Lecture 16 - Suraj @ LUMS
... • Example: IDF virus modifies DOS service interrupt handler as follows: – Request for file length: return length of uninfected file – Request to open file: temporarily disinfect file, and reinfect on closing – Request to load file for execution: load infected file ...
... • Example: IDF virus modifies DOS service interrupt handler as follows: – Request for file length: return length of uninfected file – Request to open file: temporarily disinfect file, and reinfect on closing – Request to load file for execution: load infected file ...
Operating System
... One user One process running Limited memory management File services I/O services ...
... One user One process running Limited memory management File services I/O services ...
Introduction
... Operating System Concepts (6) - Files • Protection of files and directories, e.g. UNIX the rwx bits: 9 bits (owner/group/others) rwxr-xr-• File Descriptor: a number assigned to a file. • Mounting file systems. • Special files: block special files, character special files – standard input (fd=0), st ...
... Operating System Concepts (6) - Files • Protection of files and directories, e.g. UNIX the rwx bits: 9 bits (owner/group/others) rwxr-xr-• File Descriptor: a number assigned to a file. • Mounting file systems. • Special files: block special files, character special files – standard input (fd=0), st ...
CBA Software - Hoxie Public Schools
... other software to communicate with each other. There are many brands and versions of operating ...
... other software to communicate with each other. There are many brands and versions of operating ...
CL02_Operating_Systems
... The absolute path is a path that contains the root directory and all other subdirectories you need to access the file It points to the same location in the directory tree regardless of the current working ...
... The absolute path is a path that contains the root directory and all other subdirectories you need to access the file It points to the same location in the directory tree regardless of the current working ...
Summary for chapter 2 OPERATING SYSTEM nAJWA kNEFATI
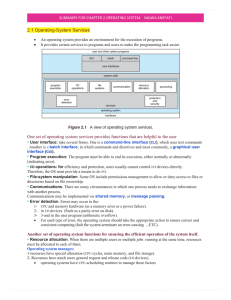
... One set of operating system services provides functions that are helpful to the user • User interface: take several forms. One is a command-line interface (CLI), which uses text commands . Another is a batch interface, in which commands and directives and most commonly, a graphical user interface (G ...
... One set of operating system services provides functions that are helpful to the user • User interface: take several forms. One is a command-line interface (CLI), which uses text commands . Another is a batch interface, in which commands and directives and most commonly, a graphical user interface (G ...
Unit 2 - NIST NACOL
... normally organized into directories to ease their use. Finally, when multiple users have access to files, it may be desirable to control by whom and in what ways files may be accessed. The operating system is responsible for the following activities in connection with file management: The creation ...
... normally organized into directories to ease their use. Finally, when multiple users have access to files, it may be desirable to control by whom and in what ways files may be accessed. The operating system is responsible for the following activities in connection with file management: The creation ...
chapter 5 – basic security
... data records. Example of data loss: sending a virus that reformats a computer hard drive. Example of data manipulation: breaking into a records system to change information, such as the price of an item. ...
... data records. Example of data loss: sending a virus that reformats a computer hard drive. Example of data manipulation: breaking into a records system to change information, such as the price of an item. ...
01-Intro
... From "PGP Freeware for MacOS, User's Guide" Version 6.5, Network Associates, Inc., www.pgp.com ...
... From "PGP Freeware for MacOS, User's Guide" Version 6.5, Network Associates, Inc., www.pgp.com ...
Linux Overview
... server and provides the server the capability to manage data, users, groups, security, applications, and other networking functions. • Real Time operating System: A real-time system is defined as a data processing system in which the time interval required to process and respond to inputs is so smal ...
... server and provides the server the capability to manage data, users, groups, security, applications, and other networking functions. • Real Time operating System: A real-time system is defined as a data processing system in which the time interval required to process and respond to inputs is so smal ...
Course Syllabus
... concepts as they are applied to memory, process, filesystem and I/O device management ...
... concepts as they are applied to memory, process, filesystem and I/O device management ...
Lecture1
... During past 25 years UNIX OS has evolved into a powerful, flexible and versatile OS. It works on Multi-Platform • PC’s, Micro-computers etc. ...
... During past 25 years UNIX OS has evolved into a powerful, flexible and versatile OS. It works on Multi-Platform • PC’s, Micro-computers etc. ...
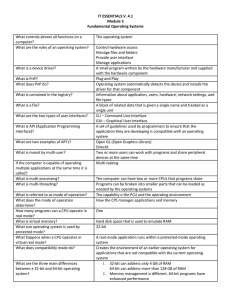
IT ESSENTIALS V. 4.1 Module 5 Fundamental Operating Systems
... Supports a single user Runs single-user applications Shares files and folders on a small network with limited security 1. Microsoft Windows 2. Apple Mac OS 3. Unix/Linux Unix Linus Torvalds The source code can be distributed and changed by anyone as a free download or from other developers 1. Suppor ...
... Supports a single user Runs single-user applications Shares files and folders on a small network with limited security 1. Microsoft Windows 2. Apple Mac OS 3. Unix/Linux Unix Linus Torvalds The source code can be distributed and changed by anyone as a free download or from other developers 1. Suppor ...
over view of operating system
... The system call interface invokes intended system call in OS kernel and returns status of the system call and any return values The caller need know nothing about how the system call is implemented Just needs to obey API and understand what OS will do as a result call Most details of OS inte ...
... The system call interface invokes intended system call in OS kernel and returns status of the system call and any return values The caller need know nothing about how the system call is implemented Just needs to obey API and understand what OS will do as a result call Most details of OS inte ...
Document
... remote files must be inserted in the local name space file names are only meaningful within the calling node but how do you refer to remote files in order to insert them? • globally unique file handles can be used to map remote files to local names ...
... remote files must be inserted in the local name space file names are only meaningful within the calling node but how do you refer to remote files in order to insert them? • globally unique file handles can be used to map remote files to local names ...
7.3.3. Computer System Structures
... maintaining all the important abstractions of the operating system, including such things as virtual memory, processes, device drivers, file systems, networking code. All the kernel code executes in privileged mode . the kernel is created as a single, monolithic binary • Monolithic Single Re ...
... maintaining all the important abstractions of the operating system, including such things as virtual memory, processes, device drivers, file systems, networking code. All the kernel code executes in privileged mode . the kernel is created as a single, monolithic binary • Monolithic Single Re ...
Import Settings:
... 28. Describe how Mac OS X is considered a hybrid system. 29. Describe how Android uses a unique virtual machine for running Java programs. True/False 30. KDE and GNOME desktops are available under open-source licenses. 31. Many operating system merge I/O devices and files into a combined file becaus ...
... 28. Describe how Mac OS X is considered a hybrid system. 29. Describe how Android uses a unique virtual machine for running Java programs. True/False 30. KDE and GNOME desktops are available under open-source licenses. 31. Many operating system merge I/O devices and files into a combined file becaus ...
William Stallings, Cryptography and Network Security 3/e
... TCP user on an inner host and one between itself and a TCP user on an outside host) ...
... TCP user on an inner host and one between itself and a TCP user on an outside host) ...
Using FPGAs to create a complete computer system Marcela Melara
... • Use polling to check status of I/O devices in these registers ...
... • Use polling to check status of I/O devices in these registers ...
Lecture 1: Operating System Services What is an Operating System?
... and the O.S. takes control of the computer system again, avoiding thus, that none program monopolizes the CPU. ...
... and the O.S. takes control of the computer system again, avoiding thus, that none program monopolizes the CPU. ...
Shawn Bracken - CISSP103 Chester StMenlo Park, CA 94025
... Member of the backline-utilities team in HP's response center supporting HP-UX. Supported HP-UX Trusted Systems secure accounting/auditing and kernel configuration Our team was the 3rd layer support known as "backline" which handled the more difficult and time-consuming calls. Most customers ...
... Member of the backline-utilities team in HP's response center supporting HP-UX. Supported HP-UX Trusted Systems secure accounting/auditing and kernel configuration Our team was the 3rd layer support known as "backline" which handled the more difficult and time-consuming calls. Most customers ...
Ch. 14 : UNIX Operating System with Linux
... Supports a wide range of devices including sound cards, graphics interfaces, networks, SCSI, etc. Supports a memory area reserved to buffer the input and output from different processes. Loads pages into memory only when they’re needed. Dynamic libraries are loaded only when they’re needed & their c ...
... Supports a wide range of devices including sound cards, graphics interfaces, networks, SCSI, etc. Supports a memory area reserved to buffer the input and output from different processes. Loads pages into memory only when they’re needed. Dynamic libraries are loaded only when they’re needed & their c ...