CS311 Introduction to Operating Systems I - Summer 2009
... • Reproduce the diagram of the organization of Unix. • Describe the memory organization of a typical process in a common operating system. • What is a context switch? – Ans: It is when a process is switched out of the microprocessor and another is switched in. It is costly in terms of cycles because ...
... • Reproduce the diagram of the organization of Unix. • Describe the memory organization of a typical process in a common operating system. • What is a context switch? – Ans: It is when a process is switched out of the microprocessor and another is switched in. It is costly in terms of cycles because ...
System Programs - Bilkent University Computer Engineering
... devices, etc. – Accounting - To keep track of which users use how much and what kinds of computer resources – Protection and security - The owners of information should be able to control use of that information; concurrent processes should not interfere with each other • Access control to resources ...
... devices, etc. – Accounting - To keep track of which users use how much and what kinds of computer resources – Protection and security - The owners of information should be able to control use of that information; concurrent processes should not interfere with each other • Access control to resources ...
Word Processors
... Know different types of utility software that are used to keep computers systems running smoothly. ...
... Know different types of utility software that are used to keep computers systems running smoothly. ...
Computer Operating Systems (COP 4610)
... understanding of interrupts, interrupt handling, processes, process management, file and device management, and other features of control programs. A team design project is required. ...
... understanding of interrupts, interrupt handling, processes, process management, file and device management, and other features of control programs. A team design project is required. ...
Read more
... PCI 5200. On the software side, Zentyal was configured with the following active modules: Network, Firewall, DHCP, DNS, Events, Logs, NTP, VPN, Users and Groups, File Sharing, HTTP Proxy and User Corner. ...
... PCI 5200. On the software side, Zentyal was configured with the following active modules: Network, Firewall, DHCP, DNS, Events, Logs, NTP, VPN, Users and Groups, File Sharing, HTTP Proxy and User Corner. ...
Linux Kernel—File Systems
... contains pointers to functions that can be used to act on any file An open file descriptor contains pointer to functions which can only ...
... contains pointers to functions that can be used to act on any file An open file descriptor contains pointer to functions which can only ...
Deployment of Sensing Devices on Critical Infrastructure
... Digression: The Windows Registry – We saw that the OS acts as intermediary between software and peripheral devices. – OS needs to know something about these devices (what is it, how installed, any special settings, etc.) – Windows Registry: keeps track of your computer’s peripheral devices & softwa ...
... Digression: The Windows Registry – We saw that the OS acts as intermediary between software and peripheral devices. – OS needs to know something about these devices (what is it, how installed, any special settings, etc.) – Windows Registry: keeps track of your computer’s peripheral devices & softwa ...
Lecture 5 - Rabie A. Ramadan
... Digression: The Windows Registry – We saw that the OS acts as intermediary between software and peripheral devices. – OS needs to know something about these devices (what is it, how installed, any special settings, etc.) – Windows Registry: keeps track of your computer’s peripheral devices & softwa ...
... Digression: The Windows Registry – We saw that the OS acts as intermediary between software and peripheral devices. – OS needs to know something about these devices (what is it, how installed, any special settings, etc.) – Windows Registry: keeps track of your computer’s peripheral devices & softwa ...
CNG 131 – Principles of Information Assurance Provides students
... Presents methods to identify technology and communication infrastructure vulnerabilities and appropriate countermeasures to prevent and mitigate failure risks for an organization. The course will take an enterprise-wide approach to developing a disaster recovery plan. CNG 257 – Network Defense and C ...
... Presents methods to identify technology and communication infrastructure vulnerabilities and appropriate countermeasures to prevent and mitigate failure risks for an organization. The course will take an enterprise-wide approach to developing a disaster recovery plan. CNG 257 – Network Defense and C ...
Netscape: System Commander in Patagonia
... host the System Oberon. Oberon is a programming language, a run-time- and operating system with an integrated development environment for object oriented or structured programming. The Oberon system is kept lean, simple and easily fits into a very small disk partition or main memory. All data is sto ...
... host the System Oberon. Oberon is a programming language, a run-time- and operating system with an integrated development environment for object oriented or structured programming. The Oberon system is kept lean, simple and easily fits into a very small disk partition or main memory. All data is sto ...
OPERATING SYSTEMS
... It is an activity that enables several users to send output to a single printer while input and processing processes are happening. Each job to be printed is stored on an intermediate device (disk) rather than being directly sent to printer. ...
... It is an activity that enables several users to send output to a single printer while input and processing processes are happening. Each job to be printed is stored on an intermediate device (disk) rather than being directly sent to printer. ...
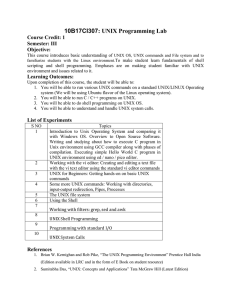
10B17CI307: UNIX Programming Lab
... Introduction to Unix Operating System and comparing it with Windows OS. Overview to Open Source Software. Writing and studying about how to execute C program in Unix environment using GCC compiler along with phases of compilation. Executing simple Hello World C program in UNIX environment using ed / ...
... Introduction to Unix Operating System and comparing it with Windows OS. Overview to Open Source Software. Writing and studying about how to execute C program in Unix environment using GCC compiler along with phases of compilation. Executing simple Hello World C program in UNIX environment using ed / ...
ppt
... Analysis of Example • Another difference between the Unix system and the SAPC is the presence/ absence of an operating system – UNIX is an operating system that runs programs in a protected environment. Our code can not do some things such as access hardware directly – Tutor is a debug monitor only ...
... Analysis of Example • Another difference between the Unix system and the SAPC is the presence/ absence of an operating system – UNIX is an operating system that runs programs in a protected environment. Our code can not do some things such as access hardware directly – Tutor is a debug monitor only ...
AccessControlSimulation
... sufficiently safeguarded from unauthorized disclosure or modification. These deficiencies are the basis of GAO’s determination that IRS had a material weakness in internal control ...
... sufficiently safeguarded from unauthorized disclosure or modification. These deficiencies are the basis of GAO’s determination that IRS had a material weakness in internal control ...
Ch10aProtectionMechanisms
... PSK v. RADIUS WPA and WPA-2 operate in two modes Pre-Shared Key (PSK) ...
... PSK v. RADIUS WPA and WPA-2 operate in two modes Pre-Shared Key (PSK) ...
Allowable Process States - Universitas Pendidikan Indonesia
... FAT: Data Region • Where the actual file and directory data is stored • Takes up the majority of the partition • A partition is divided into identically-sized clusters whose size vary depending on the FAT version and partition size – typically cluster sizes lie between 2KB and 32KB and are not nece ...
... FAT: Data Region • Where the actual file and directory data is stored • Takes up the majority of the partition • A partition is divided into identically-sized clusters whose size vary depending on the FAT version and partition size – typically cluster sizes lie between 2KB and 32KB and are not nece ...
MS-DOS-&-PC-DOS-by-Lindsey-Buranych-Alan-Crouch
... FAT: Data Region • Where the actual file and directory data is stored • Takes up the majority of the partition • A partition is divided into identically-sized clusters whose size vary depending on the FAT version and partition size – typically cluster sizes lie between 2KB and 32KB and are not nece ...
... FAT: Data Region • Where the actual file and directory data is stored • Takes up the majority of the partition • A partition is divided into identically-sized clusters whose size vary depending on the FAT version and partition size – typically cluster sizes lie between 2KB and 32KB and are not nece ...
Slides
... list files and directories list all files and directories make a directory change to named directory change to home-directory change to home-directory change to parent directory ...
... list files and directories list all files and directories make a directory change to named directory change to home-directory change to home-directory change to parent directory ...
Operating System Research Worksheet
... 7. Many people now are using mobile devices. List 3 popular mobile operating systems. Create a chart to compare desktop OS’s to mobile OS’s. ...
... 7. Many people now are using mobile devices. List 3 popular mobile operating systems. Create a chart to compare desktop OS’s to mobile OS’s. ...
Lecture 1
... kept in memory and on disk (the CPU is allocated to a job only if the job is in memory). •A job is swapped in and out of memory to the disk. •On-line communication between the user and the system is provided; when the operating system finishes the execution of one command, it seeks the next “control ...
... kept in memory and on disk (the CPU is allocated to a job only if the job is in memory). •A job is swapped in and out of memory to the disk. •On-line communication between the user and the system is provided; when the operating system finishes the execution of one command, it seeks the next “control ...
Operating System
... Transfers files between main memory and secondary storage, manages file folders, allocates the secondary storage space, and provides file protection and recovery ...
... Transfers files between main memory and secondary storage, manages file folders, allocates the secondary storage space, and provides file protection and recovery ...
Operating System
... Transfers files between main memory and secondary storage, manages file folders, allocates the secondary storage space, and provides file protection and recovery ...
... Transfers files between main memory and secondary storage, manages file folders, allocates the secondary storage space, and provides file protection and recovery ...
Operating System
... Transfers files between main memory and secondary storage, manages file folders, allocates the secondary storage space, and provides file protection and recovery ...
... Transfers files between main memory and secondary storage, manages file folders, allocates the secondary storage space, and provides file protection and recovery ...