Porting a SAS/AF Application from PC to a MAC
... on Folders as on PC directories, so most of this code ports very smoothly. Watch out for code that does not check upperJlower case names though, since the Mac supports lowercase folder and file names. (This will apply to code ported to UNIX as well.) ...
... on Folders as on PC directories, so most of this code ports very smoothly. Watch out for code that does not check upperJlower case names though, since the Mac supports lowercase folder and file names. (This will apply to code ported to UNIX as well.) ...
Votenet Security Infrastructure
... Of course many factors play into it, but one of the key aspects is the trust and confidence of your constituents that your elections are secure and reliable, enabling them to participate without concern that their personal information, voting choices, or other data will be improperly accessed or use ...
... Of course many factors play into it, but one of the key aspects is the trust and confidence of your constituents that your elections are secure and reliable, enabling them to participate without concern that their personal information, voting choices, or other data will be improperly accessed or use ...
Whitepaper: Network Penetration Testing
... networks can personify polar differences in characters. It can vary from remote system & password compromise, web server, database, network service, network device, directory and miscellaneous non-configuration to information disclosure to weak cryptography. This array of vulnerabilities propel the ...
... networks can personify polar differences in characters. It can vary from remote system & password compromise, web server, database, network service, network device, directory and miscellaneous non-configuration to information disclosure to weak cryptography. This array of vulnerabilities propel the ...
SMALL FIRMS CYBERSECURITY GUIDANCE
... Updated anti-virus software, in addition to web security software, greatly reduces the risk of unintentional and intentional computer infection. Additionally, personal vigilance against suspicious emails and attachments greatly reduces cyber threats. ...
... Updated anti-virus software, in addition to web security software, greatly reduces the risk of unintentional and intentional computer infection. Additionally, personal vigilance against suspicious emails and attachments greatly reduces cyber threats. ...
A Novel Approach for Computer Security Education Using Minix
... network security are two core courses. These courses teach students how to design, implement, analyze, test, and operate a system or a network with the goal of making it secure. Pedagogical research has shown that students’ learning is enhanced if they can engage in a significant amount of hands-on ...
... network security are two core courses. These courses teach students how to design, implement, analyze, test, and operate a system or a network with the goal of making it secure. Pedagogical research has shown that students’ learning is enhanced if they can engage in a significant amount of hands-on ...
protect a system from cyber attacks?
... computer systems and through computer networks. The objective of cyber security is to protect information and physical assets from theft, corruption, or natural disaster, while allowing the information and assets to remain accessible and productive to its intended users. It is composed of procedures ...
... computer systems and through computer networks. The objective of cyber security is to protect information and physical assets from theft, corruption, or natural disaster, while allowing the information and assets to remain accessible and productive to its intended users. It is composed of procedures ...
XML: Part - Houston Community College System
... • Two types of Java applets: – Unsigned Java applet: program that does not come from a trusted source – Signed Java applet: has a digital signature proving the program is from a trusted source and has not been ...
... • Two types of Java applets: – Unsigned Java applet: program that does not come from a trusted source – Signed Java applet: has a digital signature proving the program is from a trusted source and has not been ...
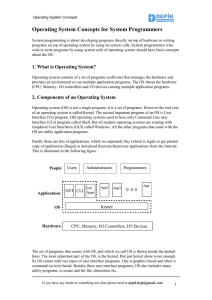
Operating System Concepts for System Programmers
... Finally people use OS for different purposes. Ordinary users will use it to run the applications. Administrators are responsible for maintaining the OS and other applications. And programmers are responsible for the development of new programs. We may also classify the programmers into System Progra ...
... Finally people use OS for different purposes. Ordinary users will use it to run the applications. Administrators are responsible for maintaining the OS and other applications. And programmers are responsible for the development of new programs. We may also classify the programmers into System Progra ...
Chap 6: Web Security - IUP Personal Websites
... • Two types of Java applets: – Unsigned Java applet: program that does not come from a trusted source – Signed Java applet: has a digital signature proving the program is from a trusted source and has not been ...
... • Two types of Java applets: – Unsigned Java applet: program that does not come from a trusted source – Signed Java applet: has a digital signature proving the program is from a trusted source and has not been ...
Lecture 2 - Rabie A. Ramadan
... resources must be allocated to each of them Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code ...
... resources must be allocated to each of them Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code ...
Network Administration Review
... and the required settings for connections across the Internet including classful address ranges, public/private addressing, and subnet masks • Identify the well-known ports associated with commonly used services and ...
... and the required settings for connections across the Internet including classful address ranges, public/private addressing, and subnet masks • Identify the well-known ports associated with commonly used services and ...
OSI Defense in Depth to Increase Application Security
... protection methods are the responsibility of the programmer at this layer. Backdoor attacks occur at this level and it is the programmer’s responsibility to close those doors. IT managers can use access control methods described to assist in preventing backdoor attacks; also, IT managers can set up ...
... protection methods are the responsibility of the programmer at this layer. Backdoor attacks occur at this level and it is the programmer’s responsibility to close those doors. IT managers can use access control methods described to assist in preventing backdoor attacks; also, IT managers can set up ...
THE WINDOWS OPERATING SYSTEM
... and the 32-bit 80386 chips. The resident portion at this stage had grown to a minimum of 46 Kbytes, with more required if certain optional extensions were selected. By this time, DOS was being used in an environment far beyond its capabilities. The introduction of the 80486 and then the Intel Pentiu ...
... and the 32-bit 80386 chips. The resident portion at this stage had grown to a minimum of 46 Kbytes, with more required if certain optional extensions were selected. By this time, DOS was being used in an environment far beyond its capabilities. The introduction of the 80486 and then the Intel Pentiu ...
1. Introduction
... Device-status table contains entry for each I/O device indicating its type, address, and state Operating system indexes into I/O device table to determine device status and to modify table entry to include interrupt Operating System Concepts – 7th Edition, Jan 12, 2005 ...
... Device-status table contains entry for each I/O device indicating its type, address, and state Operating system indexes into I/O device table to determine device status and to modify table entry to include interrupt Operating System Concepts – 7th Edition, Jan 12, 2005 ...
Self-Assessment Interactive Topic 1
... 3.1What is the purpose of the command interpreter? Why is it usually separate from the kernel? Answer: It reads commands from the user or from a file of commands and executes them, usually by turning them into one or more system calls. It is usually not part of the kernel since the command interpret ...
... 3.1What is the purpose of the command interpreter? Why is it usually separate from the kernel? Answer: It reads commands from the user or from a file of commands and executes them, usually by turning them into one or more system calls. It is usually not part of the kernel since the command interpret ...
2008-11-11
... • How operating system security can cooperate with other measures • Open discussion ...
... • How operating system security can cooperate with other measures • Open discussion ...
Architecture Intégrée | Sécurité et protection de la propriété
... is believed to have destroyed up to 1,000 F-Secure did not name the affected vendors, but said that two of them develop ICS remote management uranium enrichment centrifuges in Iran, software and the third supplies high-precision industrial cameras and related software. According to the security rese ...
... is believed to have destroyed up to 1,000 F-Secure did not name the affected vendors, but said that two of them develop ICS remote management uranium enrichment centrifuges in Iran, software and the third supplies high-precision industrial cameras and related software. According to the security rese ...
Convergence of Desktop and Web Applications on a Multi-Service OS
... tion is treated as a principal on the browser platform and that its origin labels the principal [19]. However, today’s browsers have never been designed and constructed as an OS for these web applications: different principals may coexist in the same protection domain, and there is no coherent supp ...
... tion is treated as a principal on the browser platform and that its origin labels the principal [19]. However, today’s browsers have never been designed and constructed as an OS for these web applications: different principals may coexist in the same protection domain, and there is no coherent supp ...
Department of Computer Science and Engineering
... program that loads the Linux kernel into the computer's main memory, by being executed by the computer when it is turned on and after the firmware initialization is performed. An init program, such as the traditional sysvinit and the newer systemd, OpenRC and Upstart. This is the first process launc ...
... program that loads the Linux kernel into the computer's main memory, by being executed by the computer when it is turned on and after the firmware initialization is performed. An init program, such as the traditional sysvinit and the newer systemd, OpenRC and Upstart. This is the first process launc ...
9-SystemSoftware - Systems and Computer Engineering
... – Some of these are foreground processes, that is processes that interact with human users and perform work form them. – Others are background processes (e.g. incoming mail), which are not associated with particular users, but instead have a specific function, also called daemons Fall 2012 ...
... – Some of these are foreground processes, that is processes that interact with human users and perform work form them. – Others are background processes (e.g. incoming mail), which are not associated with particular users, but instead have a specific function, also called daemons Fall 2012 ...
Application Security within Java 2, Standard Edition (J2SE)
... is loaded, the system uses a class called the SecureClassLoader (java.security.SecureClassLoader) to load the class. First the class is loaded from the specified URL and then the digital signature of the class is checked to make sure that the class is correct and intact. A CodeSource object is deriv ...
... is loaded, the system uses a class called the SecureClassLoader (java.security.SecureClassLoader) to load the class. First the class is loaded from the specified URL and then the digital signature of the class is checked to make sure that the class is correct and intact. A CodeSource object is deriv ...
Training Package - Install and optimise operating system software
... assessment must confirm the ability to install and improve system performance with minimum disruption to clients. To demonstrate competency in this unit the person will require access to: personal computer/workstation operating system software and technical documentation. ...
... assessment must confirm the ability to install and improve system performance with minimum disruption to clients. To demonstrate competency in this unit the person will require access to: personal computer/workstation operating system software and technical documentation. ...
SECURITY METRICS FOR ENTERPRISE INFORMATION SYSTEMS Interdisciplinarity – New Approaches and Perspectives
... required performance of the best practices to generate specific results. IT performance assessment methodology (coordinated by US Department of Defence) has three components namely: capabilities, attribute level, and specific metrics. The attribute level addresses the requirement that support that m ...
... required performance of the best practices to generate specific results. IT performance assessment methodology (coordinated by US Department of Defence) has three components namely: capabilities, attribute level, and specific metrics. The attribute level addresses the requirement that support that m ...
ErgoSoft RIP recommended System configuration
... is recommended to have a high tact frequency on the individual processor cores rather than a large amount of cores, as the RIP-Server process profits most from a high performing individual core. It is possible to configure the RIP-Server so it uses multiple cores, and certain processes such as Dithe ...
... is recommended to have a high tact frequency on the individual processor cores rather than a large amount of cores, as the RIP-Server process profits most from a high performing individual core. It is possible to configure the RIP-Server so it uses multiple cores, and certain processes such as Dithe ...