cisco.camre.ac.uk
... Preventing a security incursion, like the attacks themselves, is a constantly evolving process. The security measures described in the next series of lesson are a sample of those in use and are an introduction to what you may be expected to use in the ICT industry. ...
... Preventing a security incursion, like the attacks themselves, is a constantly evolving process. The security measures described in the next series of lesson are a sample of those in use and are an introduction to what you may be expected to use in the ICT industry. ...
Test Bank for Crypto..
... authentication and _________ authentication. 11. In the context of network security, ___________ is the ability to limit and control the access to host systems and applications via communications links. 12. __________ prevents either sender or receiver from denying a transmitted message. Thus, when ...
... authentication and _________ authentication. 11. In the context of network security, ___________ is the ability to limit and control the access to host systems and applications via communications links. 12. __________ prevents either sender or receiver from denying a transmitted message. Thus, when ...
Chapter 1: Introduction to security
... • Encryption: To protect data and passwords • Authentication by digital signatures and certificates: To verify who is sending data over the network • Authorization: To prevent improper access • Integrity checking and message authentication codes: To protect against improper alteration of messages • ...
... • Encryption: To protect data and passwords • Authentication by digital signatures and certificates: To verify who is sending data over the network • Authorization: To prevent improper access • Integrity checking and message authentication codes: To protect against improper alteration of messages • ...
Slide 1
... and also protect the network against malicious use. Current approaches include per-user authentication, authorization of authenticated users through access keys, and access control, a number of schemes achieve security and provide authentication at MAC are being deployed in W-Lans WEP is simple ...
... and also protect the network against malicious use. Current approaches include per-user authentication, authorization of authenticated users through access keys, and access control, a number of schemes achieve security and provide authentication at MAC are being deployed in W-Lans WEP is simple ...
Cyber Security I
... A process occurs when a task is executed. Keeping processes separate prevents the failure of one process from negatively impacting another. ...
... A process occurs when a task is executed. Keeping processes separate prevents the failure of one process from negatively impacting another. ...
User Behavior based Anomaly Detection for Cyber
... Administrator and Security Personnel who are responsible for network security, as the networks are under threat byintruders. Generaing new information from existing data becomes more critical while integrating data from multiple sources. The intrusion may get access to value information and they mig ...
... Administrator and Security Personnel who are responsible for network security, as the networks are under threat byintruders. Generaing new information from existing data becomes more critical while integrating data from multiple sources. The intrusion may get access to value information and they mig ...
Attacks and Mitigations
... software. This may be achieved by luring users with a drive-by download, exploiting web browser vulnerabilities, or tricking the user into running a Trojan horse program, possibly in an email attachment. It will typically install modules which allow the computer to be commanded and controlled by the ...
... software. This may be achieved by luring users with a drive-by download, exploiting web browser vulnerabilities, or tricking the user into running a Trojan horse program, possibly in an email attachment. It will typically install modules which allow the computer to be commanded and controlled by the ...
Identity-Based Security
... particularly useful when single-purpose devices such as voice over IP handsets are used. If the Aruba mobility controller detects a voice handset attempting to conduct database queries or file server browsing, it is likely that the device credentials have been compromised by an intruder. The mobilit ...
... particularly useful when single-purpose devices such as voice over IP handsets are used. If the Aruba mobility controller detects a voice handset attempting to conduct database queries or file server browsing, it is likely that the device credentials have been compromised by an intruder. The mobilit ...
Course name Code/No Units Credit Units Prerequisite Lecture Lab
... Describe how digital forensics fits with the other forensic disciplines. Describe the possible availability levels for a web service. Describe how redundancy and geographic dispersion relate to availability. Define integrity as a security service. Describe how one-way cryptographic functions are use ...
... Describe how digital forensics fits with the other forensic disciplines. Describe the possible availability levels for a web service. Describe how redundancy and geographic dispersion relate to availability. Define integrity as a security service. Describe how one-way cryptographic functions are use ...
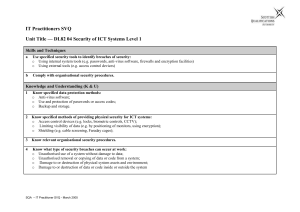
it user svq – level 2
... Know what type of security breaches can occur at work: o Unauthorised use of a system without damage to data; o Unauthorised removal or copying of data or code from a system; o Damage to or destruction of physical system assets and environment; o Damage to or destruction of data or code inside or ou ...
... Know what type of security breaches can occur at work: o Unauthorised use of a system without damage to data; o Unauthorised removal or copying of data or code from a system; o Damage to or destruction of physical system assets and environment; o Damage to or destruction of data or code inside or ou ...
OWN YOUR SPACE
... compromised by a piece of code that allows it to be controlled remotely without the computer owner’s knowledge. ...
... compromised by a piece of code that allows it to be controlled remotely without the computer owner’s knowledge. ...
Operating Systems 4
... Thus, when the OS starts at the end of the boot process, all instructions are executable. However, each time the OS allows a process to start a time slice, it switches the CPU to non-privileged mode by executing a “change privilege mode” instructinos. ...
... Thus, when the OS starts at the end of the boot process, all instructions are executable. However, each time the OS allows a process to start a time slice, it switches the CPU to non-privileged mode by executing a “change privilege mode” instructinos. ...
Attivo Networks Deception Platform Integrates with the Check Point
... companies of every size across many different industries. In addition to the security weaknesses, many security devices do not communicate with each other – meaning alerts raised by one device may not be passed to others in time to stop the same threat at a different point in the network. ...
... companies of every size across many different industries. In addition to the security weaknesses, many security devices do not communicate with each other – meaning alerts raised by one device may not be passed to others in time to stop the same threat at a different point in the network. ...
L16_Security
... a telephone conversion, an electronic mail message, and a transferred file are subject to these threats encryption masks the contents of what is transferred so even if obtained by someone, they would be unable to extract information ...
... a telephone conversion, an electronic mail message, and a transferred file are subject to these threats encryption masks the contents of what is transferred so even if obtained by someone, they would be unable to extract information ...
Responding to Intrusions
... limited to eavesdropping, identity spoofing, sniffer attacks, password-based attacks, and brute force attacks. In detail, eavesdropping is the collecting of data that passes between two active nodes on a network. Identity spoofing, aka IP address spoofing, occurs when an attacker assumes the source ...
... limited to eavesdropping, identity spoofing, sniffer attacks, password-based attacks, and brute force attacks. In detail, eavesdropping is the collecting of data that passes between two active nodes on a network. Identity spoofing, aka IP address spoofing, occurs when an attacker assumes the source ...
Systems Security
... The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploit these vulnera ...
... The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploit these vulnera ...
Security - NYU Stern School of Business
... – Mutates with every infection, making detection by the “signature” of the virus impossible – Mutation engine creates a random encryption key to encrypt the remainder of the virus • The key is stored with the virus ...
... – Mutates with every infection, making detection by the “signature” of the virus impossible – Mutation engine creates a random encryption key to encrypt the remainder of the virus • The key is stored with the virus ...
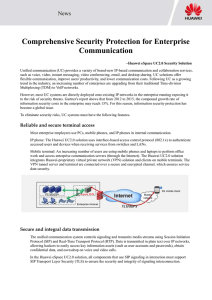
Comprehensive Security Protection for
... Some senior executives hope to keep their contact information secure to prevent undesirable calls, IMs, and emails. The Huawei UC2.0 solution classifies user information into personal and public information based on data sensitivity levels. Users (especially senior executives) can set refined and le ...
... Some senior executives hope to keep their contact information secure to prevent undesirable calls, IMs, and emails. The Huawei UC2.0 solution classifies user information into personal and public information based on data sensitivity levels. Users (especially senior executives) can set refined and le ...
C.2. Vulnerabilities
... “In 2001, a reporter for The Wall Street Journal bought a used computer in Afghanistan. He found the hard drive contained what appeared to be files from a senior al Qaeda operative. Cullison reports that he turned the computer over to the FBI. In his story published in 2004 in The Atlantic, he caref ...
... “In 2001, a reporter for The Wall Street Journal bought a used computer in Afghanistan. He found the hard drive contained what appeared to be files from a senior al Qaeda operative. Cullison reports that he turned the computer over to the FBI. In his story published in 2004 in The Atlantic, he caref ...
Neal Ziring Very Short Bio
... Mr. Neal Ziring is the Technical Director for the National Security Agency’s Capabilities Directorate, serving as a technical advisor to the Capabilities Director, Deputy Director, and other senior leadership. Mr. Ziring is responsible for setting the technical direction across many parts of the cap ...
... Mr. Neal Ziring is the Technical Director for the National Security Agency’s Capabilities Directorate, serving as a technical advisor to the Capabilities Director, Deputy Director, and other senior leadership. Mr. Ziring is responsible for setting the technical direction across many parts of the cap ...
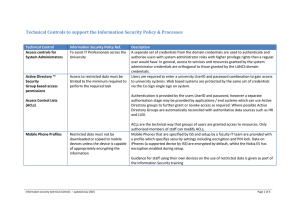
Technical Controls to support the Information
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
Research Scientist – Prague, Czech Republic Cisco Systems
... Cisco Systems, Security Cloud Operations (SCO) develops innovative products in the domain of Network Behavior Analysis (NBA) in order to fight against modern sophisticated attacks in today's cyberspace which include Advanced Persistent Threats (APT), exploit kits, zero-day attacks, polymorphic malwa ...
... Cisco Systems, Security Cloud Operations (SCO) develops innovative products in the domain of Network Behavior Analysis (NBA) in order to fight against modern sophisticated attacks in today's cyberspace which include Advanced Persistent Threats (APT), exploit kits, zero-day attacks, polymorphic malwa ...
Policy Template
... guidelines to the network. IS reserves the right to remove any network device that does not comply with standards or is not considered to be adequately secure. ...
... guidelines to the network. IS reserves the right to remove any network device that does not comply with standards or is not considered to be adequately secure. ...
Social Studies
... Understand ramifications of posting information, pictures, and videos online. Explain consequences of illegal and unethical use of technology systems and digital content. Identify examples of a computer crime. Know the penalties, fines, incarceration, and laws related to computer crimes. ...
... Understand ramifications of posting information, pictures, and videos online. Explain consequences of illegal and unethical use of technology systems and digital content. Identify examples of a computer crime. Know the penalties, fines, incarceration, and laws related to computer crimes. ...
Computer Security Presentation
... September [2004], a 600% increase over the 250 spotted a year ago. Of those, 45% were Trojan horses attempting to steal personal data, the company said. The company also reported a “surge in zombie networks,” saying it had found 400 programs in the past month compared with 17 a year ago. ...
... September [2004], a 600% increase over the 250 spotted a year ago. Of those, 45% were Trojan horses attempting to steal personal data, the company said. The company also reported a “surge in zombie networks,” saying it had found 400 programs in the past month compared with 17 a year ago. ...