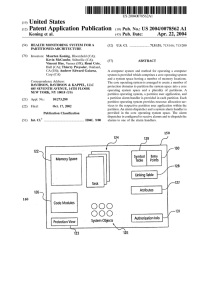
Slide 1
... copy frame pointer into stack pointer - stack top now contains the saved frame pointer pop stack into frame pointer (restore), leaving the return program pointer on top of the stack the RET instruction pops the stack top into the program counter register (EIP), causing the CPU to execute from the "r ...
... copy frame pointer into stack pointer - stack top now contains the saved frame pointer pop stack into frame pointer (restore), leaving the return program pointer on top of the stack the RET instruction pops the stack top into the program counter register (EIP), causing the CPU to execute from the "r ...
Slide 1
... copy frame pointer into stack pointer - stack top now contains the saved frame pointer pop stack into frame pointer (restore), leaving the return program pointer on top of the stack the RET instruction pops the stack top into the program counter register (EIP), causing the CPU to execute from the "r ...
... copy frame pointer into stack pointer - stack top now contains the saved frame pointer pop stack into frame pointer (restore), leaving the return program pointer on top of the stack the RET instruction pops the stack top into the program counter register (EIP), causing the CPU to execute from the "r ...
Operating Systems
... copy frame pointer into stack pointer - stack top now contains the saved frame pointer pop stack into frame pointer (restore), leaving the return program pointer on top of the stack the RET instruction pops the stack top into the program counter register (EIP), causing the CPU to execute from the "r ...
... copy frame pointer into stack pointer - stack top now contains the saved frame pointer pop stack into frame pointer (restore), leaving the return program pointer on top of the stack the RET instruction pops the stack top into the program counter register (EIP), causing the CPU to execute from the "r ...
Exploring IBM iSeries
... nology-led business revolution. The early phase of that e-business revolution was characterized by simple strategies such as publishing product information to the Internet and the first simple web-based transactions. The second, integrating phase of e-business adoption was marked by strategies to l ...
... nology-led business revolution. The early phase of that e-business revolution was characterized by simple strategies such as publishing product information to the Internet and the first simple web-based transactions. The second, integrating phase of e-business adoption was marked by strategies to l ...
IBM AIX to Oracle Solaris Technology Mapping Guide
... which environment presents the best opportunity for optimizing infrastructure today without limiting how systems can be used to address priorities in the future. Since both AIX and Oracle Solaris are based on UNIX System V, the transition to Oracle servers running Oracle Solaris 11 is not difficult. ...
... which environment presents the best opportunity for optimizing infrastructure today without limiting how systems can be used to address priorities in the future. Since both AIX and Oracle Solaris are based on UNIX System V, the transition to Oracle servers running Oracle Solaris 11 is not difficult. ...
IBM Power Systems HMC Implementation and Usage Guide Front cover
... International Technical Support Organization IBM Power Systems HMC Implementation and Usage Guide April 2013 ...
... International Technical Support Organization IBM Power Systems HMC Implementation and Usage Guide April 2013 ...
OpenAFS Quick Start Guide for UNIX
... Related Documents The OpenAFS documentation set also includes the following documents. Large portions of them are as released to the community by IBM, and are not directly applicable to current releases of OpenAFS. This document uses the legacy "Transarc" paths (/usr/ afs, /usr/vice, etc.), which do ...
... Related Documents The OpenAFS documentation set also includes the following documents. Large portions of them are as released to the community by IBM, and are not directly applicable to current releases of OpenAFS. This document uses the legacy "Transarc" paths (/usr/ afs, /usr/vice, etc.), which do ...
Secure Virtual Architecture: Security for Commodity Software Systems
... I thank my committee members Madhusudan Parthasarathy, Sam King, and Greg Morrisett for their interest in and feedback on my research work. Their suggestions have made this work better. I thank my collaborators and co-authors, including Nathan Dautenhahn, Nicolas Geoffray, Dinakar Dhurjati, Brent Mon ...
... I thank my committee members Madhusudan Parthasarathy, Sam King, and Greg Morrisett for their interest in and feedback on my research work. Their suggestions have made this work better. I thank my collaborators and co-authors, including Nathan Dautenhahn, Nicolas Geoffray, Dinakar Dhurjati, Brent Mon ...
JES2 Introduction
... JES2 initialization statements give the system programmer a single point of control to define an installation's policies regarding the degree of control users have over their jobs. For example, consider the confusion an installation would experience if users were allowed to define their own job clas ...
... JES2 initialization statements give the system programmer a single point of control to define an installation's policies regarding the degree of control users have over their jobs. For example, consider the confusion an installation would experience if users were allowed to define their own job clas ...
INF1060: Introduction to Operating Systems and Data Communication
... Presents user with a virtual machine, easier to use It is a resource manager (bottom-up view) Each program gets time with the resource Each program gets space on the resource ...
... Presents user with a virtual machine, easier to use It is a resource manager (bottom-up view) Each program gets time with the resource Each program gets space on the resource ...
Partitioning Implementations for IBM E p5 Servers
... 3.4.7 Processor resources in a shared partition environment . . . . . . . . . . 81 Chapter 4. Virtualized resource management . . . . . . . . . . . . . . . . . . . . . . 83 4.1 Micro-Partitioning technology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84 4.1.1 Shared processor ...
... 3.4.7 Processor resources in a shared partition environment . . . . . . . . . . 81 Chapter 4. Virtualized resource management . . . . . . . . . . . . . . . . . . . . . . 83 4.1 Micro-Partitioning technology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84 4.1.1 Shared processor ...
a. Real Time Operating Systems Notes
... few variables. Also, this is the only way that a thread can share variables or data structures with an ISR. In all cases, you should keep interrupts disabled for as little time as possible. If you use a kernel, you are basically allowed to disable interrupts for as much time as the kernel does witho ...
... few variables. Also, this is the only way that a thread can share variables or data structures with an ISR. In all cases, you should keep interrupts disabled for as little time as possible. If you use a kernel, you are basically allowed to disable interrupts for as much time as the kernel does witho ...
CodeMoctules O O O
... ating system to dynamically allocate system resources among processes and ?exibly implements and enforces a protection scheme. This protection scheme can be formu lated to control the impact of poorly Written applications, erroneous or disruptive application behavior, or other mal ...
... ating system to dynamically allocate system resources among processes and ?exibly implements and enforces a protection scheme. This protection scheme can be formu lated to control the impact of poorly Written applications, erroneous or disruptive application behavior, or other mal ...
The Architecture of a Worldwide Distributed System
... period of learning as much as you can in as many different subjects that are interesting. In this respect I took full advantage of my Ph.D.: I did work ranging from programming my own EEPROMs, to secure network objects, digital video on demand, and a full blown new operating system with its own TCP/ ...
... period of learning as much as you can in as many different subjects that are interesting. In this respect I took full advantage of my Ph.D.: I did work ranging from programming my own EEPROMs, to secure network objects, digital video on demand, and a full blown new operating system with its own TCP/ ...
Developing Interfaces and Interactivity for DSpace with
... – No, but.... – Basic understanding will help diagnose problems – Many skill levels represented here • Some really NEED this knowledge (and may already have it) • Will help others UNDERSTAND their tech people ...
... – No, but.... – Basic understanding will help diagnose problems – Many skill levels represented here • Some really NEED this knowledge (and may already have it) • Will help others UNDERSTAND their tech people ...
CS162 Operating Systems and Systems Programming Lecture 1
... – require repetition of the subject work, – assign an F grade or a 'zero' grade to the subject work, – for serious offenses, assign an F grade for the course. • The instructor must inform the student and the Department Chair in writing of the incident, the action taken, if any, and the student's rig ...
... – require repetition of the subject work, – assign an F grade or a 'zero' grade to the subject work, – for serious offenses, assign an F grade for the course. • The instructor must inform the student and the Department Chair in writing of the incident, the action taken, if any, and the student's rig ...
Investigation of Real-Time Operating Systems : OSEK/VDX and Rubus
... documents produced by OSEK/VDX. OSEK/VDX is a committee that produces standards for realtime operating systems in the European vehicle industry. The report also contains a market evaluation of different OSEK/VDX realtime operating systems. The main differences between OSEK/VDX OS and a realtime oper ...
... documents produced by OSEK/VDX. OSEK/VDX is a committee that produces standards for realtime operating systems in the European vehicle industry. The report also contains a market evaluation of different OSEK/VDX realtime operating systems. The main differences between OSEK/VDX OS and a realtime oper ...
Operating Systems
... per process) timer is created by the kernel on behalf of a thread (or process) when the thread calls the create timer function. In a system that contains more than one clock, the calling thread specifies the clock to which the timer is to be bound; by this, we mean that the timer will keep track of ...
... per process) timer is created by the kernel on behalf of a thread (or process) when the thread calls the create timer function. In a system that contains more than one clock, the calling thread specifies the clock to which the timer is to be bound; by this, we mean that the timer will keep track of ...
Threads (continued)
... • Some other thread may have completed the joint task • E.g., searching a database ...
... • Some other thread may have completed the joint task • E.g., searching a database ...
4.1. Threads
... • A single-threaded application would be unresponsive to the user until the operation had completed. • In contrast, if the time-consuming operation is performed in a separate thread, the application remains responsive to the user. ...
... • A single-threaded application would be unresponsive to the user until the operation had completed. • In contrast, if the time-consuming operation is performed in a separate thread, the application remains responsive to the user. ...
CS162 Operating Systems and Systems Programming Lecture 1
... • Problem: Run multiple applications in such a way that they are protected from one another • Goal: ...
... • Problem: Run multiple applications in such a way that they are protected from one another • Goal: ...