Your iPhone or Mac could be hacked with an iMessage
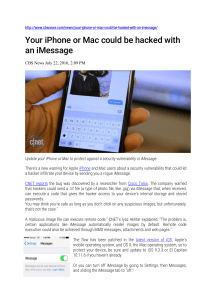
... There's a new warning for Apple iPhone and Mac users about a security vulnerability that could let a hacker infiltrate your device by sending you a rogue iMessage. CNET reports the bug was discovered by a researcher from Cisco Talos. The company warned that hackers could send a .tif file (a type of ...
... There's a new warning for Apple iPhone and Mac users about a security vulnerability that could let a hacker infiltrate your device by sending you a rogue iMessage. CNET reports the bug was discovered by a researcher from Cisco Talos. The company warned that hackers could send a .tif file (a type of ...
operating system
... The device manager, or input/output manager, is responsible for access to input/ output devices. There are limitations on the number and speed of input/output devices in a computer system. The device manager monitors every input/output device constantly to ensure that the device is functioning pro ...
... The device manager, or input/output manager, is responsible for access to input/ output devices. There are limitations on the number and speed of input/output devices in a computer system. The device manager monitors every input/output device constantly to ensure that the device is functioning pro ...
HDD for Operating System Concepts
... Education and Research Department, Infosys Technologies Limited. This document is not for general distribution and is meant for use only for the person they are specifically issued to. This document shall not be loaned to anyone, within or outside Infosys, including its customers. Copying or unautho ...
... Education and Research Department, Infosys Technologies Limited. This document is not for general distribution and is meant for use only for the person they are specifically issued to. This document shall not be loaned to anyone, within or outside Infosys, including its customers. Copying or unautho ...
Course Introduction
... – Make computers easier to use – Improve the utilization of computing resources ...
... – Make computers easier to use – Improve the utilization of computing resources ...
COS 318: Operating Systems Introduction Margaret Martonosi and Vivek Pai Computer Science Department
... 1 hour: 98.6%, 6 hours: 92%, 1 day: 71.7% 3 days: 36.8%, 7 days: 9.7% ...
... 1 hour: 98.6%, 6 hours: 92%, 1 day: 71.7% 3 days: 36.8%, 7 days: 9.7% ...
Slides - Bilkent University Computer Engineering Department
... Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all files, processes of that user to determine access control ...
... Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all files, processes of that user to determine access control ...
Protocol Overview
... • The X.500 standard is a global directory service that is based on a replicated distributed database • Programs access the directory services using the X/Open Directory Service (XDS) API’s. • The XDS API’s permit programs to read, compare, update, add, and remove directory entries; list directories ...
... • The X.500 standard is a global directory service that is based on a replicated distributed database • Programs access the directory services using the X/Open Directory Service (XDS) API’s. • The XDS API’s permit programs to read, compare, update, add, and remove directory entries; list directories ...
Application Service Provider Security Requirements
... Any University department entering into an agreement to use software operated by an ASP or to provide protected data to a vendor who will store it on its own system (outside CSUN) must ensure that the vendor chosen complies with this policy. Departments must obtain the review and approval of the CSU ...
... Any University department entering into an agreement to use software operated by an ASP or to provide protected data to a vendor who will store it on its own system (outside CSUN) must ensure that the vendor chosen complies with this policy. Departments must obtain the review and approval of the CSU ...
Windows NT Operating System
... • Windows NT servers are called protected subsystem because each one resides in a separate process whose memory is protected from other processes by the NT executive’s virtual memory system. They communicate with each other by passing messages. • The NT executive is capable of supporting any number ...
... • Windows NT servers are called protected subsystem because each one resides in a separate process whose memory is protected from other processes by the NT executive’s virtual memory system. They communicate with each other by passing messages. • The NT executive is capable of supporting any number ...
Software - Hoxie Public Schools
... other software to communicate with each other. There are many brands and versions of operating systems. An operating system is designed to work with a specific processor chip. – For example, Windows operating systems are designed to work with an Intel processor (or clone) and will not usually work o ...
... other software to communicate with each other. There are many brands and versions of operating systems. An operating system is designed to work with a specific processor chip. – For example, Windows operating systems are designed to work with an Intel processor (or clone) and will not usually work o ...
Web Application Security
... possible (ask the user to reenter instead) Instead of storing encrypted passwords, use a one-way function to hash the psswords. Choose a proven cryptography algorithm to encrypt data Store secrets such as keys, certificates, password ...
... possible (ask the user to reenter instead) Instead of storing encrypted passwords, use a one-way function to hash the psswords. Choose a proven cryptography algorithm to encrypt data Store secrets such as keys, certificates, password ...
Intrusion Detection Technique by using K
... • With the impending era of internet, the network security has become the key foundation for lot of financial and business web applications. ...
... • With the impending era of internet, the network security has become the key foundation for lot of financial and business web applications. ...
Document
... today’s Microsoft OSs (2000, XP, Vista, 2008). It is a Microsoft proprietary file system that provides many improvements over the old FAT file system, such as better security, extensions, longer names, etc. FAT: File Allocation Table use to be the defacto standard for all operating systems and is st ...
... today’s Microsoft OSs (2000, XP, Vista, 2008). It is a Microsoft proprietary file system that provides many improvements over the old FAT file system, such as better security, extensions, longer names, etc. FAT: File Allocation Table use to be the defacto standard for all operating systems and is st ...
Introduction to Object Technology
... Linus Torvalds, a Finnish student of computer science, wrote the initial version ...
... Linus Torvalds, a Finnish student of computer science, wrote the initial version ...
View Presentation - InfoSec Nashville
... (more than one for spouse & family coverage), date(s) of birth, contract number, group number, type of plan (Individual/Group, HMO/PPO, deductible and copay information), and insurer contact information for customer service and filing claims). Note: when there is a dental, vision, or chiropractic pl ...
... (more than one for spouse & family coverage), date(s) of birth, contract number, group number, type of plan (Individual/Group, HMO/PPO, deductible and copay information), and insurer contact information for customer service and filing claims). Note: when there is a dental, vision, or chiropractic pl ...
Scale and Performance in the Denali Isolation Kernel
... memory protection techniques to virtualize some of the instructions. Since Delani does not support legacy operating systems, those instructions are simply defined to have ambiguous semantics. At worst, the VM will harm only itself. However, such instructions are rarely used, and none are emitted by ...
... memory protection techniques to virtualize some of the instructions. Since Delani does not support legacy operating systems, those instructions are simply defined to have ambiguous semantics. At worst, the VM will harm only itself. However, such instructions are rarely used, and none are emitted by ...
9781111543709 _PPT_ch04
... Importing Custom Privacy Settings • Standardizing the privacy settings of all users: – Click the Import button in the Privacy tab – Import custom privacy settings from a file ...
... Importing Custom Privacy Settings • Standardizing the privacy settings of all users: – Click the Import button in the Privacy tab – Import custom privacy settings from a file ...
Operating Systems Essay Research Paper Operating Systems
... by the 1980’s, technology had advanced a great deal from the days of the mainframe computers and vacuum tubes. With the introduction of large-scale Integration circuits (LSI) and silicon chips consisting of thousands of transistors, computers reached a new level. Microcomputers, which were physicall ...
... by the 1980’s, technology had advanced a great deal from the days of the mainframe computers and vacuum tubes. With the introduction of large-scale Integration circuits (LSI) and silicon chips consisting of thousands of transistors, computers reached a new level. Microcomputers, which were physicall ...
Introduction
... CPU, memory, I/O devices Operating system Controls and coordinates use of hardware among various applications and users Application programs – define the ways in which the system resources are used to solve the computing problems of the users ...
... CPU, memory, I/O devices Operating system Controls and coordinates use of hardware among various applications and users Application programs – define the ways in which the system resources are used to solve the computing problems of the users ...
Important Concepts.
... Assurance that data received are exactly as sent by an authorized entity. (i.e., contain no modification, insertion, deletion, or replay). Data integrity can be maintained through the use of various error checking methods and validation procedures. Data integrity and data security are related te ...
... Assurance that data received are exactly as sent by an authorized entity. (i.e., contain no modification, insertion, deletion, or replay). Data integrity can be maintained through the use of various error checking methods and validation procedures. Data integrity and data security are related te ...
C.2. Vulnerabilities
... teaching lab is managed by a faculty member who has many other responsibilities or by a student manager who may have had little training. Universities are havens for free exchange of ideas. Thus, their access controls typically are configured to promote sharing and wide access to a population that c ...
... teaching lab is managed by a faculty member who has many other responsibilities or by a student manager who may have had little training. Universities are havens for free exchange of ideas. Thus, their access controls typically are configured to promote sharing and wide access to a population that c ...