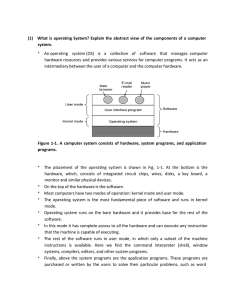
(1) What is operating System? Explain the abstract view of the
... Explain the features of Real Time Operating System. A real time operating system is used, when there are rigid (strict) time requirements on the operation of a processor or the flow of data. It is often used as a control device in a dedicated application. Systems that control scientific experiments, ...
... Explain the features of Real Time Operating System. A real time operating system is used, when there are rigid (strict) time requirements on the operation of a processor or the flow of data. It is often used as a control device in a dedicated application. Systems that control scientific experiments, ...
Benu: Operating System Increments for Embedded
... systems or useful components to reuse, one may start by selecting the operating system and appropriate development tools that will be used as a base. The operating system and development tools might be selected from the available commercial off the shelf tools (COTS), such as µC/OS-II [1], QNX [2], ...
... systems or useful components to reuse, one may start by selecting the operating system and appropriate development tools that will be used as a base. The operating system and development tools might be selected from the available commercial off the shelf tools (COTS), such as µC/OS-II [1], QNX [2], ...
Lecture notes - 南京大学计算机科学与技术系
... Allows a multiprocessor or multicomputer network resources to be integrated as a single system image Hide and manage hardware and software resources provides transparency support provide heterogeneity support control network in most effective way consists of low level commands + local op ...
... Allows a multiprocessor or multicomputer network resources to be integrated as a single system image Hide and manage hardware and software resources provides transparency support provide heterogeneity support control network in most effective way consists of low level commands + local op ...
Introduction
... Running user commands User types: ‘grep some_word file_name’ Shell parses the command, inserts the strings grep, some_word, file_name into argv and their number to argc Next, the shell uses fork() to create a process (same user ID) Now, it takes the executable name grep and the arguments, a ...
... Running user commands User types: ‘grep some_word file_name’ Shell parses the command, inserts the strings grep, some_word, file_name into argv and their number to argc Next, the shell uses fork() to create a process (same user ID) Now, it takes the executable name grep and the arguments, a ...
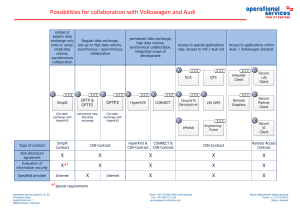
Possibilities for collaboration with Volkswagen
... · valid non-disclosure agreement · proof of an adequate level of information security ...
... · valid non-disclosure agreement · proof of an adequate level of information security ...
Voice Over IP and Security
... authorize users, calling plans and other basic telephone features (holding, transferring,etc.) ...
... authorize users, calling plans and other basic telephone features (holding, transferring,etc.) ...
Windows2000-Spr-2001-sect-2-group
... • Threads of lower priority are preempted so the higher priority threads can have access to the processor when they are ready • In the real time class, where all threads have a fixed priority that never changes, threads of equal priority are in a round-robin queue • In the variable priority class, a ...
... • Threads of lower priority are preempted so the higher priority threads can have access to the processor when they are ready • In the real time class, where all threads have a fixed priority that never changes, threads of equal priority are in a round-robin queue • In the variable priority class, a ...
Page PDF - Utah Valley University
... Fall, Spring, Summer * Prerequisite(s): IT 2700 and University Advanced Standing * Prerequisite(s) or Corequisite(s): INFO 3430 Provides perspective of key issues involved in IT activities across the organizational and technical security landscape. Examines management methodologies, staffing, and op ...
... Fall, Spring, Summer * Prerequisite(s): IT 2700 and University Advanced Standing * Prerequisite(s) or Corequisite(s): INFO 3430 Provides perspective of key issues involved in IT activities across the organizational and technical security landscape. Examines management methodologies, staffing, and op ...
Desktop Linux ready for prime time and on a screen near you
... Stability . Since Linux is based on the stable UNIX operating system, it inherits that stability and reliability. Our Linux servers have uptimes in the MONTHS. Linux is open-source, which means the source code is readily available to anyone who wants it. Since the source code available, thousands of ...
... Stability . Since Linux is based on the stable UNIX operating system, it inherits that stability and reliability. Our Linux servers have uptimes in the MONTHS. Linux is open-source, which means the source code is readily available to anyone who wants it. Since the source code available, thousands of ...
Unauthorized Access - Threats, Risk, and Control
... levels to ensure the confidentiality of information. It forbids the flow of higher security level information down to a lower security level. The Bell and La Padula (BLP) model is an example of this model. The BLP uses security levels to determine appropriate access rights based on the defined rules ...
... levels to ensure the confidentiality of information. It forbids the flow of higher security level information down to a lower security level. The Bell and La Padula (BLP) model is an example of this model. The BLP uses security levels to determine appropriate access rights based on the defined rules ...
PowerPoint
... using it as a building block for the rest of the system. Virtual memory support provided by the kernel and by user level servers. Kernel level support for light-weight threads. Support for closely and loosely coupled multi-processors and a variety of different commercially available workstatio ...
... using it as a building block for the rest of the system. Virtual memory support provided by the kernel and by user level servers. Kernel level support for light-weight threads. Support for closely and loosely coupled multi-processors and a variety of different commercially available workstatio ...
Operating systems
... The Boot Process • Step 1: The basic input/output system (BIOS) is activated • Step 2: A Power-on self-test ...
... The Boot Process • Step 1: The basic input/output system (BIOS) is activated • Step 2: A Power-on self-test ...
Discovering Computers 2006
... Operating System Functions What are other program management features of operating systems? multiprocessing Can support two or more processors running programs at same time ...
... Operating System Functions What are other program management features of operating systems? multiprocessing Can support two or more processors running programs at same time ...
EAP
... Advantages to Infrastructure Mode • Automatic use of Network Address Translation (NAT) firewall –blocks all outside port requests • Local reserved IP addresses only used by clients. Those IP addresses will not show up on the internet. • The DCHP server (gateway) that is built into this NAT firewall ...
... Advantages to Infrastructure Mode • Automatic use of Network Address Translation (NAT) firewall –blocks all outside port requests • Local reserved IP addresses only used by clients. Those IP addresses will not show up on the internet. • The DCHP server (gateway) that is built into this NAT firewall ...
lec03-concurrency
... • Most modern OS kernels – Internally concurrent because have to deal with concurrent requests by multiple users – But no protection needed within kernel ...
... • Most modern OS kernels – Internally concurrent because have to deal with concurrent requests by multiple users – But no protection needed within kernel ...
Evaluation and Assurance - NYU Polytechnic School of
... • Instead, systems are sometimes built from enclaves of workstations and network elements Within the enclave everything is at one level Commercial Off The Shelf (COTS) products (workstations, network elements) can be used C2 (Orange book) or lower EAL (common criteria) is OK Enclaves can be ...
... • Instead, systems are sometimes built from enclaves of workstations and network elements Within the enclave everything is at one level Commercial Off The Shelf (COTS) products (workstations, network elements) can be used C2 (Orange book) or lower EAL (common criteria) is OK Enclaves can be ...
Lesson 16
... Remember, computer refers to more than a desktop or laptop computer. These days, almost anything we turn on has some kind of computer. Not all products with computers have operating systems. Simple devices, such as microwaves, do not require operating systems. However, more and more electronic devic ...
... Remember, computer refers to more than a desktop or laptop computer. These days, almost anything we turn on has some kind of computer. Not all products with computers have operating systems. Simple devices, such as microwaves, do not require operating systems. However, more and more electronic devic ...
Security Tools: Superscan 3 Superscan is a program that scans a
... Security Tools: GFI LANguard Network Security Scanner GFI LANguard NSS, is a more versatile vulnerability scanner. This tool has the ability to scan Windows, Linux, and Macintosh operating systems as well as SQL servers and Cisco routers. NSS can scan for Missing patches, USB devices, open shares, ...
... Security Tools: GFI LANguard Network Security Scanner GFI LANguard NSS, is a more versatile vulnerability scanner. This tool has the ability to scan Windows, Linux, and Macintosh operating systems as well as SQL servers and Cisco routers. NSS can scan for Missing patches, USB devices, open shares, ...
The Multikernel: A new OS architecture for scalable
... • Mix of cores, caches, interconnect links.. – Increase scalability & correctness challenges for OS designers – No longer acceptable to tune a general-purpose OS design ...
... • Mix of cores, caches, interconnect links.. – Increase scalability & correctness challenges for OS designers – No longer acceptable to tune a general-purpose OS design ...
Higher National Unit specification: general information Unit title
... be made available as a central part of the course for revision, tutorials and formative assessment exercises. Candidates should be strongly encouraged to undertake further reading, and opportunities for individual or group research should be provided. The most important overall emphasis should be on ...
... be made available as a central part of the course for revision, tutorials and formative assessment exercises. Candidates should be strongly encouraged to undertake further reading, and opportunities for individual or group research should be provided. The most important overall emphasis should be on ...
Appendix C - Windows 2000
... of architecture is that interactions between modules can be kept simple. The remainder of this section describes these layers and subsystems. ...
... of architecture is that interactions between modules can be kept simple. The remainder of this section describes these layers and subsystems. ...