(OS) license terms do not permit multiple users to access
... Requirements for a Terminal Services Client Access License (TS CAL) Microsoft licenses its desktop applications on a per-device basis. Per-device licensing means a customer must obtain a license for each desktop on or from which the product is used or accessed. For example, when a desktop applicatio ...
... Requirements for a Terminal Services Client Access License (TS CAL) Microsoft licenses its desktop applications on a per-device basis. Per-device licensing means a customer must obtain a license for each desktop on or from which the product is used or accessed. For example, when a desktop applicatio ...
Chapter 2 – Operating System Overview
... 5. The earliest computers employed ________________ processing, a name derived by the way the users were forced to access the systems. ANS: serial 6. The special type of programming language used to provide instructions to a monitor in a batch-processing scheme is called ________________. ANS: Job C ...
... 5. The earliest computers employed ________________ processing, a name derived by the way the users were forced to access the systems. ANS: serial 6. The special type of programming language used to provide instructions to a monitor in a batch-processing scheme is called ________________. ANS: Job C ...
Systeemanalyse in Ontwerpprojecten
... • ARPA network: network with basic communication functionality (like TCP/IP) in the ’60ies of previous century • 1991: Tim-Berners Lee at CERN (Geneve) has the idea of connecting information sources using links (defined by URLs); this results into the World Wide Web • Business/government/individuals ...
... • ARPA network: network with basic communication functionality (like TCP/IP) in the ’60ies of previous century • 1991: Tim-Berners Lee at CERN (Geneve) has the idea of connecting information sources using links (defined by URLs); this results into the World Wide Web • Business/government/individuals ...
Lecture 15
... • The new way – better systems (1000x) – Add more $150 blades and a bigger switch – Spreading the work over many nodes is a huge win • Performance – may be linear with the number of blades • Availability – service continues despite node failures CS 111 Fall 2015 ...
... • The new way – better systems (1000x) – Add more $150 blades and a bigger switch – Spreading the work over many nodes is a huge win • Performance – may be linear with the number of blades • Availability – service continues despite node failures CS 111 Fall 2015 ...
Operating Systems, 082
... Running user commands User types: ‘grep some_word file_name’ Shell parses the command, inserts the strings grep, some_word, file_name into argv and their number to argc Next, the shell uses fork() to create a process (same user ID) Now, it takes the executable name grep and the arguments, a ...
... Running user commands User types: ‘grep some_word file_name’ Shell parses the command, inserts the strings grep, some_word, file_name into argv and their number to argc Next, the shell uses fork() to create a process (same user ID) Now, it takes the executable name grep and the arguments, a ...
Computer Security, Ethics, and Privacy
... Inform merchants that you do not want them to distribute your personal information ...
... Inform merchants that you do not want them to distribute your personal information ...
Threads, SMP, and Microkernels
... ◦ Message are sent without knowing what the target machine is ...
... ◦ Message are sent without knowing what the target machine is ...
Threads, SMP, and Microkernels
... ▫ Message are sent without knowing what the target machine is ...
... ▫ Message are sent without knowing what the target machine is ...
Windows booting procedure
... When kernel is loaded in the primary memory services for each process is started and the registry entry for those services can be found at HKEY_LOCAL_MACHINE - System - Current control set - Services. Winlogon.exe (C:\Windows\system32\winlogon.exe) is the last service started during this process. Wi ...
... When kernel is loaded in the primary memory services for each process is started and the registry entry for those services can be found at HKEY_LOCAL_MACHINE - System - Current control set - Services. Winlogon.exe (C:\Windows\system32\winlogon.exe) is the last service started during this process. Wi ...
Introduction to Operating System
... •Assume that a program has 1,200 cards. Assume further the card reader can read 1200 cards per minute (or 20 cards per second) while the CPU can process 300 cards per second. This means that it will take the card reader 60 seconds to read the cards while the CPU will take only 4 seconds to process t ...
... •Assume that a program has 1,200 cards. Assume further the card reader can read 1200 cards per minute (or 20 cards per second) while the CPU can process 300 cards per second. This means that it will take the card reader 60 seconds to read the cards while the CPU will take only 4 seconds to process t ...
Spring 2008 - Computer Science
... and mobile computing will be provided, time permitting. The main emphasis is on the various alternative approaches to the solution of problems encountered in the design of distributed operating systems. This course builds upon the topics covered in undergraduate operating systems course, such as pro ...
... and mobile computing will be provided, time permitting. The main emphasis is on the various alternative approaches to the solution of problems encountered in the design of distributed operating systems. This course builds upon the topics covered in undergraduate operating systems course, such as pro ...
how-to-maintain-your-computer-2011
... http://www.microsoft.com/windowsxp/using/networking/security/winfirewall.mspx ...
... http://www.microsoft.com/windowsxp/using/networking/security/winfirewall.mspx ...
device special files
... • Scanners – scans text and images to be manipulated by software on your computer. – Once in the computer, the digital image from the scanner can be saved in a variety of graphics image formats, edited, merged with other images or text, transmitted over the Internet or other network connection, and ...
... • Scanners – scans text and images to be manipulated by software on your computer. – Once in the computer, the digital image from the scanner can be saved in a variety of graphics image formats, edited, merged with other images or text, transmitted over the Internet or other network connection, and ...
Threads, SMP, and Microkernels
... – Message are sent without knowing what the target machine is ...
... – Message are sent without knowing what the target machine is ...
Assignment 2 description. - School of Computer Science Student
... translated to physical addresses using a very simple translation scheme and the total size of the virtual address spaces of all running processes cannot be any larger than the size of physical memory. runprogram.c: This file contains only one function, runprogram(), which is responsible for launchin ...
... translated to physical addresses using a very simple translation scheme and the total size of the virtual address spaces of all running processes cannot be any larger than the size of physical memory. runprogram.c: This file contains only one function, runprogram(), which is responsible for launchin ...
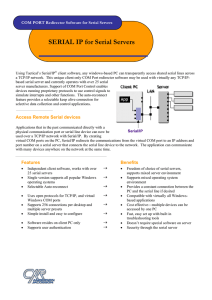
SERIAL-IP COM PORT Redirector Software for Serial Servers
... 98/95 operating systems Serial servers for use with Serial/IP: ...
... 98/95 operating systems Serial servers for use with Serial/IP: ...
Introduction:- CS-502 Operating Systems
... security: how is the integrity of the OS and its resources ensured? protection: how is one user/program protected from another? performance: how do we make it all go fast? reliability: what happens if something goes wrong – hardware or software extensibility: can we add new features? communication: ...
... security: how is the integrity of the OS and its resources ensured? protection: how is one user/program protected from another? performance: how do we make it all go fast? reliability: what happens if something goes wrong – hardware or software extensibility: can we add new features? communication: ...
Operating System
... The OS runs in kernel mode but the compilers and editors run in user mode. If a user does not like a particular complier, the user is free to write his own but he is not free to write his own disk interrupt handler, which is part of the OS. ...
... The OS runs in kernel mode but the compilers and editors run in user mode. If a user does not like a particular complier, the user is free to write his own but he is not free to write his own disk interrupt handler, which is part of the OS. ...
Hardware architecture of a Real Time Operating System
... A real-time operating system (RTOS) is an operating system that supports and guarantees timely responses to external and internal events of real-time systems. An RTOS monitors, responds to, and controls an external environment, which is connected to the computer system through sensors, actuators, or ...
... A real-time operating system (RTOS) is an operating system that supports and guarantees timely responses to external and internal events of real-time systems. An RTOS monitors, responds to, and controls an external environment, which is connected to the computer system through sensors, actuators, or ...
Blackfin VisualDSP++
... Usage: in ISR the object of this class must be declared before the first using of any ICS and before nested interrupts enable if any. On ISR exit, the class destructor is called. The destructor calls the scheduler which performs process rescheduling if need. I.e. if there was an event arisen in the ...
... Usage: in ISR the object of this class must be declared before the first using of any ICS and before nested interrupts enable if any. On ISR exit, the class destructor is called. The destructor calls the scheduler which performs process rescheduling if need. I.e. if there was an event arisen in the ...
Operating system
... switch occurs so frequently that the user can interact with each program as it is running each command is short so only a little CPU time is needed for each user each user is given the impression that the entire system is dedicated to his use Batch jobs could be running in background ...
... switch occurs so frequently that the user can interact with each program as it is running each command is short so only a little CPU time is needed for each user each user is given the impression that the entire system is dedicated to his use Batch jobs could be running in background ...
- Whatcom Community College
... • IDS/IPS systems, if not “tuned” properly, generate an enormous amount of false positives (false alarms). Tuning these out can result, however, in missing key indicators of an attack. ...
... • IDS/IPS systems, if not “tuned” properly, generate an enormous amount of false positives (false alarms). Tuning these out can result, however, in missing key indicators of an attack. ...
Word Template
... Seamlessly investigate bot infections with advanced logs and management system providing key inputs such as infected machine/user, bot name, bot actions (such as communication with command & control and spam sending), amount of data sent/received, infection severity and more. In addition, the soluti ...
... Seamlessly investigate bot infections with advanced logs and management system providing key inputs such as infected machine/user, bot name, bot actions (such as communication with command & control and spam sending), amount of data sent/received, infection severity and more. In addition, the soluti ...