* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Mohammad Husain
Process management (computing) wikipedia , lookup
Library (computing) wikipedia , lookup
Berkeley Software Distribution wikipedia , lookup
Security-focused operating system wikipedia , lookup
Windows NT startup process wikipedia , lookup
MTS system architecture wikipedia , lookup
Commodore DOS wikipedia , lookup
Plan 9 from Bell Labs wikipedia , lookup
Spring (operating system) wikipedia , lookup
Burroughs MCP wikipedia , lookup
File locking wikipedia , lookup
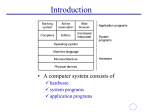
UNIX SECURITY and COMPUTER FORINSICS PRESENTED TO DR.LOA’I AL TAWALBEH New York Institute of Technology- Amman’s campus-2007 MOHAMMED HUSSAIN An operating system The OS is a program that acts as an intermediary between the user (application programs) and the hardware resources OS interacts with hardware and manages programs. Programs not expected to know which hardware they will run on. Thus they can’t manage their self OS provides a safe environment for programs to run. What is an Operating System? Unix architecture kernel Program always resides in memory. Has direct access to the hardware. Manages processes, memory, and performs all housekeeping. Only one copy shared by all users. Shell A program or command invoked only when the user logs in. so it’s called function from the kernel by command or graphical interface. At least one shell is invoked by every user, so a system may have several different shells running simultaneously. Interface between the user and the UNIX Architecture User Shell which executes the binary: -cp, mv, grep, tar, who, ps Kernel Hardware Interacting with the Shell The shell prints a prompt and waits for you to type in a command. The shell can deal with a couple of types of commands: – shell internals - commands that the shell handles directly. – External programs - the shell runs a program for you. Types of commands External program on disk which could be: – a binary executable (written in C, C++). – a script file (like a shell or perl script). Internal command of the shell which could be – a builtin (like cd, pwd, etc.) – an alias defined by the user that invokes the disk or internal version in a specific Why security? – Availability – Confidentiality – Integrity (system files) We need to identify the capabilities that UNIX OS handled to perform the levels of security at the low and high level of operating system. files and directories and the permission are the main compoundant for such a system Ordinary step in any secure OS PROPLEM – Secure the OS from un wanted users – And to secure the internal processes from each other SOLUTION – Define specific domain that each user/process can access Domain implementation Two domain groups – User – Superuser (can do everything, UID=0) User domain group – Domain = user-id (UID) – Domain switch accomplished via file system. Each file has associated with it a domain bit (setuid bit = SUID bit). When file is executed and setuid = on, then effective user-id is set to owner of the file being executed. When execution completes user-id is reset (exit() for child process ). Basic Unix Security Model User authenticated on logon – User ID associated with process – Default Group ID associated with process – Default Process listed in passwd file Groups defined in /etc/groups – Set of users listed with each group definition – User can be member of multiple groups Users and permissions Three types of users – Root super users – Privileged users – Another users We assign access permissions to such files and directories ACL Unix Access Control Three permission octets associated with each file and directory – Owner, group, and other – Read, write, execute For each file/directory – Can specify RWX permissions for one owner, one group, and one other Other Bits Set UID and Set GUID bits – When set, the process created by executing file takes on user ID or group ID associated with file Secure shell (SSH) – Accessing remotely securely. Sticky bit – On directories, prevents anyone but owner of file removing file in directory – Sys daemon (log files access) Directories Under UNIX directories are special (OS writable only) files. The directory file is an unsorted linked list of filenames to file-inode (attributes and location of file on hard disk) Directory size will always increase to be large enough to hold all the file entries. If the number of files latter shrinks the directory size WILL NOT! > ls -l foo -rw-rw---1 hollingd grads 13 Jan 10 23:05 foo permissions size owner name group time Files Regular Files – binary GIF, JPEG, Executable etc. – text scripts, program source code, documentation Files (cont.) Directory – Can contain ANY kind of files . (Dot) The special name for the current directory. .. (Dot) (Dot) The special name for the directory above the current directory. Device File – Allows programs to communicate with hardware. – Kernel modules handle device management. File Time Attributes Time Attributes: – when the file was last changed ls l – when the file was created* ls lc – when the file was last read (accessed) ls ul *actually it’s the time the file status in the directory last changed (e.g. file renamed). File permissions File type - : plain file d : directory c : character device (tty, printer) b : block device (disk, CD-ROM) l : symbolic link s : socket =, p : FIFO Access granted to others -rwxr--r-Access granted to owner r : read / w : write / x : execute Access granted to group member File Protection Given the following output from ls –l -rwxr-xr-x jason research ... test.exe ----rwxr–- jason research ... example.exe jason has full access to test.exe jason has no access to example.exe even if he belongs to the research group Any member of the research group (except jason) has full access to example.exe Unix Accounts To access a Unix system you need to have an account. Unix account includes: – username and password – userid and groupid – home directory – shell Users accounts 1-User name: a username is (typically) a sequence of alphanumeric characters of length no more than 8. 2-Password: is a secret string that only the user knows, not less that 8 characters. but userID: is a number of 16 bit integer that identifies a user account, and the user don’t know this number but it used to secure the shell. Users and Ownership: /etc/passwd Every File is owned by one of the system’s users – identity is represented by the user-id (UID) Password file assoicate UID with system users. gates:x:65:20:B. Gates:/home/gates:/bin/ksh command interpreter home directory “real” name group ID user ID [encrypted password] login name SUID/SGID/sticky bits SUID (set uid) – Processes are granted access to system resources based on user who owns the file. SGID (set gid) – (For file) Same with SUID except group is affected. – (For directory) Files created in that directory will have their group set to the directory's group. sticky bit – If set on a directory, then a user may only delete files that he owns or for which he has explicit write permission granted, even when he has write access to the directory. (e.g. /tmp ) Advanced: Access Control Lists The permissions defined by ACLs are a superset of the permissions specified by the file permission bits. The permissions defined for the file owner correspond to the permissions of the ACL_USER_OBJ entry. The permissions defined for the file group correspond to the permissions of the ACL_GROUP_OBJ entry, if the ACL has no ACL_MASK entry. If the ACL has an ACL_MASK entry, then the permissions defined for the file group correspond to the permissions of the ACL_MASK entry. The permissions defined for the other class correspond to the permissions of the ACL_OTHER_OBJ entry. Modification of the file permission bits results in the modification of the permissions in the associated ACL entries. Modification of the permissions in the ACL entries results in the modification of the file permission bits. Example: user::rwuser:lisa:rwgroup::r-group:toolies:rwmask::r-other::r-- Log files Log files are normally kept in /var/log Read them Syslog logs the system and what is happening on it Logcheck is a handy utility which checks the contents of logs and mails anything unusual http://www.psionic.com/abacus/logcheck/ Advanced: TCP/IP Firewalls UNIX and Forensics Privacy Through Media Mutilation or or or degausser forensically-secure file deletion software (but make sure it works!) Basic enabler: Data is very hard to kill Digital evidences are every were in the intended area of work. It’s in side out side the used space, or impeded into other strings. Or even on the cell phones Temp files, print spools, Zipped files, windows registry. But the anti-forensics can play an negative role in the investigation process. Hiding Data in Slack Space w/ bmap: File carving won’t help! Dear Mom, Dropp ed the hamster. D idn’t mean to kill He rbie! pa To Whom It May C oncern: … Best, Fred ssword is frid #include <stdio.h> void zapQ(void); ay #include <io.h> bmap: tools for creating a simple filesystem in slack space 1 Lsof version 4.63 Vic Abell ftp://vic.cc.purdue.edu/pub/tools/unix/ls of FUNCTIONS List open files – regular files – directories – device files – executing text file – library (for dynamic load libraries) – network file (socket, NFS file) – stream What Has a Process Opened? % lsof -p 78957 COMMAND PID USER FD dc 78957 bishop cwd /usr/home/bishop dc 78957 bishop rtd dc 78957 bishop txt dc 78957 bishop txt /usr/libexec/ld-elf.so.1 dc 78957 bishop txt /usr/lib/libm.so.2 dc 78957 bishop txt /usr/lib/libc.so.4 dc 78957 bishop 0u dc 78957 bishop 1u dc 78957 bishop 2u TYPE DEVICE SIZE/OFF VDIR 3,131077 2560 VDIR 3,131072 VREG 3,131077 VREG 3,131077 NODE NAME 8482 512 2 / 27452 7953 /usr/bin/dc 71976 992435 VREG 3,131077 116092 286210 VREG 3,131077 531444 287065 VCHR VCHR VCHR You can also use –c cmdbegin 5,2 5,2 5,2 0t735 0t735 0t735 8176 /dev/ttyp2 8176 /dev/ttyp2 8176 /dev/ttyp2 What Has a User Opened? # lsof +M -u daemon COMMAND PID USER portmap 84 daemon portmap 84 daemon portmap 84 daemon portmap 84 daemon elf.so.1 portmap 84 daemon portmap 84 daemon portmap 84 daemon portmap 84 daemon portmap 84 daemon portmap 84 daemon portmap 84 daemon (LISTEN) FD cwd rtd txt txt TYPE VDIR VDIR VREG VREG DEVICE SIZE/OFF NODE 3,131072 512 2 3,131072 512 2 3,131077 11088 64023 3,131077 71976 992435 txt txt 0u 1u 2u 3u 4u VREG 3,131077 VREG 3,131077 VCHR 2,2 VCHR 2,2 VCHR 2,2 IPv4 0xc7c6dc00 IPv4 0xc7c9ed80 NAME / / /usr/sbin/portmap /usr/libexec/ld- 24776 287069 /usr/lib/libwrap.so.3 531444 287065 /usr/lib/libc.so.4 0t0 7828 /dev/null 0t0 7828 /dev/null 0t0 7828 /dev/null 0t0 UDP *:sunrpc[portmapper] 0t0 TCP *:sunrpc[portmapper] portmapper registration name/number (+M gives this) 2 NMAP Version 3.00 by [email protected] http://www.insecure.org/nmap/ TO To scan hosts looking for open ports – – – – – – – – – TCP connect TYP SYN (a.k.a. half-open) TCP FIN (a.k.a. stealth) TCP SYN/FIN using IP fragments TCP ftp proxy (a.k.a. bounce attack) UCP raw ICMP port unreachable RPC scan ACK/WIN scan Ping scan 2 Sleuthkit Linux toolkit for forensics written by Brian Carrier http://www.sleuthkit.org/ Command line tools for forensic analysis under UNIX Graphical interface: Autopsy Forensic Browser – – – – Timestamps are often crucial in forensics analysis Determining who was using a system Determining if a system has been compromised Determining when files were downloaded, modified, organized – Establish whether a person could have actually committed a computer crime – Establish validity of alibis – Sleuthkit MAC tools “light up the filesystem” – Idea: – Create a timeline that begins with the date of creation for the first file of interest… – …traces all subsequent file access, modification and creation dates… – Good news: Deleting a file counts as a “modification” and often the deletion dates of files can be retrieved Popular Commercial Unix versions Solaris (Sun Microsystems) MacOS X (Apple Computer) AIX (IBM) Windows vs. Unix Many beginner users find Windows easer to use than other operating systems Linux has been primary used by advanced computer users – programmers and developers One fundamental difference between the two systems is the fact that Linux is "open source". Linux requires 386 architecture to run. Thus, it is compatible with any improved architecture such as 486, Pentium, Pentium Pro, etc There are drivers available for much many types of hardware devices Linux program installation seems to be easier since it only requires a restart when hardware device has been changed Security UNIX seems to be more prepared for protecting itself because of the beginning developments of Linux, UNIX, and FreeBSD which were aimed at top notch security UNIX allows does not create registry keys in a way Windows does allowing a user to browse installed components registry keys, which contain important information UNIX is more virus proof since viruses – malicious programs either cannot be run automatically on the Linux machine, or simply are not capable of being executed on a 386 architecture Windows is often known for a large amount of loop holes References http://www.faqs.org/rfcs/rfc2350.html, http://www.securityfocus.com/infocus/1769 http://sleuthkit.sourceforge.net/informer/sleuthkit-informer-11.html http://www.cs.uno.edu/~golden/teach.html CERT (Computer Emergency Response Team) – http://www.cert.org/ SysAdmin, Audit, Network, Security (SANS) Institute – http://www.sans.org/ Security Tracker – http://www.securitytracker.com/