IBM Security QRadar Incident Forensics
... terms and conditions of the agreements under which they are provided. The client is responsible for ensuring compliance with laws and regulations applicable to it. IBM does not provide legal advice or represent or warrant that its services or products will ensure that the client is in compliance w ...
... terms and conditions of the agreements under which they are provided. The client is responsible for ensuring compliance with laws and regulations applicable to it. IBM does not provide legal advice or represent or warrant that its services or products will ensure that the client is in compliance w ...
Example: Data Mining for the NBA - The University of Texas at Dallas
... Denial of service Denial of service attacks cause the service or program to cease functioning or prevent others from making use of the service or program. These may be performed at the network layer by sending carefully crafted ...
... Denial of service Denial of service attacks cause the service or program to cease functioning or prevent others from making use of the service or program. These may be performed at the network layer by sending carefully crafted ...
Introduction to Information Security Chapter N
... Deliberate Acts of Theft Illegal taking of another’s physical, electronic, or intellectual property Physical theft is controlled relatively easily Electronic theft is more complex problem; evidence of crime not readily apparent ...
... Deliberate Acts of Theft Illegal taking of another’s physical, electronic, or intellectual property Physical theft is controlled relatively easily Electronic theft is more complex problem; evidence of crime not readily apparent ...
Introduction to Information Security Chapter N
... Deliberate Acts of Theft Illegal taking of another’s physical, electronic, or intellectual property Physical theft is controlled relatively easily Electronic theft is more complex problem; evidence of crime not readily apparent ...
... Deliberate Acts of Theft Illegal taking of another’s physical, electronic, or intellectual property Physical theft is controlled relatively easily Electronic theft is more complex problem; evidence of crime not readily apparent ...
Chapter 1
... The attacker attempts to breach a web application. Common attacks of this type are SQL injection and Cross Site Scripting. ...
... The attacker attempts to breach a web application. Common attacks of this type are SQL injection and Cross Site Scripting. ...
Springfield Data Center Program Alignment
... Firewalls – Boundary protection and access controls for network resources Intrusion detection system 0 detects and alerts on possible network attack DNS – hierarchical naming system for computers and services VPN Concentrator – allows secure remote access Security Incident * Event Mgmt System – corr ...
... Firewalls – Boundary protection and access controls for network resources Intrusion detection system 0 detects and alerts on possible network attack DNS – hierarchical naming system for computers and services VPN Concentrator – allows secure remote access Security Incident * Event Mgmt System – corr ...
Rapid Response to the Advanced Persistent Threat (APT)
... Nation states and criminal gangs with substantial resources utilise an advanced attack methodology known as Advanced Persistent Threat (APT). This methodology allows them to gain a foothold in, and steal data from, your network without restriction or detection. APT is adaptive, and provides attacker ...
... Nation states and criminal gangs with substantial resources utilise an advanced attack methodology known as Advanced Persistent Threat (APT). This methodology allows them to gain a foothold in, and steal data from, your network without restriction or detection. APT is adaptive, and provides attacker ...
Data Security Manager
... To assist in taking timely action resulting from any risk assessment recommendations. This may involve liaison with other department such as estates or planning etc. It is essential to keep the Chief Information Officer informed if there are any issues of non-compliance. ...
... To assist in taking timely action resulting from any risk assessment recommendations. This may involve liaison with other department such as estates or planning etc. It is essential to keep the Chief Information Officer informed if there are any issues of non-compliance. ...
Accessing Wireless Networks Safely Brochure
... sniffing your traffic and forces anyone attempting to access your wireless network to enter in a passcode. Without the right passcode, they can’t “piggyback” on your network. ■■ Change the default SSID and administra tive password. The SSID (Service Set Identifier) is essentially the “name” of your ...
... sniffing your traffic and forces anyone attempting to access your wireless network to enter in a passcode. Without the right passcode, they can’t “piggyback” on your network. ■■ Change the default SSID and administra tive password. The SSID (Service Set Identifier) is essentially the “name” of your ...
Computer Security, Ethics, and Privacy
... Chapter 11 Objectives Describe the types of computer security risks ...
... Chapter 11 Objectives Describe the types of computer security risks ...
William Stallings, Cryptography and Network Security 5/e
... Estimated Money loss per year due to security breaches in your company = L Estimated Money loss per year due to uncontrolled system administrator/programmers paranoidism = D ...
... Estimated Money loss per year due to security breaches in your company = L Estimated Money loss per year due to uncontrolled system administrator/programmers paranoidism = D ...
Accepable Use and User Policies - Information Systems and Internet
... Outside attacker attached to trusted network ...
... Outside attacker attached to trusted network ...
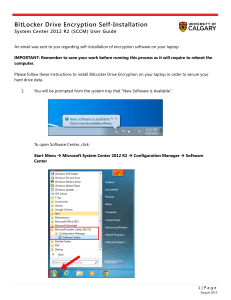
BitLocker Drive Encryption Self
... System Center 2012 R2 (SCCM) User Guide An email was sent to you regarding self-installation of encryption software on your laptop. IMPORTANT: Remember to save your work before running this process as it will require to reboot the computer. Please follow these instructions to install BitLocker Drive ...
... System Center 2012 R2 (SCCM) User Guide An email was sent to you regarding self-installation of encryption software on your laptop. IMPORTANT: Remember to save your work before running this process as it will require to reboot the computer. Please follow these instructions to install BitLocker Drive ...
Computer Security and Penetration Testing Chapter 16 Windows
... to access resources on another domain, without being authenticated by it ...
... to access resources on another domain, without being authenticated by it ...
Ch06-Firewalls
... 1. The client connects to the server via a TCP session. 2. The client and server exchange information on administrative details, such as supported encryption methods and their protocol version, each choosing a set of protocols that the other supports. 3. The client and server initiate a secret-key e ...
... 1. The client connects to the server via a TCP session. 2. The client and server exchange information on administrative details, such as supported encryption methods and their protocol version, each choosing a set of protocols that the other supports. 3. The client and server initiate a secret-key e ...
Slide 1
... An inline NIPS works like a Layer 2 bridge. It sits between the systems that need to be protected and the rest of the network. NIPS proactively protect machines against damage from attacks that signature-based technologies cannot detect, as most NIPS solutions have the ability to look at application ...
... An inline NIPS works like a Layer 2 bridge. It sits between the systems that need to be protected and the rest of the network. NIPS proactively protect machines against damage from attacks that signature-based technologies cannot detect, as most NIPS solutions have the ability to look at application ...
Introduction - GMU Computer Science
... physical mail. Use one time, time limited verifiers instead. • Implement SMS or e-mail notification of account activities, particularly those involving transfers and change of address or phone details. • Prevent too many transactions from the same user being performed in a certain period of time – t ...
... physical mail. Use one time, time limited verifiers instead. • Implement SMS or e-mail notification of account activities, particularly those involving transfers and change of address or phone details. • Prevent too many transactions from the same user being performed in a certain period of time – t ...
10.2 BASIC E-COMMERCE SECURITY ISSUES AND LANDSCAPE
... - Making sure that a customer is safe and secure while shopping online is a crucial part of improving the online buyer’s experience. - Measures taken to protect information systems and their processes against all risks. In other words assure the systems’ availability when needed. The assurance inclu ...
... - Making sure that a customer is safe and secure while shopping online is a crucial part of improving the online buyer’s experience. - Measures taken to protect information systems and their processes against all risks. In other words assure the systems’ availability when needed. The assurance inclu ...
JO-Oxford_Preso - International Cyber Center
... Successfully managing our information resources against Advanced and Persistent Threats will require an organizational integration of network and security disciplines Export Approval Number: IS-ES-072109-175 ...
... Successfully managing our information resources against Advanced and Persistent Threats will require an organizational integration of network and security disciplines Export Approval Number: IS-ES-072109-175 ...
Slide 1
... the ability to perform backups, including the security privileges that went along with it. ...
... the ability to perform backups, including the security privileges that went along with it. ...
Confidentiality
... The five main phases of an information security plan are as follows; 2.1 Inspection - The most important tasks in developing an Information Security Plan are identifying the key corporate functions, the capabilities they need, when they need those capabilities, and how they interact with other funct ...
... The five main phases of an information security plan are as follows; 2.1 Inspection - The most important tasks in developing an Information Security Plan are identifying the key corporate functions, the capabilities they need, when they need those capabilities, and how they interact with other funct ...