mpi.h - ICTP
... – Function calls that can be made from any compiler, many languages – Just link to it – Wrappers: mpicc, mpif77 ...
... – Function calls that can be made from any compiler, many languages – Just link to it – Wrappers: mpicc, mpif77 ...
Slide 1
... − many concurrent processes • performing different tasks • using different parts of the machine ...
... − many concurrent processes • performing different tasks • using different parts of the machine ...
Operating Systems
... processes • performing different tasks • using different parts of the machine ...
... processes • performing different tasks • using different parts of the machine ...
CS162 Operating Systems and Systems Programming Lecture 1
... • Would this complexity make sense if there were only one application that you cared about? ...
... • Would this complexity make sense if there were only one application that you cared about? ...
Investigation of Real-Time Operating Systems : OSEK/VDX and Rubus
... The aim of this work was to investigate the possibilities and consequences for Haldex Traction of starting to use the OSEK/VDX standard for realtime operating systems. This report contains a summary of the realtime operating system documents produced by OSEK/VDX. OSEK/VDX is a committee that produce ...
... The aim of this work was to investigate the possibilities and consequences for Haldex Traction of starting to use the OSEK/VDX standard for realtime operating systems. This report contains a summary of the realtime operating system documents produced by OSEK/VDX. OSEK/VDX is a committee that produce ...
CPU 410-5H Process Automation
... indicates that minor personal injury can result if proper precautions are not taken. NOTICE indicates that property damage can result if proper precautions are not taken. If more than one degree of danger is present, the warning notice representing the highest degree of danger will be used. A notice ...
... indicates that minor personal injury can result if proper precautions are not taken. NOTICE indicates that property damage can result if proper precautions are not taken. If more than one degree of danger is present, the warning notice representing the highest degree of danger will be used. A notice ...
file (1.5 MB, ppt)
... based on their priorities UNIX shares memory among processes by dividing RAM into equal-sized pages (e.g., 4K bytes) and allocating them; only those pages of a process that are needed in RAM are loaded from disk while pages of RAM that are not accessed are saved back to disk UNIX shares disk spa ...
... based on their priorities UNIX shares memory among processes by dividing RAM into equal-sized pages (e.g., 4K bytes) and allocating them; only those pages of a process that are needed in RAM are loaded from disk while pages of RAM that are not accessed are saved back to disk UNIX shares disk spa ...
INF1060: Introduction to Operating Systems and Data Communication
... to processes INF1060 – introduction to operating systems and data communication ...
... to processes INF1060 – introduction to operating systems and data communication ...
CS162 Operating Systems and Systems Programming Lecture 1
... • Problem: Run multiple applications in such a way that they are protected from one another • Goal: ...
... • Problem: Run multiple applications in such a way that they are protected from one another • Goal: ...
S7-400H SIMATIC Fault-tolerant systems S7-400H
... indicates that minor personal injury can result if proper precautions are not taken. NOTICE indicates that property damage can result if proper precautions are not taken. If more than one degree of danger is present, the warning notice representing the highest degree of danger will be used. A notice ...
... indicates that minor personal injury can result if proper precautions are not taken. NOTICE indicates that property damage can result if proper precautions are not taken. If more than one degree of danger is present, the warning notice representing the highest degree of danger will be used. A notice ...
VAX 6000 Models 300 and 400 Service Manual
...(XYP) Module . . . . . . . . . . . . . . . . . . . . . . . .
Typical (xyp) Configuration . . . . . . . . . . . . .
(xyp) Block Diagram . . . . . . . . . . . . . . . . . . .
Selection of Boot Processor . . . . . . . . . . . . . . . . . . . . . . . . . . .
( ...
...
Intel SGX Explained - Cryptology ePrint Archive
... process (§ 5.8) to convince itself that it is communicating with an enclave that has a specific measurement hash, and is running in a secure environment. Execution flow can only enter an enclave via special CPU instructions (§ 5.4), which are similar to the mechanism for switching from user mode to ...
... process (§ 5.8) to convince itself that it is communicating with an enclave that has a specific measurement hash, and is running in a secure environment. Execution flow can only enter an enclave via special CPU instructions (§ 5.4), which are similar to the mechanism for switching from user mode to ...
Secure Virtual Architecture: Security for Commodity Software Systems
... Commodity operating systems are entrusted with providing security to the applications we use everyday, and yet they suffer from the same security vulnerabilities as user-space applications: they are susceptible to memory safety attacks such as buffer overflows, and they can be tricked into dynamically ...
... Commodity operating systems are entrusted with providing security to the applications we use everyday, and yet they suffer from the same security vulnerabilities as user-space applications: they are susceptible to memory safety attacks such as buffer overflows, and they can be tricked into dynamically ...
Partitioning Implementations for IBM E p5 Servers
... 5.9 API-based DLPAR event handling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 194 5.9.1 The dr_reconfig system call . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195 5.9.2 A sample code using the dr_reconfig system call . . . . . . . . . . . . . . 199 5.9.3 Sample output ...
... 5.9 API-based DLPAR event handling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 194 5.9.1 The dr_reconfig system call . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195 5.9.2 A sample code using the dr_reconfig system call . . . . . . . . . . . . . . 199 5.9.3 Sample output ...
Proceedings of the FREENIX Track: 2003 USENIX Annual Technical Conference
... configuring hardware than standard BIOSes do, and its “footprint” in memory is not really that much larger. As of 1999 there are many systems (kmonte, kexec, bootimg, LOBOS) that allow Linux to boot another operating system. The result is that LinuxBIOS can load a kernel over any device, network, pr ...
... configuring hardware than standard BIOSes do, and its “footprint” in memory is not really that much larger. As of 1999 there are many systems (kmonte, kexec, bootimg, LOBOS) that allow Linux to boot another operating system. The result is that LinuxBIOS can load a kernel over any device, network, pr ...
BUILDING A DEPENDABLE OPERATING SYSTEM: FAULT TOLERANCE IN MINIX 3
... ICT Australia. The relaxed atmosphere and top-notch L4 research team made for another pleasant and inspiring stay. I would like to thank my former colleagues and all others who contributed to these experiences. Most of my time was spent at Vrije Universiteit Amsterdam though. Special mention goes th ...
... ICT Australia. The relaxed atmosphere and top-notch L4 research team made for another pleasant and inspiring stay. I would like to thank my former colleagues and all others who contributed to these experiences. Most of my time was spent at Vrije Universiteit Amsterdam though. Special mention goes th ...
PODARCH: Protecting Legacy Applications with a Purely Hardware
... Finally, secure execution primitives do not protect applications outside of the CPU’s environment or on CPUs which have been tampered with and reverse engineered. For example, the P OD FS application is an encrypted binary. We assume that its encryption key is not accidentally delivered to a malicio ...
... Finally, secure execution primitives do not protect applications outside of the CPU’s environment or on CPUs which have been tampered with and reverse engineered. For example, the P OD FS application is an encrypted binary. We assume that its encryption key is not accidentally delivered to a malicio ...
CodeMoctules O O O
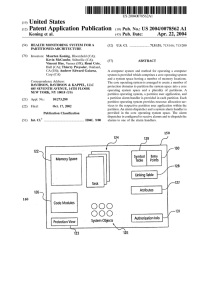
... [0004] In order to improve system protection, it has been proposed to provide an operating system that implements a “protection domain” architecture. VxWorks® AE, marketed by Wind River Systems of Alameda, Calif., is an example of such a protection domain system. Basically, the protection domain sys ...
... [0004] In order to improve system protection, it has been proposed to provide an operating system that implements a “protection domain” architecture. VxWorks® AE, marketed by Wind River Systems of Alameda, Calif., is an example of such a protection domain system. Basically, the protection domain sys ...
tutorial - Pixelbanane.de
... • Program development workload – Use selectors to separate out modes ...
... • Program development workload – Use selectors to separate out modes ...
3. Implemented Operating System
... Running tasks in parallel and, synchronization and communication between them are common to all systems. There are many methods to achieve these purposes like using an infinite loop that checks the all the tasks continuously. But most of them are not reliable, not flexible and are not used very easi ...
... Running tasks in parallel and, synchronization and communication between them are common to all systems. There are many methods to achieve these purposes like using an infinite loop that checks the all the tasks continuously. But most of them are not reliable, not flexible and are not used very easi ...
Design and Implementation of Safety Critical Real
... Integrated Real-Time Systems consist of various real-time applications which ensure safe running of the systems. A modern Integrated Real-Time System, such as factory automation or a modern vehicle with many features of automation, consists of many applications running at different criticality level ...
... Integrated Real-Time Systems consist of various real-time applications which ensure safe running of the systems. A modern Integrated Real-Time System, such as factory automation or a modern vehicle with many features of automation, consists of many applications running at different criticality level ...
A comprehensive cross-development tool chain and runtime
... model that makes it easy to break complex applications into simpler concurrent processes, communicating via high-speed direct messages. This makes complex applications easier to conceptualize, model, partition, and debug. It also provides transparency that separates applications from the details of ...
... model that makes it easy to break complex applications into simpler concurrent processes, communicating via high-speed direct messages. This makes complex applications easier to conceptualize, model, partition, and debug. It also provides transparency that separates applications from the details of ...