure to include the WAN links betw ...
... 4. What is the maximum number of host IP addresses that are needed for a single subnet? _______ 5. What is the least number of host IP addresses that are needed for a single subnet? _______ 6. How many IP addresses are needed for the East portion of the network? Be sure to include the WAN links betw ...
Ch11
... 11-7 DISTANCE VECTOR ROUTING Distance vector and link state routing are both interior routing protocols. They can be used inside an autonomous system. Both of these routing protocols become intractable when the domain of operation becomes large. Distance vector routing is subject to instability if ...
... 11-7 DISTANCE VECTOR ROUTING Distance vector and link state routing are both interior routing protocols. They can be used inside an autonomous system. Both of these routing protocols become intractable when the domain of operation becomes large. Distance vector routing is subject to instability if ...
MEF Global Interconnect Briefing
... All RAN traffic can be supported on single Carrier Ethernet connection – The MBH Generic Interworking Function (GIWF) enables the backhaul of any combination of 2G, 2.5G, 3G, Evolved-3G and 4G voice and data traffic over a single Carrier Ethernet RAN. – The MBH GIWF allows a combination of Ethernet, ...
... All RAN traffic can be supported on single Carrier Ethernet connection – The MBH Generic Interworking Function (GIWF) enables the backhaul of any combination of 2G, 2.5G, 3G, Evolved-3G and 4G voice and data traffic over a single Carrier Ethernet RAN. – The MBH GIWF allows a combination of Ethernet, ...
Document
... TCP/IP Protocol Suite Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. ...
... TCP/IP Protocol Suite Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. ...