Addressing security threats and vulnerabilities
... – To defend from these threats you must understand the technology ...
... – To defend from these threats you must understand the technology ...
COS 318: Operating Systems Introduction Kai Li and Andy Bavier Computer Science Department
... New storage = sum of all old storage (ever) New processing = sum of all old processing. ...
... New storage = sum of all old storage (ever) New processing = sum of all old processing. ...
CS 381 Operating Systems
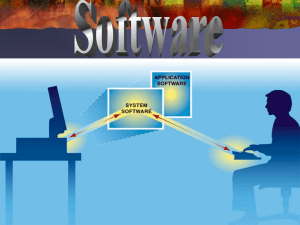
... An operating system is an intermediary between the user programs and the computer hardware resources. By managing disparate hardware resources, an OS shields user programs from the complexities of individual hardware devices and issues such as concurrency and failure. The user gets an abstraction of ...
... An operating system is an intermediary between the user programs and the computer hardware resources. By managing disparate hardware resources, an OS shields user programs from the complexities of individual hardware devices and issues such as concurrency and failure. The user gets an abstraction of ...
CS 414/415 Systems Programming and
... – Security mechanisms needed to isolate users – Requires memory protection hardware for isolation – Optimizes for response time at the cost of throughput ...
... – Security mechanisms needed to isolate users – Requires memory protection hardware for isolation – Optimizes for response time at the cost of throughput ...
Chapter 2 Operating System Overview
... – Prevents a job from monopolizing the system (when allocated time is up, job is stopped) ...
... – Prevents a job from monopolizing the system (when allocated time is up, job is stopped) ...
Bandwidth Management
... 1.5 million licensed tracks of music from major labels Hollywood blockbusters, cult classics, and independent films Robust community features that allow students with similar music, video and programming interests to connect, share and explore on their campus ...
... 1.5 million licensed tracks of music from major labels Hollywood blockbusters, cult classics, and independent films Robust community features that allow students with similar music, video and programming interests to connect, share and explore on their campus ...
Systems Administrator needed for DoD Griffin Cyberspace Defense
... Assigns personnel to various projects, directs their activities, and evaluates their work. Ensures long-term requirements of systems operations and administration are included in the overall information systems planning of the organization. Responsible for the installation, maintenance, configuratio ...
... Assigns personnel to various projects, directs their activities, and evaluates their work. Ensures long-term requirements of systems operations and administration are included in the overall information systems planning of the organization. Responsible for the installation, maintenance, configuratio ...
Trusted Operating Systems
... • e.g., reference monitor can invoke and pass data securely to audit routine CS 450/650 Lecture 22: Trusted Operating System ...
... • e.g., reference monitor can invoke and pass data securely to audit routine CS 450/650 Lecture 22: Trusted Operating System ...
Operating systems
... application programs and users. Can you identify the following operating systems? ? : It was developed by Sun Microsystems in 1996 for use in embedded systems (i.e. combinations of circuitry and software built into other products). ? : a high performance, yet completely free, Unix-like operating sys ...
... application programs and users. Can you identify the following operating systems? ? : It was developed by Sun Microsystems in 1996 for use in embedded systems (i.e. combinations of circuitry and software built into other products). ? : a high performance, yet completely free, Unix-like operating sys ...
Network Infrastructure Security
... retrieval of programs and data used by a group of people. LAN software and practices also need to provide for the security of these programs and data. ...
... retrieval of programs and data used by a group of people. LAN software and practices also need to provide for the security of these programs and data. ...
SAFEnet Becomes First PACS Platform to
... SAN ANTONIO, Texas – Monitor Dynamics announced in February 2008 that the SAFEnet Unified Security Platform received the new DIACAP (Department of Defense Information Assurance Certification and Accreditation Process) certification from an independent third-party laboratory for approval to operate o ...
... SAN ANTONIO, Texas – Monitor Dynamics announced in February 2008 that the SAFEnet Unified Security Platform received the new DIACAP (Department of Defense Information Assurance Certification and Accreditation Process) certification from an independent third-party laboratory for approval to operate o ...
Operating System Functions
... a time, but has many different programs running at once. •This is because the OS cleverly (and quickly!) allocates data to and from the CPU, prioritising the programmes need data processing before others. •Because all of this happens in milliseconds, it gives the impression of all the programs worki ...
... a time, but has many different programs running at once. •This is because the OS cleverly (and quickly!) allocates data to and from the CPU, prioritising the programmes need data processing before others. •Because all of this happens in milliseconds, it gives the impression of all the programs worki ...
NITC yearly Work Plan FY2065/66
... browsers can display advertisements tailored to that user. Slow down the computer it’s running on. Adware sometimes displays a banner that notifies the user of its presence ...
... browsers can display advertisements tailored to that user. Slow down the computer it’s running on. Adware sometimes displays a banner that notifies the user of its presence ...
virtual machine
... – OS should take the appropriate action to ensure correct and consistent computing – OS should provide debugging facilities ...
... – OS should take the appropriate action to ensure correct and consistent computing – OS should provide debugging facilities ...
The Active Streams Approach to adaptive distributed systems
... processes, the correct way is to directly quantify the amount of user interaction for the various processes. Devices that mediate between the user and a process will be called HuC devices e.g. keyboard, mouse, screen, joystick, speaker. – For now, we will focus on the first three… 4.13 Advanced Oper ...
... processes, the correct way is to directly quantify the amount of user interaction for the various processes. Devices that mediate between the user and a process will be called HuC devices e.g. keyboard, mouse, screen, joystick, speaker. – For now, we will focus on the first three… 4.13 Advanced Oper ...
Document
... grid and left behind software programs that could be used to disrupt the system, according to current and former national-security officials. The spies came from China, Russia and other countries, these officials said, and were believed to be on a mission to navigate the U.S. electrical system and i ...
... grid and left behind software programs that could be used to disrupt the system, according to current and former national-security officials. The spies came from China, Russia and other countries, these officials said, and were believed to be on a mission to navigate the U.S. electrical system and i ...
Identify Security Risks and Threats
... Identify security risks and threats Analyze and prioritize security risks Security risk tracking, planning, and scheduling ...
... Identify security risks and threats Analyze and prioritize security risks Security risk tracking, planning, and scheduling ...
Operating Systems
... Utility software: programs for performing fundamental activities, but not included in operating systems. n ...
... Utility software: programs for performing fundamental activities, but not included in operating systems. n ...
APT 2040: OPERATING SYSTEMS Pre
... its working. The students will also get hand-on experience and good working knowledge to work in DOS, Windows and UNIX environments. The aim is to gain proficiency in using various operating systems after undergoing this course. Course Description The course covers the concepts and architecture of a ...
... its working. The students will also get hand-on experience and good working knowledge to work in DOS, Windows and UNIX environments. The aim is to gain proficiency in using various operating systems after undergoing this course. Course Description The course covers the concepts and architecture of a ...
Commercial Real-Time Operating Systems – An
... POSIX-compliant Unix-like real-time operating system. Microkernel design – kernel provides essential threads and real-time services use of a microkernel allows users (developers) to turn off any functionality they do not require without having to change the OS itself. The system is quite small, fitt ...
... POSIX-compliant Unix-like real-time operating system. Microkernel design – kernel provides essential threads and real-time services use of a microkernel allows users (developers) to turn off any functionality they do not require without having to change the OS itself. The system is quite small, fitt ...
Global Information Assurance Certification (GIAC) develops and administers the premier
... (GSE). For good reason. It’s the most prestigious, most demanding certification in the information security industry. The GSE’s performancebased, hands-on nature sets it apart from any other certification in the IT security industry. Those who earn the GSE master the wide variety of skills, across m ...
... (GSE). For good reason. It’s the most prestigious, most demanding certification in the information security industry. The GSE’s performancebased, hands-on nature sets it apart from any other certification in the IT security industry. Those who earn the GSE master the wide variety of skills, across m ...
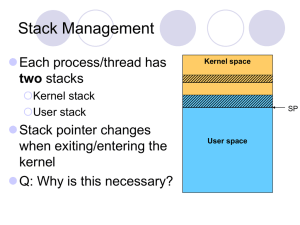
Protection
... No. User-mode code does not have permission to access the kernel’s address space. If it tries, the hardware raises an exception, which is safely handled by the OS More generally, no user mode code should ever be a security vulnerability. Unless the OS has a bug… ...
... No. User-mode code does not have permission to access the kernel’s address space. If it tries, the hardware raises an exception, which is safely handled by the OS More generally, no user mode code should ever be a security vulnerability. Unless the OS has a bug… ...