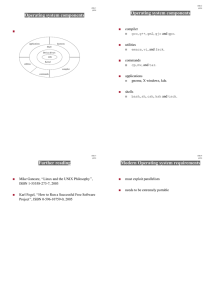
Operating system components Operating system
... started out as ‘‘for fun’’ to run bash and gcc on his ‘‘toy’’ operating system Linus started by utilising the file system code of Minix in Linux later on he found that good design principles led the way to portability for purity’s sake alone other people helped porting Linux to other ...
... started out as ‘‘for fun’’ to run bash and gcc on his ‘‘toy’’ operating system Linus started by utilising the file system code of Minix in Linux later on he found that good design principles led the way to portability for purity’s sake alone other people helped porting Linux to other ...
Remote Access Policy
... Computing) is a great client/server software package allowing remote network access to graphical desktops. With VNC, you can access your machine from everywhere provided that your machine is connected to the Internet. VNC is free (released under the GNU General Public License) and it's available on ...
... Computing) is a great client/server software package allowing remote network access to graphical desktops. With VNC, you can access your machine from everywhere provided that your machine is connected to the Internet. VNC is free (released under the GNU General Public License) and it's available on ...
1.1 Introduction
... Like a government, it performs no useful function by itself. It simply provides an environment within which other programs can do useful work. Operating systems can be explored from two viewpoints: the user and the system. ...
... Like a government, it performs no useful function by itself. It simply provides an environment within which other programs can do useful work. Operating systems can be explored from two viewpoints: the user and the system. ...
here
... This module develops the learner’s understanding of computer systems by introducing them to the theory associated with the study of operating systems, and providing them with the practical skills to perform effective system administration. As such, this is a module which is balanced between the theo ...
... This module develops the learner’s understanding of computer systems by introducing them to the theory associated with the study of operating systems, and providing them with the practical skills to perform effective system administration. As such, this is a module which is balanced between the theo ...
Chapter 4: Protection in a General
... Chapter 4: Protection in a General-Purpose Operating System This chapter discusses the services provided by a general-purpose operating system to facilitate data integrity and security. Although it is the case that these services were developed to support time-sharing (a mode of computing not much u ...
... Chapter 4: Protection in a General-Purpose Operating System This chapter discusses the services provided by a general-purpose operating system to facilitate data integrity and security. Although it is the case that these services were developed to support time-sharing (a mode of computing not much u ...
Lecture 15 - Department of Math and Computer Science
... Credentials. Each process must have an associated user ID and one or more group IDs that determine the process’s rights to access system resources and files Personality. Not traditionally found on UNIX systems, but under Linux each process has an associated personality identifier that can slight ...
... Credentials. Each process must have an associated user ID and one or more group IDs that determine the process’s rights to access system resources and files Personality. Not traditionally found on UNIX systems, but under Linux each process has an associated personality identifier that can slight ...
Operating System Services
... User identities (user IDs, security IDs) include name and associated number, one per user User ID then associated with all files, processes of that user to determine access control Group identifier (group ID) allows set of users to be defined and controls managed, then also associated with each proc ...
... User identities (user IDs, security IDs) include name and associated number, one per user User ID then associated with all files, processes of that user to determine access control Group identifier (group ID) allows set of users to be defined and controls managed, then also associated with each proc ...
Cybersecurity Chapter 3 Test Review
... Pete, the security administrator, wants to ensure that traffic to the corporate intranet is secure using HTTPS. He configures the firewall to deny traffic to port 80. Now users cannot connect to the intranet even through HTTPS. Which of the following is MOST likely causing the issue? The web server ...
... Pete, the security administrator, wants to ensure that traffic to the corporate intranet is secure using HTTPS. He configures the firewall to deny traffic to port 80. Now users cannot connect to the intranet even through HTTPS. Which of the following is MOST likely causing the issue? The web server ...
DCN-7-Network_Security
... Network Security •Physical Security: –Apart from the normal physical security such as guards, surveillance systems, •Many companies maintain backup copies of server contents at a remote location. •In case of a disaster, –The operations can be switched over in a matter of seconds to the backup locat ...
... Network Security •Physical Security: –Apart from the normal physical security such as guards, surveillance systems, •Many companies maintain backup copies of server contents at a remote location. •In case of a disaster, –The operations can be switched over in a matter of seconds to the backup locat ...
Computer Network Security Protocols and Standards
... something that is there in effect and performance but in reality not there – that is virtual. It is a physical abstraction of the company computing resources like storage, network servers, memory and others. For computing systems, it is a process in which software creates virtual machines (VMs) incl ...
... something that is there in effect and performance but in reality not there – that is virtual. It is a physical abstraction of the company computing resources like storage, network servers, memory and others. For computing systems, it is a process in which software creates virtual machines (VMs) incl ...
CS-3013 Week 0:- Introduction
... sharing: how are resources shared across users? naming: how are resources named (by users or programs)? security: how is the integrity of the OS and its resources ensured? protection: how is one user/program protected from another? performance: how do we make it all go fast? reliability: what happen ...
... sharing: how are resources shared across users? naming: how are resources named (by users or programs)? security: how is the integrity of the OS and its resources ensured? protection: how is one user/program protected from another? performance: how do we make it all go fast? reliability: what happen ...
The BaBar Online Detector Control System Update
... Records can get their input from device drivers • Interface to Hardware (mainly VME) ...
... Records can get their input from device drivers • Interface to Hardware (mainly VME) ...
(1) OS: Operating System
... allocation graph, Methods for handling deadlocks, preventions, avoidance, detection and recovery Protection –Goal domain of protection, access matrix. UNIT –IV:FILE SYSTEM Types of files in Unix - Structure of the file system - File System types - Parent & child relationship Directory handling and n ...
... allocation graph, Methods for handling deadlocks, preventions, avoidance, detection and recovery Protection –Goal domain of protection, access matrix. UNIT –IV:FILE SYSTEM Types of files in Unix - Structure of the file system - File System types - Parent & child relationship Directory handling and n ...
N4Less12
... replacement for DOS, but was too resource- intensive to work on most PCs at the time of its release. ...
... replacement for DOS, but was too resource- intensive to work on most PCs at the time of its release. ...
Module 2
... Access Controller Access-Control System Plus (TACACS+) are two protocols that provide centralized authentication, authorization, and Accounting management for computers to connect and use a network ...
... Access Controller Access-Control System Plus (TACACS+) are two protocols that provide centralized authentication, authorization, and Accounting management for computers to connect and use a network ...
pcs 105 advanced operating system
... Processes, The Critical Section Problem, Other Synchronization Problems, Language Mechanisms for Synchronization, Axiomatic Verification of Parallel Programs - Process Deadlocks Preliminaries, Models of Deadlocks, Resources, System State, Necessary and Sufficient conditions for a Deadlock, Systems w ...
... Processes, The Critical Section Problem, Other Synchronization Problems, Language Mechanisms for Synchronization, Axiomatic Verification of Parallel Programs - Process Deadlocks Preliminaries, Models of Deadlocks, Resources, System State, Necessary and Sufficient conditions for a Deadlock, Systems w ...
Top-Ten Web Security Vulnerabilities
... Security Techniques – Authorization and Access Control Limits what users can do, which resources they have access to, and what functions they are allowed to perform on the data. Authorization The act of checking to see if a user has the proper permission to access a particular file or perform a par ...
... Security Techniques – Authorization and Access Control Limits what users can do, which resources they have access to, and what functions they are allowed to perform on the data. Authorization The act of checking to see if a user has the proper permission to access a particular file or perform a par ...
FAST-OS BOF SC 04 - Department of Computer Science
... Develop a set of services to enhance the OS to improve its ability to support systems with very large numbers of processors – We will improve operating system awareness of the requirements of parallel applications. – We will enhance operating system support for parallel execution by providing coordi ...
... Develop a set of services to enhance the OS to improve its ability to support systems with very large numbers of processors – We will improve operating system awareness of the requirements of parallel applications. – We will enhance operating system support for parallel execution by providing coordi ...
Design of OSes
... – OS performs some system management & profiling – OS halts the processor and enter in low-power mode (notebooks) – OS computes some function (DEC’s VMS on VAX computed Pi) ...
... – OS performs some system management & profiling – OS halts the processor and enter in low-power mode (notebooks) – OS computes some function (DEC’s VMS on VAX computed Pi) ...
Chapter 8 Operating Systems and Utility Programs
... Red Hat provides a version of Linux called Red Hat Linux. The GNOME graphical user interface is shown in this example. ...
... Red Hat provides a version of Linux called Red Hat Linux. The GNOME graphical user interface is shown in this example. ...
Operating System
... merging adjacent disk read requests into a single request. – default: tells LILO which image to boot from by default, such as after the timeout period. This relates to a label of one of the images in the lilo.conf file. If not specified LILO will boot the first image in the file. – image: specifies ...
... merging adjacent disk read requests into a single request. – default: tells LILO which image to boot from by default, such as after the timeout period. This relates to a label of one of the images in the lilo.conf file. If not specified LILO will boot the first image in the file. – image: specifies ...
Guide to Operating System Security
... Endlessly replicates on the same computer, or sends itself to many other computers on a network Continues to create new files but does not infect existing files ...
... Endlessly replicates on the same computer, or sends itself to many other computers on a network Continues to create new files but does not infect existing files ...























