Why we need IT security - Department of Computer Science and
... – Inspect all inbound and outbound internet messages (Uses packet filtering to distinguish between legitimate messages that are responses to valid user activity and illegitimate messages that are unsolicited). Makes its decisions based on message source address, destination address and requested por ...
... – Inspect all inbound and outbound internet messages (Uses packet filtering to distinguish between legitimate messages that are responses to valid user activity and illegitimate messages that are unsolicited). Makes its decisions based on message source address, destination address and requested por ...
10-Software-Presentation
... which manages the computer and the peripherals attached to it The functions of an OS are: Provide a Human Computer Interface Handle Input and Output File Management Memory management ...
... which manages the computer and the peripherals attached to it The functions of an OS are: Provide a Human Computer Interface Handle Input and Output File Management Memory management ...
Top Five Current Operating System Issues
... without being warned. Sure, you may never have a security threat, but the fact that you could hardly use your own computer was a little embarrassing. On the other side, Apple’s newest edition of OS X, a system known and praised for its ease of use along with the majority of independent Unix-based op ...
... without being warned. Sure, you may never have a security threat, but the fact that you could hardly use your own computer was a little embarrassing. On the other side, Apple’s newest edition of OS X, a system known and praised for its ease of use along with the majority of independent Unix-based op ...
basic-os-concepts
... 2. Operating system – controls and coordinates the use of the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, video game ...
... 2. Operating system – controls and coordinates the use of the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, video game ...
CS 550 Operating Systems - James Madison University
... structure data (both in memory and in storage devices) as a first step to finding the data. The key to this search is metadata. This course will prepare you for later work in digital forensics by addressing a number of interesting questions: What can we learn by examining the metadata of modern file ...
... structure data (both in memory and in storage devices) as a first step to finding the data. The key to this search is metadata. This course will prepare you for later work in digital forensics by addressing a number of interesting questions: What can we learn by examining the metadata of modern file ...
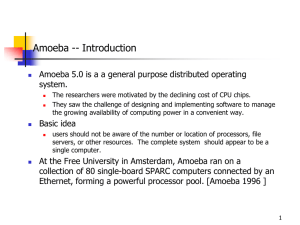
Chorusamoeba
... 2. Processor pool: users just have terminals. 3. Integrated: heterogeneous network of machines that may perform both the role of server and the role of application processor. Amoeba is an example of a hybrid system that combines characteristics of the first two models. Highly interactive or graphica ...
... 2. Processor pool: users just have terminals. 3. Integrated: heterogeneous network of machines that may perform both the role of server and the role of application processor. Amoeba is an example of a hybrid system that combines characteristics of the first two models. Highly interactive or graphica ...
Phoenix SIEM (Security Information and Event
... • Comprehensive logging of activity for offline analysis and forensics. • Port-independent analysis of application-layer protocols. • Support for many application-layer protocols (including DNS, FTP, HTTP, IRC, SMTP, SSH, SSL, SMB). • Analysis of file content exchanged over application-layer protoco ...
... • Comprehensive logging of activity for offline analysis and forensics. • Port-independent analysis of application-layer protocols. • Support for many application-layer protocols (including DNS, FTP, HTTP, IRC, SMTP, SSH, SSL, SMB). • Analysis of file content exchanged over application-layer protoco ...
Intro to Operating Systems
... This was open source which led to other versions: System V (AT&T) and BSD (Berkeley Software Distribution) ...
... This was open source which led to other versions: System V (AT&T) and BSD (Berkeley Software Distribution) ...
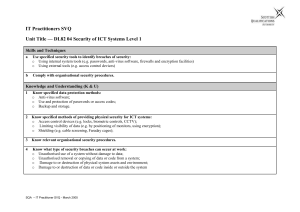
it user svq – level 2
... Know what type of security breaches can occur at work: o Unauthorised use of a system without damage to data; o Unauthorised removal or copying of data or code from a system; o Damage to or destruction of physical system assets and environment; o Damage to or destruction of data or code inside or ou ...
... Know what type of security breaches can occur at work: o Unauthorised use of a system without damage to data; o Unauthorised removal or copying of data or code from a system; o Damage to or destruction of physical system assets and environment; o Damage to or destruction of data or code inside or ou ...
Week 9a - cda college
... Memory manager, Processor Manager, Device manager and File manager. Each of the processor must perform the following tasks ...
... Memory manager, Processor Manager, Device manager and File manager. Each of the processor must perform the following tasks ...
Support: Ticket, Process, and Expectations
... the hard disk will show up just like another hard disk when connected and unlocked via the password). Tutorial available at http://www.trucrypt.org/docs/?s=tutorial Great approach for home computers as it provides a location for all work files to be placed in an encrypted "drive" and when the comp ...
... the hard disk will show up just like another hard disk when connected and unlocked via the password). Tutorial available at http://www.trucrypt.org/docs/?s=tutorial Great approach for home computers as it provides a location for all work files to be placed in an encrypted "drive" and when the comp ...
Operating System organization
... Operating System Organizations • The literature in operating systems is full of papers of simple, elegant systems like this one • Simple • Easy to build and maintain by small teams • Very instructive for study ...
... Operating System Organizations • The literature in operating systems is full of papers of simple, elegant systems like this one • Simple • Easy to build and maintain by small teams • Very instructive for study ...
Layer 1 Process Management
... •Each file system begins with a boot block. •The super block contains information describing the layout of the file system. •The disk storage can be allocated in units of 1,2,4,8 or in general 2n, blocks. •The idea behind the zone is to help ensure that disk blocks that belong to the same file are l ...
... •Each file system begins with a boot block. •The super block contains information describing the layout of the file system. •The disk storage can be allocated in units of 1,2,4,8 or in general 2n, blocks. •The idea behind the zone is to help ensure that disk blocks that belong to the same file are l ...
Test 1 Operating Systems and Networking CS
... I/O devices.” Is this a sufficient claim for a start as far as memory is concerned? Elaborate your answer. If processes within a system communicated via message passing without using shared memory, would we still insist on it? State your reason. Consider the following diagram that purports to depict ...
... I/O devices.” Is this a sufficient claim for a start as far as memory is concerned? Elaborate your answer. If processes within a system communicated via message passing without using shared memory, would we still insist on it? State your reason. Consider the following diagram that purports to depict ...
Lec.4.Communication software and the internet
... • There are a number of procedures companies and persons can take to protect their information. ...
... • There are a number of procedures companies and persons can take to protect their information. ...
Chapter04
... the fullest extent. The second type is known as a hotfix. A hotfix does not typically address security issues. Instead, it addressed a specific problem in software, such as a feature that does not work properly. Once all of the service packs have been installed on a new system then any hotfixes shou ...
... the fullest extent. The second type is known as a hotfix. A hotfix does not typically address security issues. Instead, it addressed a specific problem in software, such as a feature that does not work properly. Once all of the service packs have been installed on a new system then any hotfixes shou ...
Lecture 1 - Concepts of the UNIX Operating System
... 1. Many UNIX commands (called filters) possess an unusual property in that the output of one command can be connected to the input of another. In this way, pipelines of two or more commands can be set up to handle complex text manipulation tasks. You can’t have a pipeline of interactive commands. 2. ...
... 1. Many UNIX commands (called filters) possess an unusual property in that the output of one command can be connected to the input of another. In this way, pipelines of two or more commands can be set up to handle complex text manipulation tasks. You can’t have a pipeline of interactive commands. 2. ...
PPT 02 - Mesa Community College
... the mouse, keyboard, video display card, printer, scanner, and USB ports. ...
... the mouse, keyboard, video display card, printer, scanner, and USB ports. ...
Operating Systems 1
... History of operating system The computer is forced to execute tasks under a deadline, a process that became known as real-time processing in which the actions performed are said to occur in realtime.(Play game, real time processing)) If interactive system had been required to serve only one user ...
... History of operating system The computer is forced to execute tasks under a deadline, a process that became known as real-time processing in which the actions performed are said to occur in realtime.(Play game, real time processing)) If interactive system had been required to serve only one user ...
Slide 1
... storage, all tied together by a local network. Generally speaking, such a system will have most of the following characteristics that distinguish it from a distributed system: • Each computer has its own private operating system, instead of running part of a global, systemwide operating system. • Ea ...
... storage, all tied together by a local network. Generally speaking, such a system will have most of the following characteristics that distinguish it from a distributed system: • Each computer has its own private operating system, instead of running part of a global, systemwide operating system. • Ea ...
B.Sc. FOOTWEAR TECHNOLOGY (BSCFWT) Term
... Attempt any eight questions from Section A. Section B is compulsory. ...
... Attempt any eight questions from Section A. Section B is compulsory. ...