www.itgovernance.co.uk/training
... People are your weakest link – Strengthen awareness to improve the robustness of your ISMS Training aids are a tool for getting general staff involved in discussing and understanding the sometimes complex data security issues which might impinge on how they work – and to do so in a low impact, low p ...
... People are your weakest link – Strengthen awareness to improve the robustness of your ISMS Training aids are a tool for getting general staff involved in discussing and understanding the sometimes complex data security issues which might impinge on how they work – and to do so in a low impact, low p ...
Using Information Technology - City University of Hong Kong
... Windows NT - Microsoft’s multitasking OS designed to run on network servers; it allows multiple users to share resources such as data and programs Windows XP - successor to Windows NT ...
... Windows NT - Microsoft’s multitasking OS designed to run on network servers; it allows multiple users to share resources such as data and programs Windows XP - successor to Windows NT ...
Distributed Computing Systems
... • OSes can be different (Windows or Linux) • Typical services: rlogin, rcp – Fairly primitive way to share files ...
... • OSes can be different (Windows or Linux) • Typical services: rlogin, rcp – Fairly primitive way to share files ...
Operating Systems - School of Computer Science, University of
... Protection - any mechanism for controlling access of processes or users to resources defined by the OS Security - defense of the system against internal and external attacks Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
... Protection - any mechanism for controlling access of processes or users to resources defined by the OS Security - defense of the system against internal and external attacks Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
Introduction - GMU Computer Science
... • Delivery via web site, e-mail or instant message, the attack asks users to click on a link to “re-validate” or “re-activate” their account. The link displays a believable facsimile of your site and brand to con users into submitting private details • Sends a threatening e-mail to users telling the ...
... • Delivery via web site, e-mail or instant message, the attack asks users to click on a link to “re-validate” or “re-activate” their account. The link displays a believable facsimile of your site and brand to con users into submitting private details • Sends a threatening e-mail to users telling the ...
Operating Systems Operating Systems Operating Systems
... – important if there is to be more than one type of computer using the operating system or if the hardware is to change. – A consistent application programming interface (API) allows a software developer to write an application on one computer and have a high level of confidence that it will run on ...
... – important if there is to be more than one type of computer using the operating system or if the hardware is to change. – A consistent application programming interface (API) allows a software developer to write an application on one computer and have a high level of confidence that it will run on ...
ch04 - Computer Science
... Mac users can buy software emulation programs that: Create a simulated Windows machine in the Mac Translate all Windows-related instructions to Mac equivalents Future applications may be tied to networks rather than to desktop platforms Microsoft.NET strategy Java, a platform-neutral com ...
... Mac users can buy software emulation programs that: Create a simulated Windows machine in the Mac Translate all Windows-related instructions to Mac equivalents Future applications may be tied to networks rather than to desktop platforms Microsoft.NET strategy Java, a platform-neutral com ...
ITS 225 (Operating Systems) Lecture Notes
... – Setup: many calls to get OS info, read DLLs into memory, etc. – stat(“hw1.pdf”) to get file information and status ...
... – Setup: many calls to get OS info, read DLLs into memory, etc. – stat(“hw1.pdf”) to get file information and status ...
Information Systems and Networks
... Power failures, floods, fires, or other natural disasters can also disrupt computer systems. Domestic or offshore partnering with another company adds to system vulnerability if valuable information resides on networks and computers outside the organization’s control ...
... Power failures, floods, fires, or other natural disasters can also disrupt computer systems. Domestic or offshore partnering with another company adds to system vulnerability if valuable information resides on networks and computers outside the organization’s control ...
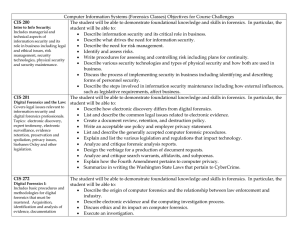
Computer Information Systems (Forensics Classes) Objectives for
... • Describe security technologies used for establishing identity and how security technologies are implemented in corporate networks. • Identify strengths and weaknesses associated with protocols designed to authenticate users. • Describe the technologies that exist at the different TCP/IP layers, in ...
... • Describe security technologies used for establishing identity and how security technologies are implemented in corporate networks. • Identify strengths and weaknesses associated with protocols designed to authenticate users. • Describe the technologies that exist at the different TCP/IP layers, in ...
Security Risks
... • Open source versions available: OpenSSH • Secure connection requires SSH running on both machines • Requires public and private key generation • Configuration options – Use one of several encryption types – Require client password – Perform port forwarding ...
... • Open source versions available: OpenSSH • Secure connection requires SSH running on both machines • Requires public and private key generation • Configuration options – Use one of several encryption types – Require client password – Perform port forwarding ...
CSC 271 – Software I: Utilities and Internals What Is an Operating
... • Time-sharing systems allowed multiple users to work interactively on a computer. • Time-sharing systems are more complex and expensive than batch systems and did not become common until the 1970s. • Time-sharing systems take advantage of the great difference between CPU speed and interactive I/O ...
... • Time-sharing systems allowed multiple users to work interactively on a computer. • Time-sharing systems are more complex and expensive than batch systems and did not become common until the 1970s. • Time-sharing systems take advantage of the great difference between CPU speed and interactive I/O ...
Tutorial 2: Question 1: The services and functions provided by an
... main categories. Briefly describe the two categories and discuss how they differ. Question 2: Describe three general methods for passing parameters to the operating system. Question 3: Describe how you could obtain a statistical profile of the amount of time spent by a program executing different se ...
... main categories. Briefly describe the two categories and discuss how they differ. Question 2: Describe three general methods for passing parameters to the operating system. Question 3: Describe how you could obtain a statistical profile of the amount of time spent by a program executing different se ...
Threads
... Many user-level threads mapped to single kernel thread. Used on systems that do not support kernel threads. ...
... Many user-level threads mapped to single kernel thread. Used on systems that do not support kernel threads. ...
CS307-slides02
... Accounting - To keep track of which users use how much and what kinds of computer resources ...
... Accounting - To keep track of which users use how much and what kinds of computer resources ...
Top 100 Network Security Tools
... After the tremendously successful 2000 and 2003 security tools surveys, Insecure.Org is delighted to release this 2006 survey. I (Fyodor) asked users from the nmap-hackers mailing list to share their favorite tools, and 3,243 people responded. This allowed me to expand the list to 100 tools, and eve ...
... After the tremendously successful 2000 and 2003 security tools surveys, Insecure.Org is delighted to release this 2006 survey. I (Fyodor) asked users from the nmap-hackers mailing list to share their favorite tools, and 3,243 people responded. This allowed me to expand the list to 100 tools, and eve ...
Authentication and Access Control
... • Software is considered malware based on the intent of the creator rather than any particular features ...
... • Software is considered malware based on the intent of the creator rather than any particular features ...
A1A_CptrArch
... (1-f) + f / N where f is the amount of code that can be parallelized, with no overhead • Not all code benefits from parallelization but certain categories of applications; e.g., games, database apps, JVM (it’s multithreaded); can take advantage of multiple processors. ...
... (1-f) + f / N where f is the amount of code that can be parallelized, with no overhead • Not all code benefits from parallelization but certain categories of applications; e.g., games, database apps, JVM (it’s multithreaded); can take advantage of multiple processors. ...
Presentation: Operating systems
... We covered five of the most important things an operating system does. Without looking back, can you recall what they were? ...
... We covered five of the most important things an operating system does. Without looking back, can you recall what they were? ...
Document
... Different applications have different needs for resources. One generalized OS cannot satisfy all the resource needs from various applications. As a result, application performances are compromised. ...
... Different applications have different needs for resources. One generalized OS cannot satisfy all the resource needs from various applications. As a result, application performances are compromised. ...
Chapter 1: Introduction
... Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all files, processes of that user to determine access control ...
... Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all files, processes of that user to determine access control ...
Security+ Guide to Network Security Fundamentals
... Gateway between an inside network and an outside network Defends against attacks aimed at the inside network; used as a security measure Unnecessary programs, services, and protocols are removed; unnecessary network ports are disabled Do not share authentication services with trusted hosts within th ...
... Gateway between an inside network and an outside network Defends against attacks aimed at the inside network; used as a security measure Unnecessary programs, services, and protocols are removed; unnecessary network ports are disabled Do not share authentication services with trusted hosts within th ...
Logical attack advisory for U.S. and Canada
... dispenser is disconnected from the ATM system, and an external electronic device (the “Black Box”) is connected to the dispenser. This device sends commands to the dispenser which results in an unauthorized dispense of cash from the ATM. All ATM models from all manufacturers are potentially at risk. ...
... dispenser is disconnected from the ATM system, and an external electronic device (the “Black Box”) is connected to the dispenser. This device sends commands to the dispenser which results in an unauthorized dispense of cash from the ATM. All ATM models from all manufacturers are potentially at risk. ...