Document
... Individuals or organizations distribute unsolicited e-mail with hidden or false information in order to sell products, conduct phishing schemes, distribute spyware/malware, or attack organizations (i.e., denial of ...
... Individuals or organizations distribute unsolicited e-mail with hidden or false information in order to sell products, conduct phishing schemes, distribute spyware/malware, or attack organizations (i.e., denial of ...
Traditional UNIX kernels
... operating systems and more To date, Apple MAC OS X is the most widely used desktop version of UNIX ...
... operating systems and more To date, Apple MAC OS X is the most widely used desktop version of UNIX ...
Chapter 1: Security Problems in Computing
... assessment, one asks what assets have value and should be protected. In some environments, such as banking there are many objects that have obvious value – big stacks of $100 bills, for example. As we saw in one of the stories above, there were also assets that had great value, although the value wa ...
... assessment, one asks what assets have value and should be protected. In some environments, such as banking there are many objects that have obvious value – big stacks of $100 bills, for example. As we saw in one of the stories above, there were also assets that had great value, although the value wa ...
Remote Access - York Technical College
... Key – binary number made up of a large number of bits ...
... Key – binary number made up of a large number of bits ...
slides - network systems lab @ sfu
... Protection and security OS should provide secure and protected access to data Protection: involves ensuring that all access to system resources is controlled Security: of the system from outsiders requires user authentication ...
... Protection and security OS should provide secure and protected access to data Protection: involves ensuring that all access to system resources is controlled Security: of the system from outsiders requires user authentication ...
module 2 network security unit 1
... 1. Keep patches and updates current Cyber criminals exploit vulnerabilities in operating systems, software applications, web browsers and browser plug-ins when administrators are lax(careful) about applying patches and updates. In particular, verify that office computers are running current versions ...
... 1. Keep patches and updates current Cyber criminals exploit vulnerabilities in operating systems, software applications, web browsers and browser plug-ins when administrators are lax(careful) about applying patches and updates. In particular, verify that office computers are running current versions ...
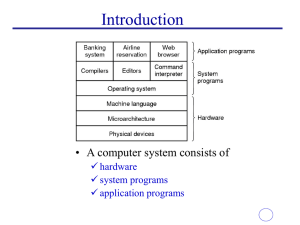
Operating systems Operating systems Protected Objects
... acts as an intermediary between a user of a computer and the computer hardware. • The purpose is to provide an environment in which a user can execute programs in a convenient and efficient manner. ...
... acts as an intermediary between a user of a computer and the computer hardware. • The purpose is to provide an environment in which a user can execute programs in a convenient and efficient manner. ...
virtual machine
... jobs running concurrently, resources must be allocated to each of them – Accounting - To keep track of which users use how much and what kinds of computer resources – Protection and security - The owners of information stored in a multiuser or networked computer system may want to control use of tha ...
... jobs running concurrently, resources must be allocated to each of them – Accounting - To keep track of which users use how much and what kinds of computer resources – Protection and security - The owners of information stored in a multiuser or networked computer system may want to control use of tha ...
VirtuWind–Security in a Virtual and Programmable Industrial
... QoS-awareness to the overlaying applications. Mechanisms for ensuring accountability of controller actions affecting cyber-physical systems will be enabled. In addition, north bound interfaces (interfaces to the business applications) should allow applications to express their requirements in terms ...
... QoS-awareness to the overlaying applications. Mechanisms for ensuring accountability of controller actions affecting cyber-physical systems will be enabled. In addition, north bound interfaces (interfaces to the business applications) should allow applications to express their requirements in terms ...
Thomas Edison Associates Report on how to install and optimizing
... computer. We can't even install a software without the help of an Operating System. The Operating System acts as a middleman between the user and the computer. It allows the user to install software he need and control the functions of Hardware components. Another important function is manage the st ...
... computer. We can't even install a software without the help of an Operating System. The Operating System acts as a middleman between the user and the computer. It allows the user to install software he need and control the functions of Hardware components. Another important function is manage the st ...
Network Technology Foundations
... Firewalls can cause a bottleneck Firewalls may not allow homebased account access to the corporate e-mail server To troubleshoot firewall problems: • Verify that you are using the correct IP address and subnet mask • Check your default gateway and verify that the computer can communicate with system ...
... Firewalls can cause a bottleneck Firewalls may not allow homebased account access to the corporate e-mail server To troubleshoot firewall problems: • Verify that you are using the correct IP address and subnet mask • Check your default gateway and verify that the computer can communicate with system ...
Week 2 _Operating system File
... machine is isolated from all other virtual machines. Suitable for research and development. System development is done on the virtual machine, instead of on a physical machine and so does not disrupt normal system operation. The virtual machine concept is difficult to implement due to the effo ...
... machine is isolated from all other virtual machines. Suitable for research and development. System development is done on the virtual machine, instead of on a physical machine and so does not disrupt normal system operation. The virtual machine concept is difficult to implement due to the effo ...
business computer and network check list
... The internet connection is reliable and does not go down I have a second internet connection for 100% up time I have clean power. Power surges and sudden outages will not damage my servers and essential network equipment. I use a UPS on essential equipment When services on my server stop, they are d ...
... The internet connection is reliable and does not go down I have a second internet connection for 100% up time I have clean power. Power surges and sudden outages will not damage my servers and essential network equipment. I use a UPS on essential equipment When services on my server stop, they are d ...
CMPT 880: Internet Architectures and Protocols
... Protection and security OS should provide secure and protected access to data Protection: involves ensuring that all access to system resources is controlled Security: of the system from outsiders requires user authentication ...
... Protection and security OS should provide secure and protected access to data Protection: involves ensuring that all access to system resources is controlled Security: of the system from outsiders requires user authentication ...
Data Security - Devi Ahilya Vishwavidyalaya
... Information Security is a complicated area and can be addressed by well-trained and experienced Professionals. “When there is an attack on the system with the help of different threats, it means that our system is working very slowly, damaged and our information are unsecured” is called Informatio ...
... Information Security is a complicated area and can be addressed by well-trained and experienced Professionals. “When there is an attack on the system with the help of different threats, it means that our system is working very slowly, damaged and our information are unsecured” is called Informatio ...
CS 502 Introduction to Operating Systems
... – Operating system transforms physical resources into virtual resources that provide similar functionality to their physical counterpart, but have a simper interface. ...
... – Operating system transforms physical resources into virtual resources that provide similar functionality to their physical counterpart, but have a simper interface. ...
DATASHEET Malwarebytes Endpoint Security
... Malwarebytes is the next-gen cybersecurity company that millions worldwide trust. Malwarebytes proactively protects people and businesses against dangerous threats such as malware, ransomware, and exploits that escape detection by traditional antivirus solutions. The company’s flagship product combi ...
... Malwarebytes is the next-gen cybersecurity company that millions worldwide trust. Malwarebytes proactively protects people and businesses against dangerous threats such as malware, ransomware, and exploits that escape detection by traditional antivirus solutions. The company’s flagship product combi ...
2. OS Components
... Protection & Security refer to a mechanism for controlling access by programs, processes, or users to both system and user resources The protection mechanism: When several separate processes execute concurrently, it should not be ...
... Protection & Security refer to a mechanism for controlling access by programs, processes, or users to both system and user resources The protection mechanism: When several separate processes execute concurrently, it should not be ...
Computer Networking and Security
... Course Activities: Students will identify the most appropriate components for building a desktop computer from scratch to ensure compatibility and budget requirements. Students will assemble and disassemble computers. Students will also work with laptops, computer peripherals and mobile devices. ...
... Course Activities: Students will identify the most appropriate components for building a desktop computer from scratch to ensure compatibility and budget requirements. Students will assemble and disassemble computers. Students will also work with laptops, computer peripherals and mobile devices. ...
security threats: a guide for small and medium
... had to shut down their entire network due to an infection of a version of a worm called Mytob. Most of the time we do not hear of small or medium-sized businesses becoming victims of such infections because it is not in their interest to publicize these incidents. Many small or medium-sized business ...
... had to shut down their entire network due to an infection of a version of a worm called Mytob. Most of the time we do not hear of small or medium-sized businesses becoming victims of such infections because it is not in their interest to publicize these incidents. Many small or medium-sized business ...
CSC 405 Introduction to Computer Security
... – There must be a clear mapping from security requirements to the design – Validate that the design has been done correctly • A mapping from security requirements to design to tests ...
... – There must be a clear mapping from security requirements to the design – Validate that the design has been done correctly • A mapping from security requirements to design to tests ...
Network Security For Distributed Simulation Systems
... networks Many civil applications - use Internet, lack security Use Internet Protocol Security (IPSEC) end-to-end mechanism for protecting data using tunneling Alternatively use a virtual private network (simulates a private network over a public network such as the Internet) VPN, which can be enh ...
... networks Many civil applications - use Internet, lack security Use Internet Protocol Security (IPSEC) end-to-end mechanism for protecting data using tunneling Alternatively use a virtual private network (simulates a private network over a public network such as the Internet) VPN, which can be enh ...
Desktop Linux ready for prime time and on a screen near you
... Stability . Since Linux is based on the stable UNIX operating system, it inherits that stability and reliability. Our Linux servers have uptimes in the MONTHS. Linux is open-source, which means the source code is readily available to anyone who wants it. Since the source code available, thousands of ...
... Stability . Since Linux is based on the stable UNIX operating system, it inherits that stability and reliability. Our Linux servers have uptimes in the MONTHS. Linux is open-source, which means the source code is readily available to anyone who wants it. Since the source code available, thousands of ...
Operating Systems - Metcalfe County Schools
... ▫ 1. Verify that all hardware is certified to work with the selected OS. ▫ 2. Verify that the hardware resources meet or exceed the published minimum requirements. ▫ 3. Confirm that the appropriate installation medium is available. Usually DVD or CD ▫ 4. If the OS is to be installed on a system that ...
... ▫ 1. Verify that all hardware is certified to work with the selected OS. ▫ 2. Verify that the hardware resources meet or exceed the published minimum requirements. ▫ 3. Confirm that the appropriate installation medium is available. Usually DVD or CD ▫ 4. If the OS is to be installed on a system that ...
Chapter 1 Operating System Fundamentals - computerscience
... XP operating systems all share common elements in their GUIs. • When using the Windows GUI, right-clicking on the My Computer icon, and selecting Properties from the popup menu will check what version of Windows is currently on the system. • The version of the OS software will be displayed on the Ge ...
... XP operating systems all share common elements in their GUIs. • When using the Windows GUI, right-clicking on the My Computer icon, and selecting Properties from the popup menu will check what version of Windows is currently on the system. • The version of the OS software will be displayed on the Ge ...