CS 471-001: Operating Systems Spring 2017 Department of
... Show an understanding of the need for the concurrent operation of multiple tasks (processes/threads) and an ability to solve basic process synchronization problems that arise from concurrent operation settings ...
... Show an understanding of the need for the concurrent operation of multiple tasks (processes/threads) and an ability to solve basic process synchronization problems that arise from concurrent operation settings ...
Security at the Operating System Level (Microsoft)
... - Allows system administrators to set global or very specific file access permissions. - Sets up a virtual root directory to prevent network users from accessing higher nodes in the system. ...
... - Allows system administrators to set global or very specific file access permissions. - Sets up a virtual root directory to prevent network users from accessing higher nodes in the system. ...
operating system
... An operating system is software installed on the computer to make it possible to use it without needing a degree in electronic engineering ...
... An operating system is software installed on the computer to make it possible to use it without needing a degree in electronic engineering ...
Chapter 16 PowerPoint
... File and directory names can be up to eight characters long, followed by a period and a three-character extension. Some universal extensions are .exe, .com, .sys, .bat, .txt, .doc, and .drv. File and directory names are not casesensitive. ...
... File and directory names can be up to eight characters long, followed by a period and a three-character extension. Some universal extensions are .exe, .com, .sys, .bat, .txt, .doc, and .drv. File and directory names are not casesensitive. ...
01- introduction
... – Referee: ensure responsiveness when multiple tabs are opened at the same time – Illusionist: web services are geographically distributed for fault tolerance and performance. Mask server failures to the users. – Glue: how does a browser achieve portable execution of scripts across different OS and ...
... – Referee: ensure responsiveness when multiple tabs are opened at the same time – Illusionist: web services are geographically distributed for fault tolerance and performance. Mask server failures to the users. – Glue: how does a browser achieve portable execution of scripts across different OS and ...
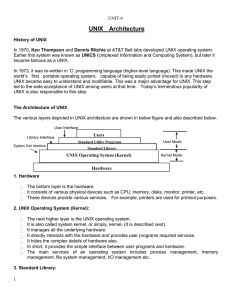
The Unix Philosophy
... job which creates other jobs such as scheduling tasks, etc). Running many processes at the same time can allow many users to connect to and use the computer resources at the same time (This concept is referred to as "multitasking"). The Unix file system allows users to share or restrict access to th ...
... job which creates other jobs such as scheduling tasks, etc). Running many processes at the same time can allow many users to connect to and use the computer resources at the same time (This concept is referred to as "multitasking"). The Unix file system allows users to share or restrict access to th ...
system programs
... and ready-to-install packages of common Unix tools. The first distributions managed these packages by simply providing a means of unpacking all the files into the appropriate places; modern distributions include advanced package management and automated installation. ...
... and ready-to-install packages of common Unix tools. The first distributions managed these packages by simply providing a means of unpacking all the files into the appropriate places; modern distributions include advanced package management and automated installation. ...
Network Security Overview
... system or application being attacked. Another form of access attacks involves privilege escalation. This is done by legitimate users who have a lower level of access privileges or intruders who have gained lower-privileged access. The intent is to get information or execute procedures that are unaut ...
... system or application being attacked. Another form of access attacks involves privilege escalation. This is done by legitimate users who have a lower level of access privileges or intruders who have gained lower-privileged access. The intent is to get information or execute procedures that are unaut ...
Linux Systems Programming I
... 13. identify bitwise, unary and binary scope resolution, and conditional operators; 14. use the new and delete operators to implement a singly linked list; 15. be proficient in using UNIX tools; 16. know about the Linux variant of UNIX; 17. have a working knowledge of enhanced UNIX shells; 18. be ab ...
... 13. identify bitwise, unary and binary scope resolution, and conditional operators; 14. use the new and delete operators to implement a singly linked list; 15. be proficient in using UNIX tools; 16. know about the Linux variant of UNIX; 17. have a working knowledge of enhanced UNIX shells; 18. be ab ...
Operating System
... In UNIX, every thing is either a file or a process. A file is a collection of data. They are used to store large amount of information permanently. Directories are considered as files. In addition, physical devices are also considered as files in UNIX. A process is a program in execution. A ...
... In UNIX, every thing is either a file or a process. A file is a collection of data. They are used to store large amount of information permanently. Directories are considered as files. In addition, physical devices are also considered as files in UNIX. A process is a program in execution. A ...
OS Concepts - UCL Computer Science
... – Don’t want to rewrite apps for each new CPU, each new I/O device ...
... – Don’t want to rewrite apps for each new CPU, each new I/O device ...
Presentation
... Crack- (1) To break into a computer system. The term was coined in the mid-80s by hackers who wanted to differentiate themselves from individuals whose sole purpose is to sneak through security systems. Whereas crackers sole aim is to break into secure systems, hackers are more interested in gaini ...
... Crack- (1) To break into a computer system. The term was coined in the mid-80s by hackers who wanted to differentiate themselves from individuals whose sole purpose is to sneak through security systems. Whereas crackers sole aim is to break into secure systems, hackers are more interested in gaini ...
Operating Systems
... •An operating system (OS) is a software program that manages the hardware and software resources of a computer. •An Operating System is the basic minimum software that is needed for a computer to be operational -Examples of operating systems for personal computers include Microsoft Windows, Mac OS, ...
... •An operating system (OS) is a software program that manages the hardware and software resources of a computer. •An Operating System is the basic minimum software that is needed for a computer to be operational -Examples of operating systems for personal computers include Microsoft Windows, Mac OS, ...
Module 3: Operating
... into memory and to run it. I/O operations – since user programs cannot execute I/O operations directly, the operating system must provide some means to perform I/O. File-system manipulation – program capability to read, write, create, and delete files. Communications – exchange of information ...
... into memory and to run it. I/O operations – since user programs cannot execute I/O operations directly, the operating system must provide some means to perform I/O. File-system manipulation – program capability to read, write, create, and delete files. Communications – exchange of information ...
Operating System
... information • UNIX: –Can be used on many computer system types and platforms • Red Hat Linux: –Can manage a cluster of up to eight servers • Mac OS X Server: ...
... information • UNIX: –Can be used on many computer system types and platforms • Red Hat Linux: –Can manage a cluster of up to eight servers • Mac OS X Server: ...
Linux
... • /mnt : Mount points. When you temporarily load the contents of a CD-ROM or USB drive, you typically use a special name under /mnt. For example, many distributions (including Fedora) come, by default, with the directory /mnt/cdrom, which is where your CDROM drive's contents are made accessible. • / ...
... • /mnt : Mount points. When you temporarily load the contents of a CD-ROM or USB drive, you typically use a special name under /mnt. For example, many distributions (including Fedora) come, by default, with the directory /mnt/cdrom, which is where your CDROM drive's contents are made accessible. • / ...
Networked communities - Ar
... the kernel, or placed in a file like /etc/hostname. Solaris adds to the multiplicity by also maintaining the install name in /etc/hostname.le0 or an equivalent file for the appropriate network interface, together with several files in /etc/net/*/hosts. • Application level name: Any name used by appl ...
... the kernel, or placed in a file like /etc/hostname. Solaris adds to the multiplicity by also maintaining the install name in /etc/hostname.le0 or an equivalent file for the appropriate network interface, together with several files in /etc/net/*/hosts. • Application level name: Any name used by appl ...
ITS 225 (Operating Systems) Lecture Notes
... If nothing is happening (no programs are ready to run, no IO devices are waiting for service, and no users are making requests), then the system sits idle, waiting for an event. Events are signaled by interrupts. • Hardware interrupts: usually triggered when a device enables a line on the system bus ...
... If nothing is happening (no programs are ready to run, no IO devices are waiting for service, and no users are making requests), then the system sits idle, waiting for an event. Events are signaled by interrupts. • Hardware interrupts: usually triggered when a device enables a line on the system bus ...
Training
... • C, D, E, F (25% - 60%) • Average of this class should be either B- or C+. • To pass this subject, the final exam should be >= 30. • To pass this subject, the overall score should be >= 35. • To get the “A” grade, the overall score should be at least 68. • Each person, each semester can have one su ...
... • C, D, E, F (25% - 60%) • Average of this class should be either B- or C+. • To pass this subject, the final exam should be >= 30. • To pass this subject, the overall score should be >= 35. • To get the “A” grade, the overall score should be at least 68. • Each person, each semester can have one su ...
Slide 1
... • OS components that are stored permanently on chip (ROM) and not on the disk drive • When a computer is powered-on, firmware is the first program that it always executes • Firmware consists of startup and a few low-level I/O routines that assist the computer in finding ...
... • OS components that are stored permanently on chip (ROM) and not on the disk drive • When a computer is powered-on, firmware is the first program that it always executes • Firmware consists of startup and a few low-level I/O routines that assist the computer in finding ...