* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download 2001-10-11-AIC-SecurityForEducation
Information security wikipedia , lookup
Mobile security wikipedia , lookup
Wireless security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Deep packet inspection wikipedia , lookup
Unix security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Computer security wikipedia , lookup
Distributed firewall wikipedia , lookup
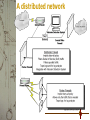
Analysts International Security Services Introductions – Mark Lachniet • Former Director of Information Systems at Holt Public Schools • Former MAEDS board member and conference organizer (go to www.maeds.org) • Full time security specialist for Sequoia Services and part of the security services team • Novell CNE / Master CNE – Connectivity Track • Microsoft MCSE 4.0 • Linux Professional Institute LPIC-1 • Checkpoint Certified Security Engineer Tentative Agenda • • • • • • • • • • Introductions Quick survey Security needs in K12 Child Internet Protection Act / USF Integrity, publicity, and hassle Policies and procedures Types of security services to know about Types of security technology to know about Secure network configurations Q&A Quick Survey • What is your level of technical interest/affinity (low, med, high) • Do you currently have a firewall? • Do you currently have content filtering? • Do you currently have an IDS? • Have you done a vulnerability assessment on your network? Security in K-12 education Organizational reasons for security in K-12 education: • Funding requirements (USF) • Integrity of critical data • Public opinion / negative publicity • Time & money to fix the damage • Student safety & disciplinary issues • Avoid costly litigation! Funding Issues – the Child Internet Protection Act • The Children’s Internet Protection Act (CIPA) and the Neighborhood Internet Protection Act (NCIPA) went into effect on April 20, 2001. • Have a 1-year window of time to comply, but must “certify” that you are taking action to comply by 10/28/2001 in order to get USF year 4 discounts. Must comply for year 5 funding. • “I certify that, as of the date of the start of discounted services, ... pursuant to the Children's Internet Protection Act, as codified at 47 U.S.C. § 254(h) and (l), the recipient(s) of service represented in the Funding Request Number(s) on this Form 486 is (are) undertaking such actions, including any necessary procurement procedures, to comply with the requirements of CIPA for the next funding year, but has (have) not completed all requirements of CIPA for this funding year. “ From: http://www.sl.universalservice.org/whatsnew/MISC/CIPA051801.asp Funding Issues – the Child Internet Protection Act cont. Some mandatory actions to take: 1. “Technology Protection Measure” such as a content filter 2. “Internet Safety Policy” to address issues like student access to inappropriate material, hacking, access to confidential student information, etc. 3. “Public Notice and Hearing” to discuss these issues with the community and provide a chance for input Integrity of data • Integrity of system data – Grades / Attendance: changing (for better or worse) student grades or attendance: School Accreditation, state funding (count day) etc. – Information considered private: SS#, special education status, free lunch programs, notes from councilors, discipline, medication (ritalin), etc. – Integrity of financial data – online PO’s, budgetary information (balances, accounts, responsibility reports) – Payroll and Human Resources – criminal history, disciplinary actions, disability, etc. Online predators and threats • Failure to protect children who are threatened by electronic means • Pedophiles, stalkers, and bad people • Student to student threats, assault • Recorded information about drugs, sexual activity, abuse, gang activity, violence, or other crime • The problem of IM and chat rooms • Student info – last names & pictures • South Carolina’s law The public • As a public school employee, anyone can question your methods and actions at a school board meeting, etc. • Bad security can (and eventually probably will) equal bad publicity. • May expose the district to significant lawsuits, especially in areas of protecting children’s information such as special ed. status • Be aware of FOIA laws – what can they legally obtain??? All e-mail? What is protected? • And… of course… Internet filtering. • The path of least resistance: seek input, obtain support from administration and unions, and keep a low profile The Hassle Factor – naughty kids • Broken systems – deleted files, missing software, physical vandalism • Prevents students from learning • Requires extensive time and $$ to fix • Use desktop imaging products such as ZenWorks • Use workstation protection products such as Centurion Guard • Frequently leads to disciplinary action. The computer tech as computer-narc (Think S.C.) • Take good notes of what you do • Learn to use windows find! Alt-PrtScn it, print it out, and start a file • Parents….. Policies and procedures • Should apply to students and teachers • Need to have a policy to have “teeth” • Use an acceptable use policy (AUP) and get sign-off from everyone • Use a “implicit deny” policy instead of an “implicit allow” because You can’t revise it every time a new technology comes out • DO discuss password strength and protection issues – frequency of change, sharing, complexity, etc. This may not be intuitive to non-technical users Types of security services • Security is a nascent field in many respects • Terminology, procedures and skill levels vary drastically • Some disagreement over what best practices actually are • Few objective benchmarks to allow “apples to apples” comparisons • Shop wisely.. Use someone you can trust and who will be around a few years from now • The issue of hiring ex-hackers.. Former students? • Your Mileage May Vary Security services at Sequoia Services / Analysts International • Vulnerability assessments – ISAS for the Internet border – OSAS for the internal network • Comprehensive analysis – SNAS – Security needs and policy analysis – SAS – Detailed, highly customized projects • Managed services – Active Internet Managed firewall – VPN, content filtering, virus protection, etc. • Enterprise networking – Secure design and implementation of network infrastructure Money, Money, Money • Schools are on a tight budget, and there don’t seem to be any grants you can apply for to get security work done • However, CO$T is the *best* reason to get security work done • Talk to the school board, H.R. and Finance directors, and superintendents about the risk (and ask for help!) • Security is a proactive cost savings, not reactive Scare them…. with reality • The frequency of computer breaches in the media and at peer organizations • The national cost of computer incidents – Code Red alone = $1.2 BILLION • Compute the cost in lost productivity if the HR, payroll, or student system dies (tons!) • Discuss the cost of a lawsuit (as Holt knows, this is not in any way cheap) • Discuss the need for student safety – could a child be exposed to harm due to a failure in the existing system? Scare them with more reality… • Discuss the educational ramifications – what if all student directories were wiped out and no backups existed? • Discuss privacy issues – all of the superintendent’s or spec. ed director’s email being sent to the local paper for example • Loss of USF funding, loss of accreditation • Loss of stakeholder confidence and support • Loss of valuable computer technician time that could otherwise be spent keeping everything working properly Technologies to know about • There are Several important tools in evaluating network and system security • Server hardening – The number one issue! Patches, hotfixes, and checklists • Traffic control – Firewalls, routers, access control lists, etc. Consider traffic control on network devices as well as filters on servers (ie, windows filtering, Zone Alarm, etc) Secure network designs • The commonly accepted Internet border configuration utilizes three or more segments: • Outside or “dirty” network – IP addresses that can be reached from the Internet. This network should be considered completely untrustworthy, and the hosts must be hardened. In an ideal situation, *no* hosts will be on this network at all. • DMZ (De-Militarized Zone) – RFC1918 reserved IP addresses that are protected by a firewall and mapped to outside IP addresses. This network is also to be considered untrustworthy, and should not be able to initiate conversations with the inside network • Inside network – RFC1918 reserved IP addresses for internal use (servers, workstations, etc.) Considered a “safe”network. Usually utilizes many-to-one network address translation. Use NAT and access control • Best practices dictate that you use RFC1918 addresses such as: 10.0.0.0/8 172.18.0.0/16 192.168.0.0/24 • Use one-to-one NAT for externally accessible hosts or special clients (or where you have room) • Use many-to-one (PAT, IP Masquerading, overloaded nat) for client access to the Internet • NAT can break a lot of software, so be aware of address translation issues –anything that requires a host-to-host communication channel • Use ACLs (access control lists) to deny all traffic except for that which is needed Firewall configurations: Block all incoming Firewall Configurations: Selectively block outgoing Important stuff to filter • Everything! (except what you need) • RFC1918 traffic on the outside interface • Spoofed traffic (such as source IP = 127.0.0.1 or 255.255.255.255) • Known DoS (Denial of Service) attacks, especially anything with a broadcast address (ping 255.255.255.255) • Windows SMB traffic, udp/tcp 135-139 • LDAP servers, SQL servers, etc. A distributed network Considerations with a distributed net • Can share a single fast internet connection, giving you good high-speed “burst” beyond what you could afford individually • In this type of design, partners still have control of their traffic and ACL’s • Can be used as a single point of control in the event of attacks or incidents • Consolidation of partners allows for economical intrusion detection and log analysis • Best with fiber-optic connections to partners • Down side: Can also be a single point of failure Questions and Answers Contacting us for help Mark Lachniet (517) 336-1004 [email protected] Jack Brahce (517) 336-1025 [email protected]