* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download CIS484-FIREWALL
Mobile security wikipedia , lookup
Wireless security wikipedia , lookup
Norton Internet Security wikipedia , lookup
Computer security wikipedia , lookup
Cybercrime countermeasures wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Deep packet inspection wikipedia , lookup
Computer and network surveillance wikipedia , lookup
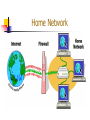
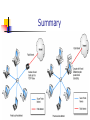
Firewall Kidane Ghebresilassie Sandra Corona Sirisha Garimella Christopher Mora Elizabeth Canela Contents • Introduction • Software firewall • Hardware firewall • • Home/Corporate Network Future trends Software Firewall A firewall ISOLATES the computer from the Internet. A “wall of code” inspects each individual “packet” of data as it arrives at either side of the firewall — inbound or outbound. Determines whether the data packet should be allowed to pass or be blocked. How does a firewall work? Exchange of individual "packets" of data. Each packet is transmitted by its source machine toward its destination machine. Each machine sends back "acknowledgement packets" to let the source machine know that data was received. The software firewall has total veto power over the computer's receipt of any data from the internet. Illustration Personal firewalls Top Picks : Zone Alarm, Norton Internet Security More Choices : Black Ice, PcInternet patrol, Kerio, Norman, Outpost, Sygate, Terminet Fading Away : ConSeal, eSafe, HackTracer, PC Viper, NeoWatch & Sphinx Free firewall and security software Zonealarm - PC firewall that keeps personal data and privacy safe from internet hackers and data thieves. Protection against worms, Trojans, spyware and 47 types of malicious email attachments. Kerio Personal Firewall - Controls all dataflow in both directions - from the internet to the computer and vice versa and it can block all attempted communication, allowing only what is permitted. Hardware Firewall Devices Used As Firewalls Firewall Router Hub PC Host Collection of Hosts Dial-Up System Internet Workstation/s 101011 Firewall (DMZ) (HUB) LAN HUB Performs basic packet filtering at the router level without purchasing additional hardware or software. Firewall with Proxy Server Proxy / Internet LAN 10101 Firewall HUB Proxy is the shield of the network Workstation/s Buying a Firewall • • • Product prices range from a few hundred dollars to thousands of dollars. Features range from a couple dozen configuration parameters to detailed level of control. Variety of alarms, controls and alert sounds. Buying a Firewall Umax Technologies Model : Ugate-3000 Price : $399.95 Capabilities : Provides a secure, high- speed LAN- connected gateway to the internet for 253 users over cable or an Asymmetric Digital Subscriber Line (ASDL) modem. Contd. 3Com Model : Office Connect Internet Price : $695.00 Capabilities : • • • Protects the LAN from unauthorized access . Prevents denial of service attacks from the internet. Includes two 10Mbps Ethernet ports. Contd. RADGUARD Model : cIPro Price : $4,950.00 Capabilities : • • • • Offers IP security and internet key exchange network encryption. Integrated firewall functions. Network address translation. Encrypted SNMP management traffic. Contd. Consider that not all packet filtering routers filter the source TCP/UDP port, however more vendors are starting to incorporate this capability. Some routers examine the network’s interface as a packet arrives, then uses additional criterion. Some UNIX hosts provide packet filtering capability, although most don’t. Basic Firewall Configuration Option 1: Internet <--> Firewall Hardware or Software <--> Internal Network/Individual Computer Option 2: Internet <--> Hardware Firewall/Router <--> Personal Firewall Software <--> PC Home Network Sorting Data Workstation/s Internet Firewall LAN Router Or (DMZ) Cable Modem (HUB) HUB Outside Server Packet filtering - a simple method, packet filtering entails analyzing small packets or chunks of data through a series of filters. Contd. Proxy service - some information is transmitted by proxy, automatically responding to the source with some small amount of data. Stateful inspection - this method looks at parts of packets to see if they match specific characteristics that are allowable. Most modern firewalls offer stateful inspection. Firewall Analysis Depends on both ports and application names. Users can define rules according to actual ports or they can set rules to match a program. The firewall will detect common programs such as web browsers and email programs and auto configure the necessary ports as they attempt to connect to the internet. Contd. The firewall can be set to learn new programs to begin with and later changed to only allow those that have been predefined. The firewall tends to default to “any port” for detected applications. Recommended that users learn the required port for each allowable Internet program and edit the remote ports to match. Features of firewall Port Control, Application Monitoring (Program Control) and Packet Filtering. Additional features: Data encryption, hiding presence, reporting/logging, e-mail virus protection, pop-up ad blocking, cookie digestion, spy ware protection, laptop protection. Corporate network Setting up your personal firewall Kerio Firewall Basics Software or hardware between your LAN and the Internet, inspecting both inbound and outbound traffic by rules that you set, which define the sort of security you want. Kerio Choices Permit Unknown Ask Me First Deny Unknown What Traffic Is Good/What's Bad? Experience Reading Learning Installation Note Concerns Do Firewalls Prevent Viruses and Trojans? NO!! A firewall can only prevent a virus or Trojan from accessing the internet while on your machine. 95% of all viruses and Trojans are received via e-mail, through file sharing (like Kazaa or Gnucleus) or through direct download of a malicious program. Firewalls can't prevent this - only a good anti-virus software program can. Contd. However, once installed on your PC, many viruses and Trojans "call home" using the internet to the hacker that designed it. This lets the hacker activate the Trojan and he/she can now use your PC for his/her own purposes. A firewall can block the call home and can alert you if there is suspicious behavior taking place on your system. The key to security awareness is embedded in the word security If not you, who? If not now, when? FUTURE TRENDS Evolution Security FUTURE DEVELOPMENTS IP Security (IPSec) standards Level of fragmentation in the firewall market Summary References www.howstuffworks.com http://www.microsoft.com http://www.securityfocus.com www.google.com http://grace.com/us-firewalls.htm http://www.kerio.com/us/supp_kpf_manual.html http://www.broadbandreports.com/faq/security/2.5.1. http://www.firewall-software.com Glossary ASDL (Asymmetric Digital Subscriber Line): A new technology that provides high transmission speeds for video and voice to homes over ordinary copper telephone wire. DMZ (Demilitarized Zone): An area outside the firewall that guards valuable information inside the firewall. Firewall: A computer firewall protects networked computers from intentional hostile intrusion that could compromise confidentiality or result in data corruption or denial of service. It may be a hardware device or a software program running on a secure host computer.