Module 3: Operating
... – CPU scheduling can create the appearance that users have their own processor. – Spooling and a file system can provide virtual card readers and virtual line printers. – A normal user time-sharing terminal serves as the virtual machine operator’s console. ...
... – CPU scheduling can create the appearance that users have their own processor. – Spooling and a file system can provide virtual card readers and virtual line printers. – A normal user time-sharing terminal serves as the virtual machine operator’s console. ...
PPT
... resource(s) is involved? is physical reality of resource? abstraction to present to user apps? protections to guarantee? ...
... resource(s) is involved? is physical reality of resource? abstraction to present to user apps? protections to guarantee? ...
Batching processing
... Total main memory required exceeds available(I.e., 512MB is requires but only 256MB available), it creates the illusion of additional memory space by rotating back and forth of program and data between main memory and mass storage ...
... Total main memory required exceeds available(I.e., 512MB is requires but only 256MB available), it creates the illusion of additional memory space by rotating back and forth of program and data between main memory and mass storage ...
OS_Intro - SIUE Computer Science
... • Understand the purpose of each OS component • Understand how each OS component works ...
... • Understand the purpose of each OS component • Understand how each OS component works ...
Device Drivers - EMU CMPE Home Page
... Segments (Process Control Block, states of registers). TSS also has Input-Output Map showing for each of possible 64K input-output ports possibility of access to it. Windows NT/2000 is characterized by: ...
... Segments (Process Control Block, states of registers). TSS also has Input-Output Map showing for each of possible 64K input-output ports possibility of access to it. Windows NT/2000 is characterized by: ...
Linux+ Guide to Linux Certification
... proprietary and stopped supplying the sourcecode with their version of the ...
... proprietary and stopped supplying the sourcecode with their version of the ...
System Administration
... Access Controls - specific access controls can include restrictions on: • Locations from which a user can log on to the system or access its resources. • Days/times when access is granted or denied. • The ability to read, write, create and delete directories and files. • The ability to execute progr ...
... Access Controls - specific access controls can include restrictions on: • Locations from which a user can log on to the system or access its resources. • Days/times when access is granted or denied. • The ability to read, write, create and delete directories and files. • The ability to execute progr ...
Document
... breached in the last 12 months, with 64 percent of the breaches costing $2 million or more.” - csi Of those: 99% used antivirus software 98% used firewalls 91% employed physical security to protect their ...
... breached in the last 12 months, with 64 percent of the breaches costing $2 million or more.” - csi Of those: 99% used antivirus software 98% used firewalls 91% employed physical security to protect their ...
(FIPS) 140-2 - Aviat Networks
... support Security is balance between level of protection and cost FIPS 140-2 Level 2 is sweet spot for networking equipment AVIAT NETWORKS ...
... support Security is balance between level of protection and cost FIPS 140-2 Level 2 is sweet spot for networking equipment AVIAT NETWORKS ...
Operating Systems 2
... Components of an operating system Any access to a file is obtained at the discretion of the file manager. The procedure begins by requesting that the file manager grant access to the file through procedure known as opening the file. If the file manager approves the requested access, it provides ...
... Components of an operating system Any access to a file is obtained at the discretion of the file manager. The procedure begins by requesting that the file manager grant access to the file through procedure known as opening the file. If the file manager approves the requested access, it provides ...
HUNTING-AS-A-SERVICE By Accenture, Powered by Endgame
... of a breach before security analysts take action. This approach is failing. The most dangerous hackers are — with minimal cost and effort — compromising victims at will by leveraging new techniques as their weapons of choice. These approaches include single-use rotating attack patterns that don’t le ...
... of a breach before security analysts take action. This approach is failing. The most dangerous hackers are — with minimal cost and effort — compromising victims at will by leveraging new techniques as their weapons of choice. These approaches include single-use rotating attack patterns that don’t le ...
Rearchitecting System Software for the Cloud - Muli Ben
... The rise of cloud computing has also brought with it a host of new hardware support for efficient machine virtualization. New CPU, MMU, chipset, and I/O device support can greatly increase machine virtualization run-time performance, to the extent that it is now possible to run an I/O-intensive virt ...
... The rise of cloud computing has also brought with it a host of new hardware support for efficient machine virtualization. New CPU, MMU, chipset, and I/O device support can greatly increase machine virtualization run-time performance, to the extent that it is now possible to run an I/O-intensive virt ...
Teaching Computer Security using Minix
... Learn IPSec protocol, understand how it is implemented Apply comprehensive knowledge: networking, encryption/decryption, key management, access control, authentication, and security in OS kernels ...
... Learn IPSec protocol, understand how it is implemented Apply comprehensive knowledge: networking, encryption/decryption, key management, access control, authentication, and security in OS kernels ...
lec1
... facilities. Virtual memory and file system facilities together satisfy all these requirements. Virtual memory allows programs to address the memory from a logical point of view without regard to the amount of main memory available. File : persistent storage for programs and data. Can view file also ...
... facilities. Virtual memory and file system facilities together satisfy all these requirements. Virtual memory allows programs to address the memory from a logical point of view without regard to the amount of main memory available. File : persistent storage for programs and data. Can view file also ...
Operating System Security Rules
... Trusted operating systems have security features built into the operating system. The National Computer Security Center’s Rainbow series Orange Book, Trusted Computer Standards Evaluation Criteria describes several levels of trust including C1, C2, B1, B2, and B3. Currently, there are no commercial ...
... Trusted operating systems have security features built into the operating system. The National Computer Security Center’s Rainbow series Orange Book, Trusted Computer Standards Evaluation Criteria describes several levels of trust including C1, C2, B1, B2, and B3. Currently, there are no commercial ...
LECTURE 33 APPLICATION I/O INTERFACE
... writers (roll your own). Can implement “secret” calls which may not be documented in a users or programming manual ...
... writers (roll your own). Can implement “secret” calls which may not be documented in a users or programming manual ...
Network Security Policy: In the Work Place
... It includes a set of cryptographic tools to protect communications, encrypting each IP packet going between network systems. Overall, network security is a very broad topic. When applied to businesses and work places, it becomes slightly more specific. Common methods and techniques of applying netwo ...
... It includes a set of cryptographic tools to protect communications, encrypting each IP packet going between network systems. Overall, network security is a very broad topic. When applied to businesses and work places, it becomes slightly more specific. Common methods and techniques of applying netwo ...
Hacking, Security, and Information War
... break-ins are justified because they protect civilians against "big brother" government and corporations. The government and businesses as well, have lots of information about us than they should have. The hacker is merely keeping ...
... break-ins are justified because they protect civilians against "big brother" government and corporations. The government and businesses as well, have lots of information about us than they should have. The hacker is merely keeping ...
security
... • Web browser then checks the key for certification and the authority that certified it ...
... • Web browser then checks the key for certification and the authority that certified it ...
Computer Network Security Protocols and Standards
... – It provides an encrypted end-to-end data path between a client and a server regardless of platform or OS. – Secure and authenticated services are provided through data encryption, server authentication, message integrity, and client authentication for a TCP connection through HTTP, LDAP or POP3 ap ...
... – It provides an encrypted end-to-end data path between a client and a server regardless of platform or OS. – Secure and authenticated services are provided through data encryption, server authentication, message integrity, and client authentication for a TCP connection through HTTP, LDAP or POP3 ap ...
Slide 1 - IITK - Indian Institute of Technology Kanpur
... • Vulnerability scanner :A vulnerability scanner is a tool used to quickly check computers on a network for known weaknesses. These check to see which ports on a specified computer are "open" or available to access the computer, and sometimes will detect what program or service is listening on that ...
... • Vulnerability scanner :A vulnerability scanner is a tool used to quickly check computers on a network for known weaknesses. These check to see which ports on a specified computer are "open" or available to access the computer, and sometimes will detect what program or service is listening on that ...
Lec1
... you into something that the application programmers want? For any OS area (file systems, virtual memory, networking, CPU scheduling), you begin by asking two questions: – What’s the hardware interface? (the physical reality) – What’s the application interface? (the nicer abstraction) ...
... you into something that the application programmers want? For any OS area (file systems, virtual memory, networking, CPU scheduling), you begin by asking two questions: – What’s the hardware interface? (the physical reality) – What’s the application interface? (the nicer abstraction) ...
Unit OS2: Operating Systems Principles
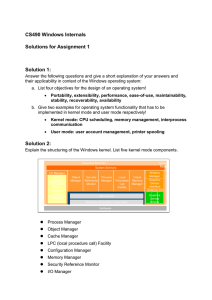
... Explain why Windows NT 4 move windows manager and graphics services from running in the context of the Windows Subsystem process to a set of callable services running in kernel mode. The primary reason for this shift was to improve overall system performance. Having a separate server process that co ...
... Explain why Windows NT 4 move windows manager and graphics services from running in the context of the Windows Subsystem process to a set of callable services running in kernel mode. The primary reason for this shift was to improve overall system performance. Having a separate server process that co ...
Introduction
... special files – standard input (fd=0), standard output (fd=1), standard error (fd=2). ...
... special files – standard input (fd=0), standard output (fd=1), standard error (fd=2). ...