Lecture 2
... Program design philosophy: 1. Arrange each program to perform a single function. 2. Avoid extraneous output, another program might use it as input. 3. If possible, use or modify existing tools rather write a new one. 4. Create the design first, then start with a small prototype and add features incr ...
... Program design philosophy: 1. Arrange each program to perform a single function. 2. Avoid extraneous output, another program might use it as input. 3. If possible, use or modify existing tools rather write a new one. 4. Create the design first, then start with a small prototype and add features incr ...
Operating Systems
... – When control was passed to a user – User program and data loaded – Clock generates interrupts about every 0.2 sec – At each interrupt OS gained control and could assign processor to another user ...
... – When control was passed to a user – User program and data loaded – Clock generates interrupts about every 0.2 sec – At each interrupt OS gained control and could assign processor to another user ...
Chapter 1 Operating System Fundamentals
... a client/server relationship. • A server offers network services, such as e-mail to other programs called clients. • Once enabled, a server program waits to receive requests from client programs. If a legitimate request is received, the server responds by sending the appropriate information back to ...
... a client/server relationship. • A server offers network services, such as e-mail to other programs called clients. • Once enabled, a server program waits to receive requests from client programs. If a legitimate request is received, the server responds by sending the appropriate information back to ...
ComputersandFiles
... directly with Microsoft. Apple makes Macintosh computers, ibooks, G5 computers, etc… OS X will not run on a regular PC, it will work only on Apple made computers. Windows will not work on an Apple machine. ...
... directly with Microsoft. Apple makes Macintosh computers, ibooks, G5 computers, etc… OS X will not run on a regular PC, it will work only on Apple made computers. Windows will not work on an Apple machine. ...
Operating System Software The OS
... your kitchen doesn't need an operating system. The computer in a microwave oven simply runs a single program all the time. ...
... your kitchen doesn't need an operating system. The computer in a microwave oven simply runs a single program all the time. ...
Operating Software
... 5. A performance monitor is a program that accesses and reports information about various system resources and devices. The information in such reports can help a user identify problems with resources. 6. Administering Security - Most multiuser operating systems require each user to log on. Both suc ...
... 5. A performance monitor is a program that accesses and reports information about various system resources and devices. The information in such reports can help a user identify problems with resources. 6. Administering Security - Most multiuser operating systems require each user to log on. Both suc ...
doc
... An operating system is a collection of programs that manage computer resources, provides a user interface, and runs applications. Computer resources include memory, processing, storage, input & output devices. The OS also monitors system performance, schedules jobs, and provides some security for th ...
... An operating system is a collection of programs that manage computer resources, provides a user interface, and runs applications. Computer resources include memory, processing, storage, input & output devices. The OS also monitors system performance, schedules jobs, and provides some security for th ...
TH1. Applications and programming languages AND Operating
... This isn't just about running more than one application at the same time. Multi-tasking allows multiple tasks to run concurrently, taking turns using the resources of the computer. This can mean running a couple of applications, sending a document to the printer and downloading a web page. Multi-acc ...
... This isn't just about running more than one application at the same time. Multi-tasking allows multiple tasks to run concurrently, taking turns using the resources of the computer. This can mean running a couple of applications, sending a document to the printer and downloading a web page. Multi-acc ...
group policy - University Of Worcester
... To assist users with responsible user of network resources, all aspects of user activity need to be audited or at least monitored monitored: use of alerts to flag abnormal events e.g. attempted illegal access audited: details of user activity and effects written to a .log text file ...
... To assist users with responsible user of network resources, all aspects of user activity need to be audited or at least monitored monitored: use of alerts to flag abnormal events e.g. attempted illegal access audited: details of user activity and effects written to a .log text file ...
Module 3: Operating
... The program that reads and interprets control statements is called variously: control-card interpreter command-line interpreter shell (in UNIX) ...
... The program that reads and interprets control statements is called variously: control-card interpreter command-line interpreter shell (in UNIX) ...
CS423/523
... – Allows multiple processes to share resources of processor fairly – Does this by scheduling processes to get execution time • User Processes • Microsoft Word, Foxfire or Skype • System Processes: • Print spooler, network connections, security accounts manager ... plus many others ...
... – Allows multiple processes to share resources of processor fairly – Does this by scheduling processes to get execution time • User Processes • Microsoft Word, Foxfire or Skype • System Processes: • Print spooler, network connections, security accounts manager ... plus many others ...
Chorusamoeba
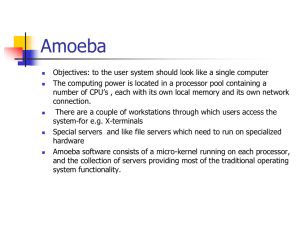
... Objectives: to the user system should look like a single computer The computing power is located in a processor pool containing a number of CPU’s , each with its own local memory and its own network connection. There are a couple of workstations through which users access the system-for e.g. X-termi ...
... Objectives: to the user system should look like a single computer The computing power is located in a processor pool containing a number of CPU’s , each with its own local memory and its own network connection. There are a couple of workstations through which users access the system-for e.g. X-termi ...
[intro.pptx]
... A simple module (or “component”) • A set of procedures/functions/methods. • An interface (API) that defines a template for how to call/invoke the procedures. • State is just data maintained and accessed by the procedures. • A module may be a class that defines a template (type) for a data structure ...
... A simple module (or “component”) • A set of procedures/functions/methods. • An interface (API) that defines a template for how to call/invoke the procedures. • State is just data maintained and accessed by the procedures. • A module may be a class that defines a template (type) for a data structure ...
Fall 2008 Term - Computer Science
... phones, watches, and Ipods). Although there are variations (different versions) of Unix, each provides fundamentally the same set of commands and tools. 4. Many variations of UNIX are open source. Thus, you can obtain the actual source code for the operating system and see exactly how it works. If f ...
... phones, watches, and Ipods). Although there are variations (different versions) of Unix, each provides fundamentally the same set of commands and tools. 4. Many variations of UNIX are open source. Thus, you can obtain the actual source code for the operating system and see exactly how it works. If f ...
CS 291 – Dynamic Web Prog. With PHP
... the system is provided When the operating system finishes the execution of one command, it seeks the next “control statement” from the user’s keyboard. On-line system must be available for users to access data and code. ...
... the system is provided When the operating system finishes the execution of one command, it seeks the next “control statement” from the user’s keyboard. On-line system must be available for users to access data and code. ...
QUIZ1
... 8. Discuss what CPU must do (a) when the current process exits it, (b) when it has to respond to an interrupt, or (c) the triggering event is a trap. 9. An OS could appear in different architectural modes like monolithic, layered, objected oriented and as a micro-kernel. Indicate their basic design ...
... 8. Discuss what CPU must do (a) when the current process exits it, (b) when it has to respond to an interrupt, or (c) the triggering event is a trap. 9. An OS could appear in different architectural modes like monolithic, layered, objected oriented and as a micro-kernel. Indicate their basic design ...
Sai Uday Kiran Ravi`s presentation on Application Security on
... when the operating system is malicious is challenging. Even if the OS behaves correctly, a buggy application might expose its own sensitive data (e.g. via a buffer overflow). Problem must be ensuring that applications continue to run normally (or fail-stop) even if the OS behaves maliciously, ra ...
... when the operating system is malicious is challenging. Even if the OS behaves correctly, a buggy application might expose its own sensitive data (e.g. via a buffer overflow). Problem must be ensuring that applications continue to run normally (or fail-stop) even if the OS behaves maliciously, ra ...
chapter 4
... Each time a new task is assigned to the machine, the scheduler creates a process for that task by placing a new entry in the process table The entry contains such information as - The memory area assigned to the process(obtained from the memory manager) , the priority of the process, and whether ...
... Each time a new task is assigned to the machine, the scheduler creates a process for that task by placing a new entry in the process table The entry contains such information as - The memory area assigned to the process(obtained from the memory manager) , the priority of the process, and whether ...
CCN2273 Operating Systems
... Virtual memory; Paging and segmentation system; Secondary storage allocation; Directory and file system structure. Protection and Security Protection and access control; Capabilities; Security and cryptography. Case Studies on Operating Systems Structure of UNIX, Linux, Mac OS, Microsoft Windows, et ...
... Virtual memory; Paging and segmentation system; Secondary storage allocation; Directory and file system structure. Protection and Security Protection and access control; Capabilities; Security and cryptography. Case Studies on Operating Systems Structure of UNIX, Linux, Mac OS, Microsoft Windows, et ...












![[intro.pptx]](http://s1.studyres.com/store/data/000013153_1-8c71297723930f81fc51edc276eba587-300x300.png)