security threats: a guide for small and medium
... network when they run malicious executable code (EXE files). Sometimes they might receive an email with an attached worm or download spyware when visiting a malicious website. Alternatively, to get work done, employees may decide to install pirated software for which they do not have a license. This ...
... network when they run malicious executable code (EXE files). Sometimes they might receive an email with an attached worm or download spyware when visiting a malicious website. Alternatively, to get work done, employees may decide to install pirated software for which they do not have a license. This ...
General IT Auditing Techniques
... Typical results of a port scan include: Discovery of ports that are listening or open Determination of which ports refuse connections Determination of connections that time out Port scanning tips include: Start by scanning slowly, a few ports at a time To avoid detection, try the same port across se ...
... Typical results of a port scan include: Discovery of ports that are listening or open Determination of which ports refuse connections Determination of connections that time out Port scanning tips include: Start by scanning slowly, a few ports at a time To avoid detection, try the same port across se ...
D`Amo - softfarm
... • D’Amo enables strict separation of authority between the Security Manager and the Database Administrator. ...
... • D’Amo enables strict separation of authority between the Security Manager and the Database Administrator. ...
Click to add title - toostusuudised.ee
... Teiste skaneerimised • keskmiselt 223 päringut päevas, • 118 riigist • 9996 ip aadressilt, mis on suunatud 516 erinevale pordile ...
... Teiste skaneerimised • keskmiselt 223 päringut päevas, • 118 riigist • 9996 ip aadressilt, mis on suunatud 516 erinevale pordile ...
IT Security Policy
... DISTRICTS shall maintain a network configuration management program which includes as a minimum: a network diagram identifying all connections, addresses, and purpose of each connection including management approval of all high risk internetfacing ports such as mail (SMTP/25), file transport protoco ...
... DISTRICTS shall maintain a network configuration management program which includes as a minimum: a network diagram identifying all connections, addresses, and purpose of each connection including management approval of all high risk internetfacing ports such as mail (SMTP/25), file transport protoco ...
Safeguarding of Unclassified Controlled Technical Information (UCTI)
... Contractors that don’t have all of the NIST controls implemented must submit a written explanation of how 1) the required security control(s) is not applicable, or 2) an alternative control or protective measure is used to achieve equivalent protection. This means all 51 controls must be addressed, ...
... Contractors that don’t have all of the NIST controls implemented must submit a written explanation of how 1) the required security control(s) is not applicable, or 2) an alternative control or protective measure is used to achieve equivalent protection. This means all 51 controls must be addressed, ...
Out Of The Blue - Joshua`s Learning Log
... Typically, wireless access points can cover generally cover 100-300 feet indoors and up to 600-1000 feet in open space. However, when accessed points are placed at maximum range, they tend to suffer from poor connections and intermittent service. Finally, the number of users that can access a networ ...
... Typically, wireless access points can cover generally cover 100-300 feet indoors and up to 600-1000 feet in open space. However, when accessed points are placed at maximum range, they tend to suffer from poor connections and intermittent service. Finally, the number of users that can access a networ ...
Chapter 6
... • How firewalls can protect intranets and corporate servers • What role the Secure Socket Layer, Secure HTTP, and secure electronic transaction protocols play in protecting electronic commerce ...
... • How firewalls can protect intranets and corporate servers • What role the Secure Socket Layer, Secure HTTP, and secure electronic transaction protocols play in protecting electronic commerce ...
Computer Security: Principles and Practice, 1/e
... o Often sufficient for use as a component of a distributed IDS to warn of imminent attack ...
... o Often sufficient for use as a component of a distributed IDS to warn of imminent attack ...
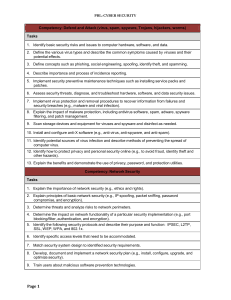
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... 3. Describe the types of cryptography algorithms (e.g., secret key, public key, and hash functions). 4. Describe trust models such as web of trust, Kerberos, and certificates. 5. Identify cryptography applications used for password protection and private communication. (IP security protocol, clipper ...
... 3. Describe the types of cryptography algorithms (e.g., secret key, public key, and hash functions). 4. Describe trust models such as web of trust, Kerberos, and certificates. 5. Identify cryptography applications used for password protection and private communication. (IP security protocol, clipper ...
Information Security
... -This packet is always good so pass it into my network. -This packet is always bad so drop it and tell me about it. -This packet is sometimes bad so tell me about it, but don't drop it. ...
... -This packet is always good so pass it into my network. -This packet is always bad so drop it and tell me about it. -This packet is sometimes bad so tell me about it, but don't drop it. ...
Networking Security
... • These databases contain a variety of data elements regarding the assignment of domain names, individual contacts, and even Internet Protocol (IP) addresses ...
... • These databases contain a variety of data elements regarding the assignment of domain names, individual contacts, and even Internet Protocol (IP) addresses ...
Privacy Legislation Update $1.7 Million Civil Penalty for a
... Detecting a Breach Due to the rapidly evolving nature of the information security threat spectrum, it is important that organisations also include breach detection capabilities within their environment. This should include: ...
... Detecting a Breach Due to the rapidly evolving nature of the information security threat spectrum, it is important that organisations also include breach detection capabilities within their environment. This should include: ...
Phishing and whaling – Don`t get hooked!
... perhaps the most technological expert panel presenter. Perhaps counter intuitively this self-confessed “technology geek” made the following two key observations: 1. Cyber threats are not about the technology – usually it is the human part of the process that is the weak link. Access to an organisati ...
... perhaps the most technological expert panel presenter. Perhaps counter intuitively this self-confessed “technology geek” made the following two key observations: 1. Cyber threats are not about the technology – usually it is the human part of the process that is the weak link. Access to an organisati ...
CATAPAN Global Brochure
... Strengthening and building cross government relationships is an essential part of our economic growth, expanding opportunities and creating a global communications network where intelligence and assets can be shared seamlessly. The sharing of this intelligence means that cross-government communicati ...
... Strengthening and building cross government relationships is an essential part of our economic growth, expanding opportunities and creating a global communications network where intelligence and assets can be shared seamlessly. The sharing of this intelligence means that cross-government communicati ...
Global Challenges
... Duqu computer virus Detected by Iran civil defense organization More than 100 Pakistani Government Sites Under Malware attack Thousands of United Nation (UNDP) logins leaked Cyber attacks hit Fujitsu local government system in Japan Largest DDOS attack hit Chinese company ...
... Duqu computer virus Detected by Iran civil defense organization More than 100 Pakistani Government Sites Under Malware attack Thousands of United Nation (UNDP) logins leaked Cyber attacks hit Fujitsu local government system in Japan Largest DDOS attack hit Chinese company ...
Naval Postgraduate School
... 5. Upper-Level Graduate Hours: All MACO students, regardless of sponsorship, must complete no fewer than 12 quarter hours of 4000-level coursework (do not relist courses identified in sections 2 through 4): ...
... 5. Upper-Level Graduate Hours: All MACO students, regardless of sponsorship, must complete no fewer than 12 quarter hours of 4000-level coursework (do not relist courses identified in sections 2 through 4): ...
Current Issues in Maintaining a Secure System
... Malware Prevention • Many companies are blocking employees from nonbusiness related web browsing with technology rather than policy. – General Electric bars instant messaging, file sharing programs, and access to personal email. – JP Morgan Chase blocks any traffic it can’t trace and analyze includ ...
... Malware Prevention • Many companies are blocking employees from nonbusiness related web browsing with technology rather than policy. – General Electric bars instant messaging, file sharing programs, and access to personal email. – JP Morgan Chase blocks any traffic it can’t trace and analyze includ ...
Support: Ticket, Process, and Expectations
... not connected and is thus protected from anyone else accessing the files. ...
... not connected and is thus protected from anyone else accessing the files. ...
Key To Personal Information Security
... • Sniffer programs exploit this characteristic, monitoring all traffic and capturing the first 128 bytes or so of every unencrypted FTP or Telnet session (the part that contains user passwords) • It is estimated that in the last year more than 100,000 systems were victims of packet sniffers ...
... • Sniffer programs exploit this characteristic, monitoring all traffic and capturing the first 128 bytes or so of every unencrypted FTP or Telnet session (the part that contains user passwords) • It is estimated that in the last year more than 100,000 systems were victims of packet sniffers ...
Building an in-depth defense with Vectra and sandbox security
... command-and-control (C&C) servers that the attacker uses to remotely control each phase of the cyber attack. The attacker uses the C&C servers to send commands to and receive responses from hosts under his control as a result of downloading the exploit. Cyber attacks that are targeted differ from bo ...
... command-and-control (C&C) servers that the attacker uses to remotely control each phase of the cyber attack. The attacker uses the C&C servers to send commands to and receive responses from hosts under his control as a result of downloading the exploit. Cyber attacks that are targeted differ from bo ...
Newfield National Bank > Home
... In the third type of tax scam, malicious actors use tax related spam, phishing emails, and fraudulent websites to trick victims into providing login names, passwords, or additional information, which can be used in further fraud. Other emails or websites may download malware onto the victim’s comput ...
... In the third type of tax scam, malicious actors use tax related spam, phishing emails, and fraudulent websites to trick victims into providing login names, passwords, or additional information, which can be used in further fraud. Other emails or websites may download malware onto the victim’s comput ...
Important Concepts.
... Packet sniffing in computer networks is like wire tapping in telephone network. ...
... Packet sniffing in computer networks is like wire tapping in telephone network. ...
CNCERT/CC Annual Report 2008
... 1.4. Constituency & Etc CNCERT/CC provides computer network security services and technology support in the handling of security incidents for national public networks, important national application systems and key organizations, involving detection, prediction, response and prevention. It collects ...
... 1.4. Constituency & Etc CNCERT/CC provides computer network security services and technology support in the handling of security incidents for national public networks, important national application systems and key organizations, involving detection, prediction, response and prevention. It collects ...