Member services - Scottish Public Pensions Agency
... NEW IN 2012 SPPA LAUNCHING MEMBER ONLINE WEB SERVICES Diane Gladstone Philippa Brosnan Member Web Services Project Team Presentation By: ...
... NEW IN 2012 SPPA LAUNCHING MEMBER ONLINE WEB SERVICES Diane Gladstone Philippa Brosnan Member Web Services Project Team Presentation By: ...
group policy - University Of Worcester
... » e.g. change system date/time, update device drivers ...
... » e.g. change system date/time, update device drivers ...
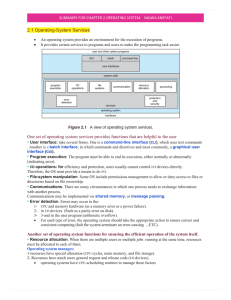
Overview of Operating Systems
... ❚ UNIX – limited by hardware functionality, the original UNIX operating system had limited structure. ❚ The UNIX OS consists of two separable parts: Ø Application programs Ø The kernel (everything below the system-call interface and above the physical hardware) ü Provides the file system, CPU s ...
... ❚ UNIX – limited by hardware functionality, the original UNIX operating system had limited structure. ❚ The UNIX OS consists of two separable parts: Ø Application programs Ø The kernel (everything below the system-call interface and above the physical hardware) ü Provides the file system, CPU s ...
History of Operating Systems
... Information is usually stored in the form of a file. OS responsibility for files are typically: • creation, deletion of files • provision of access to files ...
... Information is usually stored in the form of a file. OS responsibility for files are typically: • creation, deletion of files • provision of access to files ...
Huntsman Security updates trail-blazing cyber security analytics and
... Massive growth in interest around security analytics, threat management and automation has driven rapid evolution of Huntsman Security cyber risk solutions with new version released today. Sydney, May 31 2016. Huntsman Security (http://www.huntsmansecurity.com) today announced the latest release of ...
... Massive growth in interest around security analytics, threat management and automation has driven rapid evolution of Huntsman Security cyber risk solutions with new version released today. Sydney, May 31 2016. Huntsman Security (http://www.huntsmansecurity.com) today announced the latest release of ...
DIGITAL SYSTEM FOR TELECOMMUNICATIONS II (Verizon)
... CATALOGUE DESCRIPTION: In this course students will be working with hardware ...
... CATALOGUE DESCRIPTION: In this course students will be working with hardware ...
CS423/523
... User Account Control What does it do? UAC allows an administrator to enter credentials during a non-administrator's user session to perform occasional administrative tasks without having to switch users, log off, or use the Run as command UAC also can also require administrators to specifically app ...
... User Account Control What does it do? UAC allows an administrator to enter credentials during a non-administrator's user session to perform occasional administrative tasks without having to switch users, log off, or use the Run as command UAC also can also require administrators to specifically app ...
Syllabus/Course Outline for COSC 402 Computer
... Computer systems, hardware and basic operating systems software, as well as their features will be discussed. Processor, memory, input/output, storage, remote transmission memory, and channel management are included. In this course, topics and issues such as executive and diagnostic software, data-h ...
... Computer systems, hardware and basic operating systems software, as well as their features will be discussed. Processor, memory, input/output, storage, remote transmission memory, and channel management are included. In this course, topics and issues such as executive and diagnostic software, data-h ...
Chapter 13 Troubleshooting the Operating System
... • If it is a daemon that is crashing regularly try using other methods of starting it and running it. ...
... • If it is a daemon that is crashing regularly try using other methods of starting it and running it. ...
ITE-II-ch13
... • If it is a daemon that is crashing regularly try using other methods of starting it and running it. ...
... • If it is a daemon that is crashing regularly try using other methods of starting it and running it. ...
Booting and Shutting Down UNIX Flavored Operating Systems
... from the command line. Here are a few commands: – shutdown: Broadcasts a message to all users logged in prompting a system shut down. – halt: Performs essential duties required to bring the system down, waits for the filesystem writes to complete then halts the kernel. – reboot: Executes identical ...
... from the command line. Here are a few commands: – shutdown: Broadcasts a message to all users logged in prompting a system shut down. – halt: Performs essential duties required to bring the system down, waits for the filesystem writes to complete then halts the kernel. – reboot: Executes identical ...
Chapter 1 - Introduction to Operating Systems
... 2. Operating system – controls and coordinates the use of the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, video game ...
... 2. Operating system – controls and coordinates the use of the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, video game ...
chap-01mod
... Different administrative domains have conflicting policies for resource usage, management and security ...
... Different administrative domains have conflicting policies for resource usage, management and security ...
What is an Operating System?
... On-line communication between the user and the system is provided; when the operating system finishes the execution of one command, it seeks the next “control statement” from the user’s keyboard. On-line system must be available for users to access data and code. ...
... On-line communication between the user and the system is provided; when the operating system finishes the execution of one command, it seeks the next “control statement” from the user’s keyboard. On-line system must be available for users to access data and code. ...
LVRJ Case study
... actionable control panel for a single view of all user activity and security incidents across the Review-Journal LAN. About ConSentry Networks ConSentry Networks secures enterprise LANs with a purpose-built system that preserves data integrity, ensures network availability and supports regulatory co ...
... actionable control panel for a single view of all user activity and security incidents across the Review-Journal LAN. About ConSentry Networks ConSentry Networks secures enterprise LANs with a purpose-built system that preserves data integrity, ensures network availability and supports regulatory co ...
Summary for chapter 2 OPERATING SYSTEM nAJWA kNEFATI
... • File-system manipulation. Some OS include permissions management to allow or deny access to files or directories based on file ownership. • Communications. There are many circumstances in which one process needs to exchange information with another process. Communications may be implemented via sh ...
... • File-system manipulation. Some OS include permissions management to allow or deny access to files or directories based on file ownership. • Communications. There are many circumstances in which one process needs to exchange information with another process. Communications may be implemented via sh ...
Operating Systems
... • In a complex machine, having a part move more quickly just because system resources are available may be just as catastrophic as having it not move at all because the system was busy ...
... • In a complex machine, having a part move more quickly just because system resources are available may be just as catastrophic as having it not move at all because the system was busy ...
Wally Mead - ConfigMgr 2012 SP1 Slidedeck - November
... • For clients, securely save/restore user state and settings (locally or on a file server) ...
... • For clients, securely save/restore user state and settings (locally or on a file server) ...
Powerpoint template
... – Many web sites use Linux as the operating system – Even Steve Ballmer of Microsoft said Linux has 60% of the server market in 2008. – Tolerant of a range of hardware platforms without special configuration. ...
... – Many web sites use Linux as the operating system – Even Steve Ballmer of Microsoft said Linux has 60% of the server market in 2008. – Tolerant of a range of hardware platforms without special configuration. ...
PC Operating Systems in Review
... replacement for DOS, but was too resource- intensive to work on most PCs at the time of its release. ...
... replacement for DOS, but was too resource- intensive to work on most PCs at the time of its release. ...
yanc: Yet Another Network Controller References
... With the rise of software-defined networking, there has been a great deal of focus on the design of the centralized controller (both commercially and academically). This controller serves the role of an operating system for networks [2] which provides an interface to program the entire network. In t ...
... With the rise of software-defined networking, there has been a great deal of focus on the design of the centralized controller (both commercially and academically). This controller serves the role of an operating system for networks [2] which provides an interface to program the entire network. In t ...
File
... replacement for DOS, but was too resource- intensive to work on most PCs at the time of its release. ...
... replacement for DOS, but was too resource- intensive to work on most PCs at the time of its release. ...