You Can`t Control People. Control What`s On Your Network.
... » Limited network access, such as Internet access only, until remediation is complete » Redirection to a Web server for user-appropriate remediation Management Capabilities Mirage NAC offers one-to-many management, enabling change management for software patches and policies across all Mirage appl ...
... » Limited network access, such as Internet access only, until remediation is complete » Redirection to a Web server for user-appropriate remediation Management Capabilities Mirage NAC offers one-to-many management, enabling change management for software patches and policies across all Mirage appl ...
Module 4: Processes
... to be fetched from memory, brought into the CPU, decoded, and executed Register settings – current values of working registers Stack – temporary area for program parameters, return addresses, stack frames (used for recursion) local variables (specific method) Data – global variables; other data; buf ...
... to be fetched from memory, brought into the CPU, decoded, and executed Register settings – current values of working registers Stack – temporary area for program parameters, return addresses, stack frames (used for recursion) local variables (specific method) Data – global variables; other data; buf ...
Discovering Computers 2006
... Operating System Functions What are other program management features of operating systems? multiprocessing Can support two or more processors running programs at same time ...
... Operating System Functions What are other program management features of operating systems? multiprocessing Can support two or more processors running programs at same time ...
Chap 01 - Introduction
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
1) Routine is not loaded until it is called. All routines are kept on disk
... 39) Virtual memory is __________. 1 An extremely large main memory 2 An extremely large secondary memory 3 An illusion of extremely large main memory 4 A type of memory used in super computers. ...
... 39) Virtual memory is __________. 1 An extremely large main memory 2 An extremely large secondary memory 3 An illusion of extremely large main memory 4 A type of memory used in super computers. ...
Computer Network and Infrastructure
... However if the time required for I/O operations is longer than the user operation (this is the true case) the processor will be idle for a long time. Multiprogramming which has more than one process in the memory solves this. Which means multiple user programs are now available for task switching. A ...
... However if the time required for I/O operations is longer than the user operation (this is the true case) the processor will be idle for a long time. Multiprogramming which has more than one process in the memory solves this. Which means multiple user programs are now available for task switching. A ...
Password Security
... choosing a sentence that incorporates something unique about the website or account, and then using the first letter of each word as your password. For example the sentence: "This is my August password for the Center for Internet Security website." would become "TimAp4tCfISw." Since a strong passwor ...
... choosing a sentence that incorporates something unique about the website or account, and then using the first letter of each word as your password. For example the sentence: "This is my August password for the Center for Internet Security website." would become "TimAp4tCfISw." Since a strong passwor ...
ch1
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
What is an Operating System?
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
What is an Operating System?
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
Our Digital World - Computer Information Systems
... • How will smaller computers change operating systems? • How might operating systems be different in 2020? Spotlight on the Future ...
... • How will smaller computers change operating systems? • How might operating systems be different in 2020? Spotlight on the Future ...
Chapter 8
... they are accessed Structure of Management Information (SMI) Rules specifying the format used to define objects managed on the network that the SNMP protocol accesses SNMP Protocol Defines format of messages exchanged by management systems and agents. Specifies the Get, GetNext, Set, and Tr ...
... they are accessed Structure of Management Information (SMI) Rules specifying the format used to define objects managed on the network that the SNMP protocol accesses SNMP Protocol Defines format of messages exchanged by management systems and agents. Specifies the Get, GetNext, Set, and Tr ...
dasan.sejong.ac.kr
... proved to be one of the most difficult aspects of systems programming. The ad hoc techniques used by programmers of early multiprogramming and real-time systems were always vulnerable to subtle programming errors whose effects could be observed only when certain relatively rare sequences of actions ...
... proved to be one of the most difficult aspects of systems programming. The ad hoc techniques used by programmers of early multiprogramming and real-time systems were always vulnerable to subtle programming errors whose effects could be observed only when certain relatively rare sequences of actions ...
Course Form - Bluegrass Community and Technical College
... 17. Proposed Course Description (Course description as it will appear in the catalog.): Provides a conceptual and practical view of client operating systems and the hardware systems required to run them. Covers computer hardware components, operating system interfaces and management tools, periphera ...
... 17. Proposed Course Description (Course description as it will appear in the catalog.): Provides a conceptual and practical view of client operating systems and the hardware systems required to run them. Covers computer hardware components, operating system interfaces and management tools, periphera ...
Linux+ Guide to Linux Certification Chapter One Introduction to Linux
... Firewalls and Proxy Services • Firewalls protect companies from outside intruders on the Internet • Linux has firewall support directly built into the kernel • A proxy service requests Internet resources such as Web sites and FTP sites on behalf of the computer inside the company ...
... Firewalls and Proxy Services • Firewalls protect companies from outside intruders on the Internet • Linux has firewall support directly built into the kernel • A proxy service requests Internet resources such as Web sites and FTP sites on behalf of the computer inside the company ...
What is an Operating System? ¯ Three views of an operating system
... Application View: what services does it provide? System View: what problems does it solve? Implementation View: how is it built? ...
... Application View: what services does it provide? System View: what problems does it solve? Implementation View: how is it built? ...
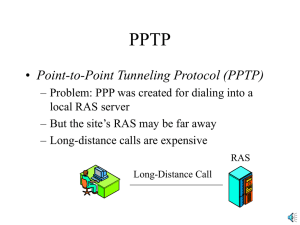
PPTP
... – Problem: PPP was created for dialing into a local RAS server – But the site’s RAS may be far away – Long-distance calls are expensive RAS Long-Distance Call ...
... – Problem: PPP was created for dialing into a local RAS server – But the site’s RAS may be far away – Long-distance calls are expensive RAS Long-Distance Call ...
Document
... How is free space managed? Free space is unused clusters. Clusters can come in different sizes. How does sector size affect the free space available when the disk is in use? What is a linked list of clusters? What are FAT, FAT32 and NTFS file systems? Short Course 2003 ...
... How is free space managed? Free space is unused clusters. Clusters can come in different sizes. How does sector size affect the free space available when the disk is in use? What is a linked list of clusters? What are FAT, FAT32 and NTFS file systems? Short Course 2003 ...
Threat Briefing - (AFCEA) Ottawa Chapter
... As systems and network are moving towards “one” common infrastructure: video, phones, data etc all riding on one common network, it requires more and different styles of security to protect the system while providing a quality level of user expectation. This session discusses IP convergence from thi ...
... As systems and network are moving towards “one” common infrastructure: video, phones, data etc all riding on one common network, it requires more and different styles of security to protect the system while providing a quality level of user expectation. This session discusses IP convergence from thi ...
Module 7: Process Synchronization
... Semaphore mutex initialized to the value 1 Semaphore full initialized to the value 0 Semaphore empty initialized to the value N. ...
... Semaphore mutex initialized to the value 1 Semaphore full initialized to the value 0 Semaphore empty initialized to the value N. ...
L4_L6_System_Structu..
... and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code. ...
... and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code. ...
Hotspot Shield Baixaki
... Hotspot Shield Baixaki - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while b ...
... Hotspot Shield Baixaki - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while b ...
Document
... Make sure your software and devices are compatible; Recommended that you use Windows 7 Upgrade advisor – Can download this program. It scans your computer to see what software (and drivers for hardware) are on your computer and whether compatible with Win 7. – Then if software not compatible, you ne ...
... Make sure your software and devices are compatible; Recommended that you use Windows 7 Upgrade advisor – Can download this program. It scans your computer to see what software (and drivers for hardware) are on your computer and whether compatible with Win 7. – Then if software not compatible, you ne ...
Information Security Office
... • A device capable of locating itself on a map • Software that will log data from the second when a network is detected by the first. • You then move these devices from place to place, letting them do their job. • Over time, you build up a database comprised of the network name, signal strength, loc ...
... • A device capable of locating itself on a map • Software that will log data from the second when a network is detected by the first. • You then move these devices from place to place, letting them do their job. • Over time, you build up a database comprised of the network name, signal strength, loc ...