Slide - Courses
... md5sum – Free file integrity verifier. Get a hash from a “known good” file. EventCombMT – Free event ID parser. Part of the …..there are TONS more free tools! ...
... md5sum – Free file integrity verifier. Get a hash from a “known good” file. EventCombMT – Free event ID parser. Part of the …..there are TONS more free tools! ...
Intrusion Detection and Prevention
... attacks originating from the Internet that are able to get through the outer firewall to public servers. Place in the private network to detect any attacks that are able to successfully penetrate perimeter security. ...
... attacks originating from the Internet that are able to get through the outer firewall to public servers. Place in the private network to detect any attacks that are able to successfully penetrate perimeter security. ...
E-Commerce and Bank Security
... Computer Science Classification: Confidentiality – protecting against unauthorized data disclosure Integrity – preventing unauthorized modification Availability – preventing data delays or denials ...
... Computer Science Classification: Confidentiality – protecting against unauthorized data disclosure Integrity – preventing unauthorized modification Availability – preventing data delays or denials ...
Slide 1
... achieve security. They are the IP Authentication Header (AH) and the IP Encapsulating Security Payload (ESP) header. The IP Authentication Header (AH) is used to provide connectionless integrity and data origin authentication for IP datagrams and protection against replays. The IP Encapsulating Secu ...
... achieve security. They are the IP Authentication Header (AH) and the IP Encapsulating Security Payload (ESP) header. The IP Authentication Header (AH) is used to provide connectionless integrity and data origin authentication for IP datagrams and protection against replays. The IP Encapsulating Secu ...
Cyber-Terrorism
... beheadings and IED attacks terrorist groups are engaging in a form of psychological warfare against their target audience. • The internet and other global media serves as ‘force multiplier’ for terrorist actions. ...
... beheadings and IED attacks terrorist groups are engaging in a form of psychological warfare against their target audience. • The internet and other global media serves as ‘force multiplier’ for terrorist actions. ...
Information Assurance Presentation
... all the time; a hacker only has to find one small hole. A sysadmin has to be lucky all of the time; a hacker only has to get lucky once. It is easier to destroy than to create.” – Robert Graham, lead architect of Internet Security Systems ...
... all the time; a hacker only has to find one small hole. A sysadmin has to be lucky all of the time; a hacker only has to get lucky once. It is easier to destroy than to create.” – Robert Graham, lead architect of Internet Security Systems ...
View File
... • use an application specific gateway / proxy • has full access to protocol – user requests service from proxy – proxy validates request as legal – then actions request and returns result to user ...
... • use an application specific gateway / proxy • has full access to protocol – user requests service from proxy – proxy validates request as legal – then actions request and returns result to user ...
System Administration
... Access Controls - specific access controls can include restrictions on: • Locations from which a user can log on to the system or access its resources. • Days/times when access is granted or denied. • The ability to read, write, create and delete directories and files. • The ability to execute progr ...
... Access Controls - specific access controls can include restrictions on: • Locations from which a user can log on to the system or access its resources. • Days/times when access is granted or denied. • The ability to read, write, create and delete directories and files. • The ability to execute progr ...
procedure name - Siskiyou Central Credit Union
... o They may not be used to send communications or material that defames or disparages an individual, Credit Union, or business. o They may not be used to conduct personal business. Solicitations, offers to buy and sell goods or services, and other personal messages to groups are not an appropriate us ...
... o They may not be used to send communications or material that defames or disparages an individual, Credit Union, or business. o They may not be used to conduct personal business. Solicitations, offers to buy and sell goods or services, and other personal messages to groups are not an appropriate us ...
shuffling:improving data security in ad hoc networks based
... reveal relationships between nodes or disclose their IP addresses. If a route to a particular node is requested more often than to other nodes, the attacker will be able to expect that the node is important for the network, and disabling it could bring the entire network down. Unlike passive attacks ...
... reveal relationships between nodes or disclose their IP addresses. If a route to a particular node is requested more often than to other nodes, the attacker will be able to expect that the node is important for the network, and disabling it could bring the entire network down. Unlike passive attacks ...
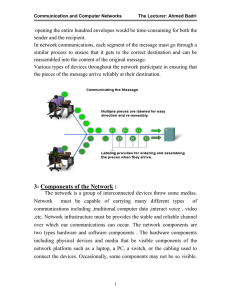
1-Introduction :
... invisible radio frequency or infrared waves. The software components include Services and processes that are the communication programs that run on the networked devices. A network service provides information in response to a request. Services include many of the common network applications people ...
... invisible radio frequency or infrared waves. The software components include Services and processes that are the communication programs that run on the networked devices. A network service provides information in response to a request. Services include many of the common network applications people ...
Slides.
... System design should be public Default should be no access Check for current authority Give each process least privilege possible Protection mechanism should be ...
... System design should be public Default should be no access Check for current authority Give each process least privilege possible Protection mechanism should be ...
Chapter11
... What are some other safeguards against software theft? Product activation allows user to input product identification number online or by phone and receive unique installation identification number ...
... What are some other safeguards against software theft? Product activation allows user to input product identification number online or by phone and receive unique installation identification number ...
group policy - University Of Worcester
... watching for communication patterns… reveals user ID, data volumes & sending times can detect covert channels ...
... watching for communication patterns… reveals user ID, data volumes & sending times can detect covert channels ...
Presentation Prepared By: Raghda Zahran
... plan to implement in the event of catastrophic data loss? ...
... plan to implement in the event of catastrophic data loss? ...
A Primer on Computer Security
... Corrupted files on victim’s machine – deleted mp3, jpg and other files Searched for active passwords in memory and emailed them to Web site in the ...
... Corrupted files on victim’s machine – deleted mp3, jpg and other files Searched for active passwords in memory and emailed them to Web site in the ...
Chapter 9
... Securing Traffic with IPSec IPSec allows us to protect our network from within IPSec secures the IP protocol IPSec has two principle goals: To protect the contents of IP packets To provide defense against network attacks through packet filtering and the enforcement of trusted communicatio ...
... Securing Traffic with IPSec IPSec allows us to protect our network from within IPSec secures the IP protocol IPSec has two principle goals: To protect the contents of IP packets To provide defense against network attacks through packet filtering and the enforcement of trusted communicatio ...
Information Security
... Special characters ($, %, @, etc.) Password Generators, password cracking ...
... Special characters ($, %, @, etc.) Password Generators, password cracking ...
BILL ANALYSIS
... The security of State computer networks is currently handled by each agency on an independent basis. As computer needs arise, agencies with resources to fill these needs often find solutions, while agencies with limited resources are often forced to choose between accessibility and security. This fr ...
... The security of State computer networks is currently handled by each agency on an independent basis. As computer needs arise, agencies with resources to fill these needs often find solutions, while agencies with limited resources are often forced to choose between accessibility and security. This fr ...
Operating System Security
... • high-integrity file cannot be contaminated by information from low-integrity processes. • high-integrity process cannot be subverted by low integrity processes or data. The integrity class label on a file guarantees that the contents came only from sources of at least that degree of integrity. ...
... • high-integrity file cannot be contaminated by information from low-integrity processes. • high-integrity process cannot be subverted by low integrity processes or data. The integrity class label on a file guarantees that the contents came only from sources of at least that degree of integrity. ...
BitLocker - Microsoft
... “After virus infections, businesses report unintended forwarding of e-mails and loss of mobile devices more frequently than they do any other security breach” Jupiter Research Report, 2004 ...
... “After virus infections, businesses report unintended forwarding of e-mails and loss of mobile devices more frequently than they do any other security breach” Jupiter Research Report, 2004 ...
security threats: a guide for small and medium
... we do not hear of small or medium-sized businesses becoming victims of such infections because it is not in their interest to publicize these incidents. Many small or medium-sized business networks cannot afford to employ prevention mechanisms such as network segregation. These factors simply make i ...
... we do not hear of small or medium-sized businesses becoming victims of such infections because it is not in their interest to publicize these incidents. Many small or medium-sized business networks cannot afford to employ prevention mechanisms such as network segregation. These factors simply make i ...