What is an Operating System?
... On the desktop, CPUs are now cheap enough to have multiprocessor PCs. Really good for a crisp responsive user interface. Multi-core CPUs will be common soon. ...
... On the desktop, CPUs are now cheap enough to have multiprocessor PCs. Really good for a crisp responsive user interface. Multi-core CPUs will be common soon. ...
Lecture 6
... • The system call interface invokes the intended system call in OS kernel and returns status of the system call and any return values • The caller need know nothing about how the system call is implemented – Just needs to obey API and understand what OS will do as a result call – Most details of OS ...
... • The system call interface invokes the intended system call in OS kernel and returns status of the system call and any return values • The caller need know nothing about how the system call is implemented – Just needs to obey API and understand what OS will do as a result call – Most details of OS ...
lesson12
... somewhere other than on the mass storage devices supporting your database, usually on some type of tape media. – You can also store a backup on a hard drive on another computer connected over a local area network (LAN). ...
... somewhere other than on the mass storage devices supporting your database, usually on some type of tape media. – You can also store a backup on a hard drive on another computer connected over a local area network (LAN). ...
Course Overview, History
... – Huge, parallel, very expensive, not understood • Windows NT/XP: 10 years, 1000s of people, … ...
... – Huge, parallel, very expensive, not understood • Windows NT/XP: 10 years, 1000s of people, … ...
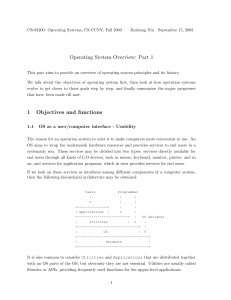
Operating System Overview: Part 1 1 Objectives and functions
... With it, users don’t have direct access to the computer systems any longer; instead, the operator of the system collects the user programs and batches them together sequentially for use by the monitor. To process user programs, the monitor first has to be loaded into memory. Then it reads in program ...
... With it, users don’t have direct access to the computer systems any longer; instead, the operator of the system collects the user programs and batches them together sequentially for use by the monitor. To process user programs, the monitor first has to be loaded into memory. Then it reads in program ...
course syllabus
... By the end of the semester, students in this course would have developed their own basic functions of an operating system through the completion of a series of laboratory assignment. The lectures will help to familiarize students with the main concepts of an operating system. Technical Requirements: ...
... By the end of the semester, students in this course would have developed their own basic functions of an operating system through the completion of a series of laboratory assignment. The lectures will help to familiarize students with the main concepts of an operating system. Technical Requirements: ...
Lec01b-OS Overview
... • No universally accepted definition • “Everything a vendor ships when you order an operating system” is a good approximation – But varies wildly ...
... • No universally accepted definition • “Everything a vendor ships when you order an operating system” is a good approximation – But varies wildly ...
CIS162AB
... Create a method and add the code to check if the data has been saved in the form closing method. After writing this method to handle the FormClosing event, its needs to be assigned as the form's FormClosing event handler while in Design Mode. After assigning it to the form, the method is automatical ...
... Create a method and add the code to check if the data has been saved in the form closing method. After writing this method to handle the FormClosing event, its needs to be assigned as the form's FormClosing event handler while in Design Mode. After assigning it to the form, the method is automatical ...
operating system
... • OS is written as collection of procedures. Each of which can call any of the other ones whenever it needs to. • To construct the OS one first compiles all the individual procedures and then binds them all together into a single object file using the system linker. • This organization suggests a ba ...
... • OS is written as collection of procedures. Each of which can call any of the other ones whenever it needs to. • To construct the OS one first compiles all the individual procedures and then binds them all together into a single object file using the system linker. • This organization suggests a ba ...
Dan A CSC 345 Term Paper
... means that applications that request to access a resource must go through a security policy administrator to do so. This prevents applications from gaining access to more than they are supposed to. Much like their computer brethren, mobile operating systems must use some sort of file and memory prot ...
... means that applications that request to access a resource must go through a security policy administrator to do so. This prevents applications from gaining access to more than they are supposed to. Much like their computer brethren, mobile operating systems must use some sort of file and memory prot ...
Chapter 9 Linux Installation Procedures
... • RPM is the most popular type of package. • It provides the necessary tools such as package databases that are needed to install and remove programs, however, not all applications or programs use RPM. • The difference between Debian and RPM packages is that they are not interchangeable. • Debian co ...
... • RPM is the most popular type of package. • It provides the necessary tools such as package databases that are needed to install and remove programs, however, not all applications or programs use RPM. • The difference between Debian and RPM packages is that they are not interchangeable. • Debian co ...
Security
... Antivirus and Anti-Antivirus Techniques • A goat file is a program that does nothing but is infected by a virus. • Use goat file to create the profile of a virus and insert it into the virus database. • Virus scanners scan every executable file or some specific types of files to locate the virus. • ...
... Antivirus and Anti-Antivirus Techniques • A goat file is a program that does nothing but is infected by a virus. • Use goat file to create the profile of a virus and insert it into the virus database. • Virus scanners scan every executable file or some specific types of files to locate the virus. • ...
Operating Systems - KSU Web Home
... abstractions, and other utilities to monitor the state of the computer system. The system software forms an environment for the programmers to develop and execute their programs (collectively known as application software). Three types of users can be identified: system programmers, application prog ...
... abstractions, and other utilities to monitor the state of the computer system. The system software forms an environment for the programmers to develop and execute their programs (collectively known as application software). Three types of users can be identified: system programmers, application prog ...
Chapter 5 - Department of Computer Science and Information Systems
... controlling who and what has access to the ecommerce server Operating systems often provide access control list security to restrict file access to selected users Users identify themselves using either a password or a token An access control list (ACL) is a list or database of people who can access ...
... controlling who and what has access to the ecommerce server Operating systems often provide access control list security to restrict file access to selected users Users identify themselves using either a password or a token An access control list (ACL) is a list or database of people who can access ...
Final Exam 2004 PowerPoint
... • Rules to keep in mind: – NTFS object permissions always apply, no matter if the accessing user is local or remote – NTFS object permissions are cumulative – NTFS file permissions override any contradictory settings on the parent or container folder – Deny overrides all other specific Allows – When ...
... • Rules to keep in mind: – NTFS object permissions always apply, no matter if the accessing user is local or remote – NTFS object permissions are cumulative – NTFS file permissions override any contradictory settings on the parent or container folder – Deny overrides all other specific Allows – When ...
Operating Systems and File Management Learning Steps LAP CC
... examples of file management utilities provided by operating systems. f) These utilities allow you to find, rename, copy, move, and delete files and folders. In addition they allow you to perform file management activities with more than one file at a time. The way that data is actually stored is ref ...
... examples of file management utilities provided by operating systems. f) These utilities allow you to find, rename, copy, move, and delete files and folders. In addition they allow you to perform file management activities with more than one file at a time. The way that data is actually stored is ref ...
Transparency in Distributed Systems
... due to heterogeneity of the network components and mainly due to the extensive use of the Internet services. For instance a company may have many branches operating at different geographical locations and may need to interact with all other branches for dayto-day activities. This gives rise to Distr ...
... due to heterogeneity of the network components and mainly due to the extensive use of the Internet services. For instance a company may have many branches operating at different geographical locations and may need to interact with all other branches for dayto-day activities. This gives rise to Distr ...
Background: Operating Systems
... for each pathname component start read of directory from disk sleep waiting for disk read ...
... for each pathname component start read of directory from disk sleep waiting for disk read ...
Why Study OS?
... Layout by compiler Allocate/deallocate by process creation (fork) and termination Names are relative off of stack pointer and entirely local Linker and loader say the starting address Allocate/deallocate by library calls such as malloc() and free() Application program use the library calls to manage ...
... Layout by compiler Allocate/deallocate by process creation (fork) and termination Names are relative off of stack pointer and entirely local Linker and loader say the starting address Allocate/deallocate by library calls such as malloc() and free() Application program use the library calls to manage ...
Operating System Concepts, Terminology, and History
... Operating System Concepts • For purposes of this book, we'll consider an operating system to be the supporting software structure on which application programs run. – This support structure includes the facilities to manage the computer system's resources and any utility programs needed to maintain ...
... Operating System Concepts • For purposes of this book, we'll consider an operating system to be the supporting software structure on which application programs run. – This support structure includes the facilities to manage the computer system's resources and any utility programs needed to maintain ...