Operating System: A Software Engineering Perspective
... Real systems have “uses” cycles File system requires virtual memory services (buffers) Virtual memory would like to use files for its backing store ...
... Real systems have “uses” cycles File system requires virtual memory services (buffers) Virtual memory would like to use files for its backing store ...
Desktop PC Operating Systems
... A file containing commands to automatically configure a personal computer on start up. ...
... A file containing commands to automatically configure a personal computer on start up. ...
CMSC 312 Introduction to Operating System Syllabus
... 2. Understand process management in operating systems, including such topics as process definition, threads, scheduling, synchronization and deadlocks. 3. Understand memory management in operating systems, including such topics as main and virtual memories, memory allocation and paging and segmentat ...
... 2. Understand process management in operating systems, including such topics as process definition, threads, scheduling, synchronization and deadlocks. 3. Understand memory management in operating systems, including such topics as main and virtual memories, memory allocation and paging and segmentat ...
Chapter 5 Protecting Information Resources
... ◦ Callback modems ◦ Firewalls ◦ Intrusion detection systems ...
... ◦ Callback modems ◦ Firewalls ◦ Intrusion detection systems ...
Software - Hoxie Public Schools
... other software to communicate with each other. There are many brands and versions of operating ...
... other software to communicate with each other. There are many brands and versions of operating ...
security
... • Produce fixed-length hash (~32 bits) from variable-length message – It is computationally infeasible to find a message with that hash; in fact one can't determine any usable information about a message with that hash, not even a single bit. – Biometrics usually work the same way! ...
... • Produce fixed-length hash (~32 bits) from variable-length message – It is computationally infeasible to find a message with that hash; in fact one can't determine any usable information about a message with that hash, not even a single bit. – Biometrics usually work the same way! ...
ppt in chapter 11
... plus firewall devices. Internal routers provide additional security to the network by screening traffic to various parts of the protected corporate network, and they do this using access lists. You can see where each of these types of devices are found in Figure below. ...
... plus firewall devices. Internal routers provide additional security to the network by screening traffic to various parts of the protected corporate network, and they do this using access lists. You can see where each of these types of devices are found in Figure below. ...
Operating System
... lilo.conf parameters – boot: tells LILO where to install the boot loader. – map: points to the map file used by LILO internally during bootup. – install: is one of the files used internally by LILO during the boot process. This holds both the primary and secondary parts of the boot loader. A segme ...
... lilo.conf parameters – boot: tells LILO where to install the boot loader. – map: points to the map file used by LILO internally during bootup. – install: is one of the files used internally by LILO during the boot process. This holds both the primary and secondary parts of the boot loader. A segme ...
MINIX 3: status report and current research
... carefully saves its state in the data store so the new component can find it later. After the new version has been started, it goes to the data store to fetch the saved state, reformats and converts it as necessary, and starts processing the queued requests. The other components should not even noti ...
... carefully saves its state in the data store so the new component can find it later. After the new version has been started, it goes to the data store to fetch the saved state, reformats and converts it as necessary, and starts processing the queued requests. The other components should not even noti ...
Lecture 15 Designing Trusted Operating Systems Thierry Sans
... Developed by the NSA to implements the multilevel military security policy proposed by the US DoD First released as a Linux patch, SELinux is now fully integrated into the Linux Kernel (version 2.6) ...
... Developed by the NSA to implements the multilevel military security policy proposed by the US DoD First released as a Linux patch, SELinux is now fully integrated into the Linux Kernel (version 2.6) ...
CST1215 Operating System Fundamentals
... 21. Identify the major components of an operating system and explain their functions individually, 22. Discuss the operating system features required for a particular target application, 23. Understand the various levels of system and application software, 24. Understand how design decisions in Oper ...
... 21. Identify the major components of an operating system and explain their functions individually, 22. Discuss the operating system features required for a particular target application, 23. Understand the various levels of system and application software, 24. Understand how design decisions in Oper ...
L03 - UMBC
... where # is the number of the Linux server to which you have connected. You may use any of the Linux servers: linux1, linux2 or linux3. ...
... where # is the number of the Linux server to which you have connected. You may use any of the Linux servers: linux1, linux2 or linux3. ...
PPT
... Linus Torvald, a student in Finland, extends an educational operating system Minix into an Unix style operating system for PCs (x86 machines) as a hobby In 1991, he posts to the comp.os.minix newsgroup an invitation for others to join him in developing this free, open source OS Different distributio ...
... Linus Torvald, a student in Finland, extends an educational operating system Minix into an Unix style operating system for PCs (x86 machines) as a hobby In 1991, he posts to the comp.os.minix newsgroup an invitation for others to join him in developing this free, open source OS Different distributio ...
D1S1_TSV404_Course_Intro_2011_v1
... ■ The information systems security office has areas that can be improved upon, especially C&A, RA and CP. ■ Embedding security into the SDLC is the best methodology NIST 80064R2 ■ Accountability is important from the system owner, to OIS, to the vendor implementing the controls ■ Standard reporting ...
... ■ The information systems security office has areas that can be improved upon, especially C&A, RA and CP. ■ Embedding security into the SDLC is the best methodology NIST 80064R2 ■ Accountability is important from the system owner, to OIS, to the vendor implementing the controls ■ Standard reporting ...
ppt
... • Rate monotonic: equivalent to any static algorithm • Earliest deadline first: equiv. to any dynamic alg. ...
... • Rate monotonic: equivalent to any static algorithm • Earliest deadline first: equiv. to any dynamic alg. ...
Chapter 8: Operating Systems and Utility Programs
... – Organizes and coordinates how multiple users access and share resources on a network. • Include Hardware, Software, data, and information • When not on network user uses their own operating system ...
... – Organizes and coordinates how multiple users access and share resources on a network. • Include Hardware, Software, data, and information • When not on network user uses their own operating system ...
Underlying computer system = hardware + software
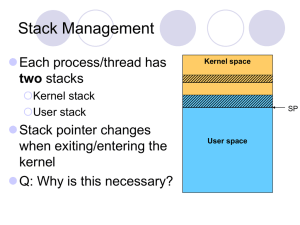
... z Processes can give up CPU when they don’t need it (e.g. waiting on I/O device) z ...
... z Processes can give up CPU when they don’t need it (e.g. waiting on I/O device) z ...
PDF
... In 1991, he posts to the comp.os.minix newsgroup an invitation for others to join him in developing this free, open source OS Different distributions package the same Linux kernel together with other various collections of open source software (GNU-Linux) Companies sell support or installation CDs, ...
... In 1991, he posts to the comp.os.minix newsgroup an invitation for others to join him in developing this free, open source OS Different distributions package the same Linux kernel together with other various collections of open source software (GNU-Linux) Companies sell support or installation CDs, ...
Operating System Design
... what is OS design like? • it‘s an engineering project rather than an exact science ...
... what is OS design like? • it‘s an engineering project rather than an exact science ...
Operating System Security Chapter 9 Operating System Security
... – Software developers often include these for easier development and testing – Can be used by developer for malicious purposes or discovered by an attacker – Defense is good formal testing of software ...
... – Software developers often include these for easier development and testing – Can be used by developer for malicious purposes or discovered by an attacker – Defense is good formal testing of software ...
Introduction to Windows NT/2000
... Every file in NTFS is described by one or more records in an array stored in a special file called the Master File Table (MFT). Each file on an NTFS volume has a unique ID called a file reference. 64-bit quantity that consists of a 48-bit file number and a 16-bit sequence number. Can be used to ...
... Every file in NTFS is described by one or more records in an array stored in a special file called the Master File Table (MFT). Each file on an NTFS volume has a unique ID called a file reference. 64-bit quantity that consists of a 48-bit file number and a 16-bit sequence number. Can be used to ...
UNIX Notes:
... UNIX has a directory structure that is tree-like with files containing all the information that is part of the system. Most people familiar with microcomputers and MSDOS are familiar with the tree-like directory structure with directories, sub-directories and pathnames. But in UNIX/Linux the directo ...
... UNIX has a directory structure that is tree-like with files containing all the information that is part of the system. Most people familiar with microcomputers and MSDOS are familiar with the tree-like directory structure with directories, sub-directories and pathnames. But in UNIX/Linux the directo ...