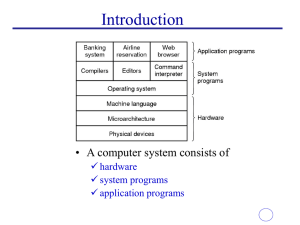
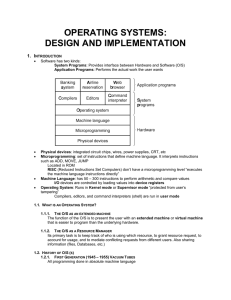
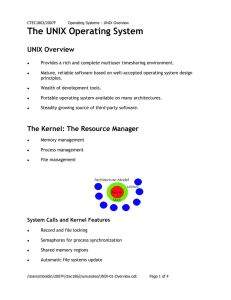
application programs
... some of the details of the underlying hardware for such I/O. All the user sees is that the I/O has been performed, without those details. Communications There are instances where processes need to communicate with each other to exchange information. It may be between processes running on the same ...
... some of the details of the underlying hardware for such I/O. All the user sees is that the I/O has been performed, without those details. Communications There are instances where processes need to communicate with each other to exchange information. It may be between processes running on the same ...
An Introduction to Operating Systems
... OS provides an environment where the user can conveniently run programs. The user does not have to worry about memory allocation or CPU scheduling. ¾ I/O Operations Each program requires input and produces output. The OS hides some of the details of the underlying hardware for such I/O. All the user ...
... OS provides an environment where the user can conveniently run programs. The user does not have to worry about memory allocation or CPU scheduling. ¾ I/O Operations Each program requires input and produces output. The OS hides some of the details of the underlying hardware for such I/O. All the user ...
Traditional UNIX kernels
... • man provides online documentation on nearly every standard command and configuration file. • Optional Syntax: man -k keyword • man man for more details ...
... • man provides online documentation on nearly every standard command and configuration file. • Optional Syntax: man -k keyword • man man for more details ...
OPERATING SYSTEMS:
... 1. Everything is a file (a sequence of bytes; record = byte) 2. Directories: Multilevel (implemented as files). Contain pairs: filename, i-node address) 3. Directory commands: chdir “cd”, mkdir, rmdir, pwd. 4. File commands: rm, mv, cp, cat, ls, 5. Several links to a file shared file. 6. Protectio ...
... 1. Everything is a file (a sequence of bytes; record = byte) 2. Directories: Multilevel (implemented as files). Contain pairs: filename, i-node address) 3. Directory commands: chdir “cd”, mkdir, rmdir, pwd. 4. File commands: rm, mv, cp, cat, ls, 5. Several links to a file shared file. 6. Protectio ...
The UNIX Operating System - Niagara College Technology
... Each UNIX command can get its input from any data source and send its output to any data destination. ...
... Each UNIX command can get its input from any data source and send its output to any data destination. ...
(1) OS: Operating System
... File Attributes: Structure of the inode - Brief discussion on partitions and file systems - Analyzing the ls-l output - File type and permissions (chmod) - Significance of directory permissions - Hard and soft Links (ln and ln-s). Concept of ownership - The/etc/passwd and /etc/group files - Changing ...
... File Attributes: Structure of the inode - Brief discussion on partitions and file systems - Analyzing the ls-l output - File type and permissions (chmod) - Significance of directory permissions - Hard and soft Links (ln and ln-s). Concept of ownership - The/etc/passwd and /etc/group files - Changing ...