Network Security
... Strong, but flexible firewall and proxy Schools’ faculty should have responsibility of supervising the access of indecent websites Children’s Internet Protection Act (CIPA) signed into law in December 2000: ...
... Strong, but flexible firewall and proxy Schools’ faculty should have responsibility of supervising the access of indecent websites Children’s Internet Protection Act (CIPA) signed into law in December 2000: ...
Embedded Operating Systems and Linux
... • An embedded OS is an operating system which runs on any embedded platform. • Embedded platforms are generally required to function without human intervention. • A typical embedded system consists of a single-board microcomputer or SOC with an OS and some software loaded in ROM. • It will not usual ...
... • An embedded OS is an operating system which runs on any embedded platform. • Embedded platforms are generally required to function without human intervention. • A typical embedded system consists of a single-board microcomputer or SOC with an OS and some software loaded in ROM. • It will not usual ...
Siveillance Vantage
... recognizes the caller’s number and – if configured to – routes the call to a dedicated team of operators according to the requested service. Caller data, such as name and location, are identified and the location is displayed in the GIS. Siveillance Vantage also offers integrated control for communi ...
... recognizes the caller’s number and – if configured to – routes the call to a dedicated team of operators according to the requested service. Caller data, such as name and location, are identified and the location is displayed in the GIS. Siveillance Vantage also offers integrated control for communi ...
Security: Protection Mechanisms, Trusted Systems
... into C1 and C2. C1 identifies cooperating users with the same level of protection. C2 allows user-level access control. – B – All the properties of C, however each object may have unique sensitivity labels. Divided into B1, B2, and B3. – A – Uses formal design and verification techniques to ensure ...
... into C1 and C2. C1 identifies cooperating users with the same level of protection. C2 allows user-level access control. – B – All the properties of C, however each object may have unique sensitivity labels. Divided into B1, B2, and B3. – A – Uses formal design and verification techniques to ensure ...
Operating System Concepts, Terminology, and History
... • For purposes of this book, we'll consider an operating system to be the supporting software structure on which application programs run. – This support structure includes the facilities to manage the computer system's resources and any utility programs needed to maintain and configure the operatin ...
... • For purposes of this book, we'll consider an operating system to be the supporting software structure on which application programs run. – This support structure includes the facilities to manage the computer system's resources and any utility programs needed to maintain and configure the operatin ...
Answers
... Note: At this point, these exercises do not have to be turned in. The point of the exercises is to help you reflect on and better understand the course material. We will have an in-class discussion on these exercises on 1/23. 1. Who are the two main programmers that wrote UNIX, and what were their r ...
... Note: At this point, these exercises do not have to be turned in. The point of the exercises is to help you reflect on and better understand the course material. We will have an in-class discussion on these exercises on 1/23. 1. Who are the two main programmers that wrote UNIX, and what were their r ...
Linux For Beginners - Hazelwood Linux Users Group
... University of Helsinki in Finland, and then released to the Internet as an Open Source project. Since then thousands of people have contributed to make Linux (combined with GNU software) one of the most stable and full-featured operating systems available. Tux, the penguin shown above, is the offici ...
... University of Helsinki in Finland, and then released to the Internet as an Open Source project. Since then thousands of people have contributed to make Linux (combined with GNU software) one of the most stable and full-featured operating systems available. Tux, the penguin shown above, is the offici ...
HW2 Solution 1. What are the advantages of using a higher
... interpreter. One way is to allow the command interpreter to contain the code needed to execute the command. The other way is to implement the commands through system programs. Compare and contrast the two approaches. In the first approach, upon the user issuing a command, the interpreter jumps to th ...
... interpreter. One way is to allow the command interpreter to contain the code needed to execute the command. The other way is to implement the commands through system programs. Compare and contrast the two approaches. In the first approach, upon the user issuing a command, the interpreter jumps to th ...
Case study Compute privacy
... Periodic penetration testing (enterprise nets) Centralized patch management (enterprise nets) Anti-DOS mechanisms (ISPs) ...
... Periodic penetration testing (enterprise nets) Centralized patch management (enterprise nets) Anti-DOS mechanisms (ISPs) ...
os_ch1-2008
... – User ID then associated with all files, processes of that user to determine access control – Group identifier (group ID) allows set of users to be defined and controls managed, then also associated with each process, file – Privilege escalation allows user to change to effective ID with more right ...
... – User ID then associated with all files, processes of that user to determine access control – Group identifier (group ID) allows set of users to be defined and controls managed, then also associated with each process, file – Privilege escalation allows user to change to effective ID with more right ...
Emerging Threats to Business Security
... losses generated by cleanup are considerable, so businesses should consider implementing web filtering, to prevent infection with this and other types of malware. With P2P file sharing already a commonplace thing, the number, diversity and impact of file infectors is bound to grow significantly in t ...
... losses generated by cleanup are considerable, so businesses should consider implementing web filtering, to prevent infection with this and other types of malware. With P2P file sharing already a commonplace thing, the number, diversity and impact of file infectors is bound to grow significantly in t ...
Enhancing the Security and Capacity of Collaborative Software for
... For security, we propose to integrate the security model such Bell LaPadula Model so that only persons with proper security clearance or category can see the documents or ...
... For security, we propose to integrate the security model such Bell LaPadula Model so that only persons with proper security clearance or category can see the documents or ...
Operating systems
... operator as intermediary is that the users have no interaction with their jobs once they are submitted to the operator. New operating systems were developed that allowed a program being executed to carry on a dialogue with the user through remote terminals (interactive processing) – in which the u ...
... operator as intermediary is that the users have no interaction with their jobs once they are submitted to the operator. New operating systems were developed that allowed a program being executed to carry on a dialogue with the user through remote terminals (interactive processing) – in which the u ...
CompTIA Strata™ Fundamentals of IT Technology
... maintenance of computers. This test is intended for candidates completing their “secondary” education, considering the pursuit of a CompTIA A+ certification, and/or advanced home users who wish to further their IT knowledge. Domain ...
... maintenance of computers. This test is intended for candidates completing their “secondary” education, considering the pursuit of a CompTIA A+ certification, and/or advanced home users who wish to further their IT knowledge. Domain ...
Simple TCP/IP Services
... respond with a welcome message called a banner – Banners provide information about the responding program – You may want to suppress or modify banner information to thwart attackers – Scanning programs use this information to detect programs and versions ...
... respond with a welcome message called a banner – Banners provide information about the responding program – You may want to suppress or modify banner information to thwart attackers – Scanning programs use this information to detect programs and versions ...
The Linux Kernel and Acquiring Forensic Images of Hard Disks
... odd number of sectors was reduced by 512 bytes, this was a small loss and could be easily overlooked. Only users who attempted to access the last sector on a drive with an odd number of sectors that had been formatted on another operating system would find themselves unable to read part of their dat ...
... odd number of sectors was reduced by 512 bytes, this was a small loss and could be easily overlooked. Only users who attempted to access the last sector on a drive with an odd number of sectors that had been formatted on another operating system would find themselves unable to read part of their dat ...
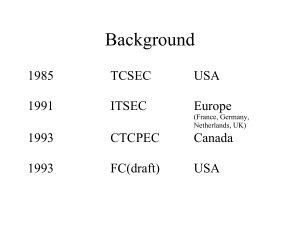
Common Criteria
... Information Assurance G&PM: 5.2.20. Consult the IA Technical Framework (IATF) and published Common Criteria (CC) Protection Profiles for guidance regarding common classes of network and system attacks, interoperability and compatibility with the defense-in-depth strategy, and IA solutions that shoul ...
... Information Assurance G&PM: 5.2.20. Consult the IA Technical Framework (IATF) and published Common Criteria (CC) Protection Profiles for guidance regarding common classes of network and system attacks, interoperability and compatibility with the defense-in-depth strategy, and IA solutions that shoul ...
Guide to Operating System Security
... Uses asymmetrical public and private keys along with an algorithm that relies on factoring large prime numbers The algorithm uses a trapdoor function to manipulate prime numbers More secure than DES and 3DES Used in Internet Explorer and Netscape Navigator ...
... Uses asymmetrical public and private keys along with an algorithm that relies on factoring large prime numbers The algorithm uses a trapdoor function to manipulate prime numbers More secure than DES and 3DES Used in Internet Explorer and Netscape Navigator ...
Test 1 Operating Systems and Networking CS
... moved? How does the system realize these specific set of events via the system module A? What role should A play in this setup if one of the things it must do is to get the CPU first for whatever it wants to do. ...
... moved? How does the system realize these specific set of events via the system module A? What role should A play in this setup if one of the things it must do is to get the CPU first for whatever it wants to do. ...
PPT - RAMP - University of California, Berkeley
... pipeline/cache/bus-interface • Thus, prefer to keep existing port interface • Also provides forward compatibility with soft-cores ...
... pipeline/cache/bus-interface • Thus, prefer to keep existing port interface • Also provides forward compatibility with soft-cores ...
Computer Connections: Lesson 6 – Operating Systems
... Lesson 2 that the BIOS is responsible for waking up the computer when you turn it on to remind it of all the parts it has and what they do. The operating system also contains other programs that are important, but not essential to making the computer run. The part of the operating system that contai ...
... Lesson 2 that the BIOS is responsible for waking up the computer when you turn it on to remind it of all the parts it has and what they do. The operating system also contains other programs that are important, but not essential to making the computer run. The part of the operating system that contai ...
Linux+ Guide to Linux Certification Chapter One Introduction to Linux
... and many additional software packages are freely developed and improved upon by a large community of software developers in collaboration • Since Linux is published under GNU Public License, it is referred to as Open source Software • Companies find Linux a stable, low-risk, and flexible alternative ...
... and many additional software packages are freely developed and improved upon by a large community of software developers in collaboration • Since Linux is published under GNU Public License, it is referred to as Open source Software • Companies find Linux a stable, low-risk, and flexible alternative ...