Linux+ Guide to Linux Certification
... of an OS that provides a user-friendly interface System services: Applications that handle system-related tasks ◦ Printing ◦ Scheduling programs ◦ Network access ...
... of an OS that provides a user-friendly interface System services: Applications that handle system-related tasks ◦ Printing ◦ Scheduling programs ◦ Network access ...
LINUX System (English
... CPU scheduling : batch vs time-sharing Memory allocation : determine what is in memory when? Virtual memory : a technique that gives an application program the impression that it has large contiguous working memory, while in fact it is physically fragmented and may even overflow on to disk storage. ...
... CPU scheduling : batch vs time-sharing Memory allocation : determine what is in memory when? Virtual memory : a technique that gives an application program the impression that it has large contiguous working memory, while in fact it is physically fragmented and may even overflow on to disk storage. ...
File System - QES Main Website
... • But we need to start learning how computer scientists look at file systems • And that includes some new terms for ...
... • But we need to start learning how computer scientists look at file systems • And that includes some new terms for ...
Book cover slide
... bits to store a file’s address location. (p. 176) NT file system (NTFS) A file storage system used by the ...
... bits to store a file’s address location. (p. 176) NT file system (NTFS) A file storage system used by the ...
Introduction to UNIX System
... information. In fact there is several different types of file: 1)Ordinary files; 2)Directories; 3)Special files; ...
... information. In fact there is several different types of file: 1)Ordinary files; 2)Directories; 3)Special files; ...
The Linux System
... recovered to this directory. Such damages are almost always due to incorrect shutdown. ...
... recovered to this directory. Such damages are almost always due to incorrect shutdown. ...
LECT03
... the OS rotates its various jobs in and out of execution via time-sharing o Each job gets a predetermined “time slice” o At end of time slice current job is set aside and a new one starts o By rapidly shuffling jobs, illusion of several jobs executing simultaneously is created ...
... the OS rotates its various jobs in and out of execution via time-sharing o Each job gets a predetermined “time slice” o At end of time slice current job is set aside and a new one starts o By rapidly shuffling jobs, illusion of several jobs executing simultaneously is created ...
Answers
... Ken Thompson – Inventor of UNIX, contributed to C language. (Also inventor of B language) 2. What is POSIX? Portable Operating System Interface for Computing Environments Same system call interface standardized among UNIX-like operating systems ...
... Ken Thompson – Inventor of UNIX, contributed to C language. (Also inventor of B language) 2. What is POSIX? Portable Operating System Interface for Computing Environments Same system call interface standardized among UNIX-like operating systems ...
Win32 Programming
... OS needs to schedule processes and threads Create and delete processes Suspend and resume processes Ideally, allow for process synchronization and process communication ...
... OS needs to schedule processes and threads Create and delete processes Suspend and resume processes Ideally, allow for process synchronization and process communication ...
virtual machine
... jobs running concurrently, resources must be allocated to each of them – Accounting - To keep track of which users use how much and what kinds of computer resources – Protection and security - The owners of information stored in a multiuser or networked computer system may want to control use of tha ...
... jobs running concurrently, resources must be allocated to each of them – Accounting - To keep track of which users use how much and what kinds of computer resources – Protection and security - The owners of information stored in a multiuser or networked computer system may want to control use of tha ...
Evolution of Operating System
... o without time slicing, a computer spends most of its time waiting for peripheral devices or users o A collection of tasks can be completed in less time with time-sharing than when completed sequentially ...
... o without time slicing, a computer spends most of its time waiting for peripheral devices or users o A collection of tasks can be completed in less time with time-sharing than when completed sequentially ...
Syllabus - Marwadi University
... Write a shell script to display the digits which are in odd position in a given 5 digit number in Unix / Linux / Ubuntu Write a shell script to read n numbers as command arguments and sort them in descending/ascending order. Write a shell script to check entered string is palindrome or not. Write an ...
... Write a shell script to display the digits which are in odd position in a given 5 digit number in Unix / Linux / Ubuntu Write a shell script to read n numbers as command arguments and sort them in descending/ascending order. Write a shell script to check entered string is palindrome or not. Write an ...
Course number and name CSC 345 – Operating Systems Credits
... An introduction to operating systems concepts. Topics include processor management, storage management, device management, performance, security, and case studies of common operating systems. Prerequisites or co-requisites CSC 222 Indicate whether a required, elective, or selected elective (as per T ...
... An introduction to operating systems concepts. Topics include processor management, storage management, device management, performance, security, and case studies of common operating systems. Prerequisites or co-requisites CSC 222 Indicate whether a required, elective, or selected elective (as per T ...
Document
... This course involves study of concepts and components of general purpose operating systems. These include the study of processes and process synchronization, multithreaded applications, deadlocks, memory management, and file systems. UNIX and Windows NT are general purpose operating systems used as ...
... This course involves study of concepts and components of general purpose operating systems. These include the study of processes and process synchronization, multithreaded applications, deadlocks, memory management, and file systems. UNIX and Windows NT are general purpose operating systems used as ...
Detecting drive-by-downloads using human
... Wrote a program that takes the file system data from ProcMon and user action data from tlogger and flags any ‘suspicious’ downloads ...
... Wrote a program that takes the file system data from ProcMon and user action data from tlogger and flags any ‘suspicious’ downloads ...
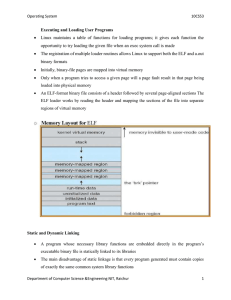
Operating System 10CS53 Executing and Loading User Programs
... An ELF-format binary file consists of a header followed by several page-aligned sections The ELF loader works by reading the header and mapping the sections of the file into separate regions of virtual memory ...
... An ELF-format binary file consists of a header followed by several page-aligned sections The ELF loader works by reading the header and mapping the sections of the file into separate regions of virtual memory ...
Answers
... Ken Thompson – Inventor of UNIX, contributed to C language. (Also inventor of B language) 2. What is POSIX? Portable Operating System Interface for Computing Environments Same system call interface standardized among UNIX-like operating systems ...
... Ken Thompson – Inventor of UNIX, contributed to C language. (Also inventor of B language) 2. What is POSIX? Portable Operating System Interface for Computing Environments Same system call interface standardized among UNIX-like operating systems ...
Operating Systems
... • https://en.wikipedia.org/wiki/Usage_share_of _operating_systems#/media/File:Operatingsys tem_market_share.svg ...
... • https://en.wikipedia.org/wiki/Usage_share_of _operating_systems#/media/File:Operatingsys tem_market_share.svg ...