Operating System
... This course introduces the fundamentals of operating systems. Topics include interprocess communication, process scheduling, deadlock, memory management, virtual memory, and file system. Formal principles are illustrated with examples and case studies of one or more contemporary operating system. ...
... This course introduces the fundamentals of operating systems. Topics include interprocess communication, process scheduling, deadlock, memory management, virtual memory, and file system. Formal principles are illustrated with examples and case studies of one or more contemporary operating system. ...
Chapter 2
... and execution. Some of them are simply user interfaces to system calls; others are considerably more complex ...
... and execution. Some of them are simply user interfaces to system calls; others are considerably more complex ...
UNIX Notes:
... UNIX has a directory structure that is tree-like with files containing all the information that is part of the system. Most people familiar with microcomputers and MSDOS are familiar with the tree-like directory structure with directories, sub-directories and pathnames. But in UNIX/Linux the directo ...
... UNIX has a directory structure that is tree-like with files containing all the information that is part of the system. Most people familiar with microcomputers and MSDOS are familiar with the tree-like directory structure with directories, sub-directories and pathnames. But in UNIX/Linux the directo ...
UNIX Software Tools
... an email system) the software on the local host is the client and the software on the remote host is the server. In a X-Windows system this is reversed. The X-Windows server is on your local machine. It provides the following services: keyboard input, mouse, procedures for drawing on the screen, ...
... an email system) the software on the local host is the client and the software on the remote host is the server. In a X-Windows system this is reversed. The X-Windows server is on your local machine. It provides the following services: keyboard input, mouse, procedures for drawing on the screen, ...
2. Operating System Structure
... The shell then either waits for the process to finish or runs the process in the background. In background, the shell immediately requests another command. The user is free to ask the shell to run other programs. When the process is done, it executes an exit() system call to terminate. exit() retur ...
... The shell then either waits for the process to finish or runs the process in the background. In background, the shell immediately requests another command. The user is free to ask the shell to run other programs. When the process is done, it executes an exit() system call to terminate. exit() retur ...
ppt - Stanford Crypto group
... – Typically, a root process uses system call to determine if initiating user has permission to a particular file, e.g. /tmp/X. – After access is authorized and before the file open, user may change the file /tmp/X to a symbolic link to a target file /etc/shadow. ...
... – Typically, a root process uses system call to determine if initiating user has permission to a particular file, e.g. /tmp/X. – After access is authorized and before the file open, user may change the file /tmp/X to a symbolic link to a target file /etc/shadow. ...
Principles of Operating System
... • Processor time is shared among multiple users • Multiple users simultaneously access the system through terminals, with the OS interleaving the execution of each user program in a short burst or quantum of computation ...
... • Processor time is shared among multiple users • Multiple users simultaneously access the system through terminals, with the OS interleaving the execution of each user program in a short burst or quantum of computation ...
OS Concepts - UCL Computer Science
... – Don’t want to rewrite apps for each new CPU, each new I/O device ...
... – Don’t want to rewrite apps for each new CPU, each new I/O device ...
presentation6
... Login information is encrypted by default All remote connections can be audited ...
... Login information is encrypted by default All remote connections can be audited ...
Computers
... A page table is an index to the current location of a page. Access can be Swapped Page Segmentation (hierarchical) Hashed ...
... A page table is an index to the current location of a page. Access can be Swapped Page Segmentation (hierarchical) Hashed ...
Solaris System Management - Understanding System Concepts -
... – Bourne – located in /bin/sh, uses $ prompt – C – located in /bin/csh, uses a % prompt – Korn – best of both, located in /bin/ksh, uses $ prompt va-scan ...
... – Bourne – located in /bin/sh, uses $ prompt – C – located in /bin/csh, uses a % prompt – Korn – best of both, located in /bin/ksh, uses $ prompt va-scan ...
Malware - UTK-EECS
... A worm is a piece of malware that, like a virus, replicates itself to spread to other systems. The difference between a worm and a virus is that a worm doesn’t need to inject into an existing program to be executed. Worms can have payloads, such as installing backdoors to create zombie machines for ...
... A worm is a piece of malware that, like a virus, replicates itself to spread to other systems. The difference between a worm and a virus is that a worm doesn’t need to inject into an existing program to be executed. Worms can have payloads, such as installing backdoors to create zombie machines for ...
The Evolution of the Unix Time-sharing System
... machine such as we suggested might lead on the one hand to yet another Multics, or on the other, if we produced something useful, to yet another Comp Center for them to be responsible for. Besides the financial agitations that took place in 1969, there was technical work also. Thompson, R. H. Canada ...
... machine such as we suggested might lead on the one hand to yet another Multics, or on the other, if we produced something useful, to yet another Comp Center for them to be responsible for. Besides the financial agitations that took place in 1969, there was technical work also. Thompson, R. H. Canada ...
The Evolution of the Unix Time
... Thus, during 1969, we began trying to find an alternative to Multics. The search took several forms. Throughout 1969 we (mainly Ossanna, Thompson, Ritchie) lobbied intensively for the purchase of a medium-scale machine for which we promised to write an operating system; the machines we suggested wer ...
... Thus, during 1969, we began trying to find an alternative to Multics. The search took several forms. Throughout 1969 we (mainly Ossanna, Thompson, Ritchie) lobbied intensively for the purchase of a medium-scale machine for which we promised to write an operating system; the machines we suggested wer ...
Here is the Original File
... AIX was designed for the IBM 6150 RT and was initially used on the IBM RS/6000, POWER and PowerPC-based systems, IBM System I, System/370 mainframes, PS/2 personal computers, and the Apple Network Server. AIX is one of five operating system that have versions certified to The Open Group's UNIX 03 st ...
... AIX was designed for the IBM 6150 RT and was initially used on the IBM RS/6000, POWER and PowerPC-based systems, IBM System I, System/370 mainframes, PS/2 personal computers, and the Apple Network Server. AIX is one of five operating system that have versions certified to The Open Group's UNIX 03 st ...
CS 414/415 Systems Programming and Operating Systems
... • Windows NT/XP: 10 years, 1000s of people, … ...
... • Windows NT/XP: 10 years, 1000s of people, … ...
Junior Enlisted - Cyber Security
... Trained 150 System Administrators and Users in their roles and responsibilities to ensure network security to prevent spillages, malicious code, and loss of services ...
... Trained 150 System Administrators and Users in their roles and responsibilities to ensure network security to prevent spillages, malicious code, and loss of services ...
Systems Software - Shawlands Academy
... input from the keyboard, mouse, or other input device. Background processes cannot accept interactive input from a user. For example, some word processors print files in the background, enabling you to continue editing while files are being printed. ...
... input from the keyboard, mouse, or other input device. Background processes cannot accept interactive input from a user. For example, some word processors print files in the background, enabling you to continue editing while files are being printed. ...
DISTRIBUTED OPERATING SYSTEM
... processing resources between that system's distributed processes. These policies and mechanisms support operations involving the allocation and de-allocation of processes and ports to processors, as well as provisions to run, suspend, migrate, halt, or resume execution of processes. While these dist ...
... processing resources between that system's distributed processes. These policies and mechanisms support operations involving the allocation and de-allocation of processes and ports to processors, as well as provisions to run, suspend, migrate, halt, or resume execution of processes. While these dist ...
Systems Administrator needed for DoD Griffin Cyberspace Defense
... Maintain and manage the capability to deploy correlation rule sets base boundary (aka enclave control node, ECN) to correctly identify and process system alerts in support of 33 NWS operations Provide support on customer operations by providing the capability to "omit" or filter sensor traffic and a ...
... Maintain and manage the capability to deploy correlation rule sets base boundary (aka enclave control node, ECN) to correctly identify and process system alerts in support of 33 NWS operations Provide support on customer operations by providing the capability to "omit" or filter sensor traffic and a ...
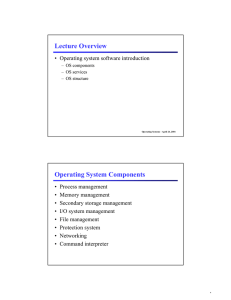
Lecture Overview Operating System Components
... – Allows for better protection since services cannot affect the rest of the operating system – Very adaptable for use in distributed systems – It is not always possible to have a clean separation between a service and the kernel – This approach adds overhead – Examples: Mach, Mac OS X, GNU Hurd ...
... – Allows for better protection since services cannot affect the rest of the operating system – Very adaptable for use in distributed systems – It is not always possible to have a clean separation between a service and the kernel – This approach adds overhead – Examples: Mach, Mac OS X, GNU Hurd ...
UNIX Operating System
... understand naming patterns for devices on Linux. Special device files are used by kernel drivers to control a device. There can be more than one special device file that maps to the same physical device. For example, in a multipath environment with four paths to the same device, four different dev ...
... understand naming patterns for devices on Linux. Special device files are used by kernel drivers to control a device. There can be more than one special device file that maps to the same physical device. For example, in a multipath environment with four paths to the same device, four different dev ...